IDHub and Entra ID Field Test: Integration and Application
Purpose of the document
The document provides a detailed guide on integrating Entra ID with IDHub using the connector onboarding wizard. It covers prerequisites, quick onboard Entra ID connector, managing user provisioning and revocation, and performing certification checks.
Who can use this
The guide on integrating Entra ID with IDHub is primarily intended for IT professionals and system administrators who are responsible for managing user access and security in organizations. These users should have a basic understanding of Microsoft Entra IDand be subscribers of IDHub. The guide is particularly useful for those looking to streamline their user provisioning and revocation processes through IDHub's features, ensuring a seamless integration with Entra ID.
What are the Prerequisites?
You would need a IDHub Subscription and tenant information before you can on-board Entra ID connector.
If you don't have an IDHub subscription, refer to Get IDHub Cloud Tenant for detailed instructions.
Quick Onboard Entra ID Connector
Entra ID Connector Details Page
- Go to sath website and at the top navigation menu go to
Product-->Identity Connectors-->Entra ID. - Click on the button
Deploy in Cloud.
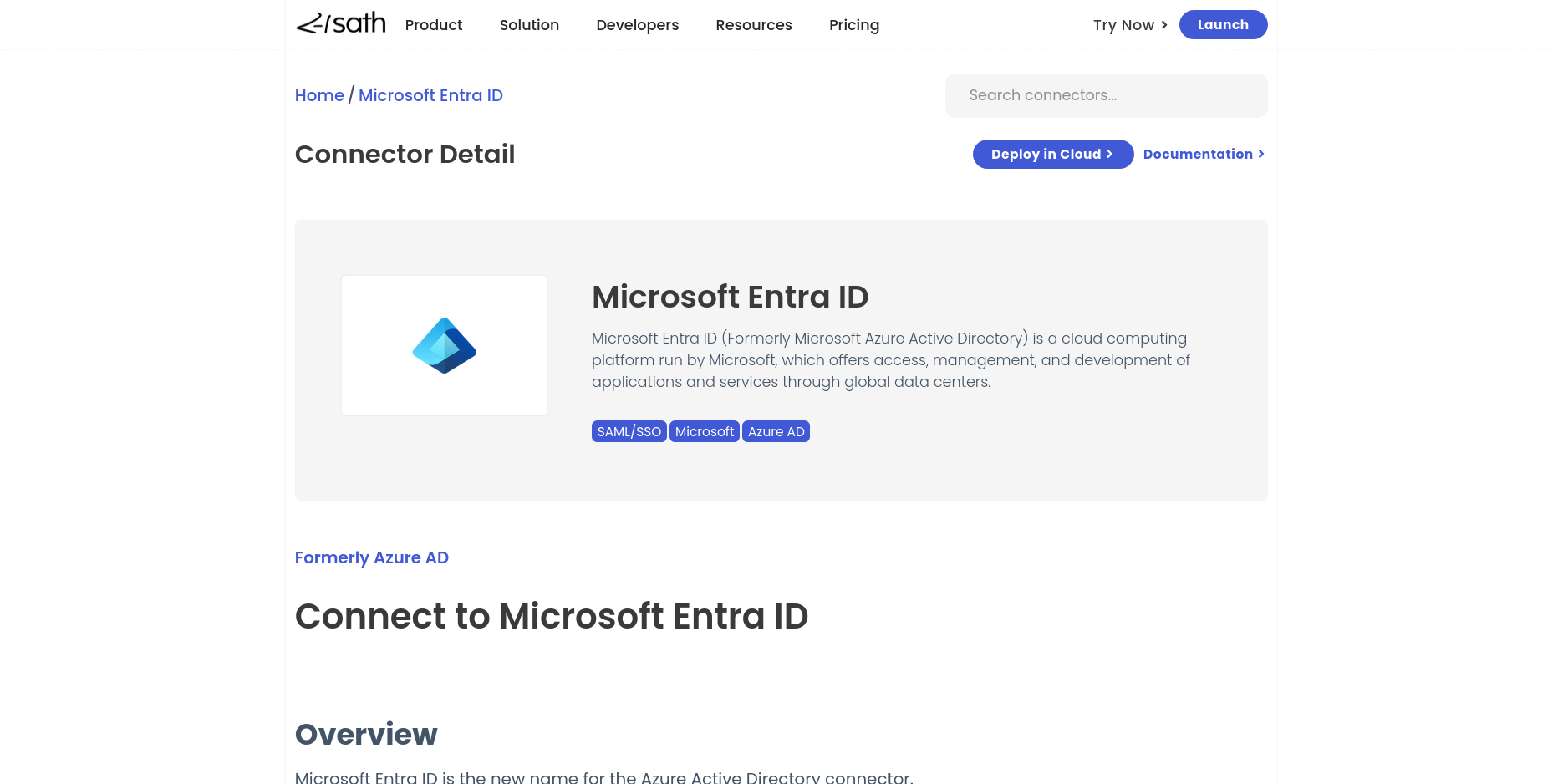
Purchase Entra ID Connector
- Under choose your connector, Microsoft Entra ID is pre-selected in the dropdown.
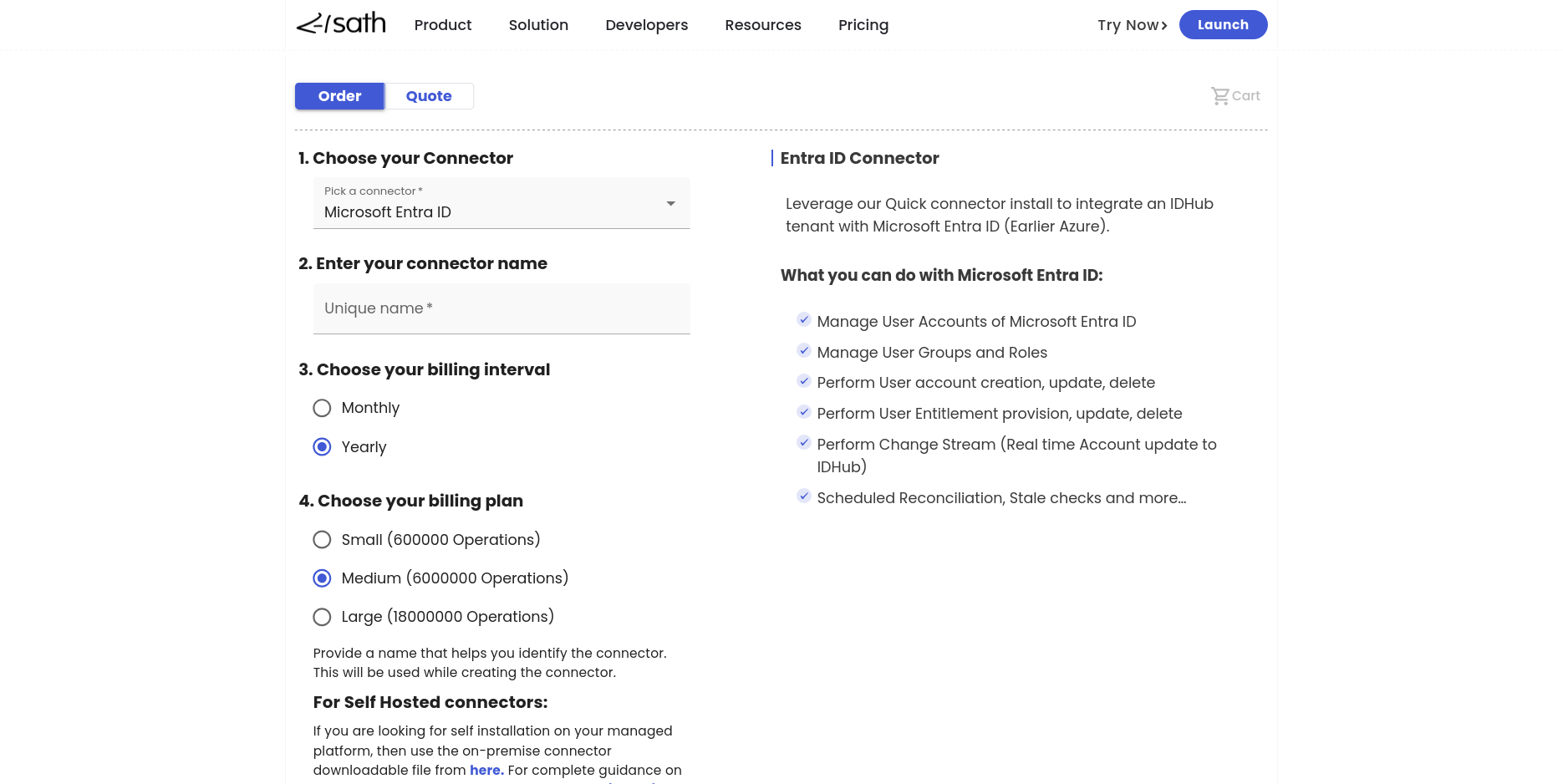
Next you have to enter the connector name. Make sure, that you provide a name which helps you to identify the connector and this connector name will be used, while onboarding the connector to IDHub.
infoConnector names can only be lowercase and alphanumeric.
Choose your billing interval. IDHub provides you two options for the billing interval. One is yearly and the other one is monthly.
Choose your billing plan. IDHub provides you small, medium and large billing plan, depending on the number of connector operations that you expect.
Next click on the button
Checkout Orderin order to proceed to checkout page.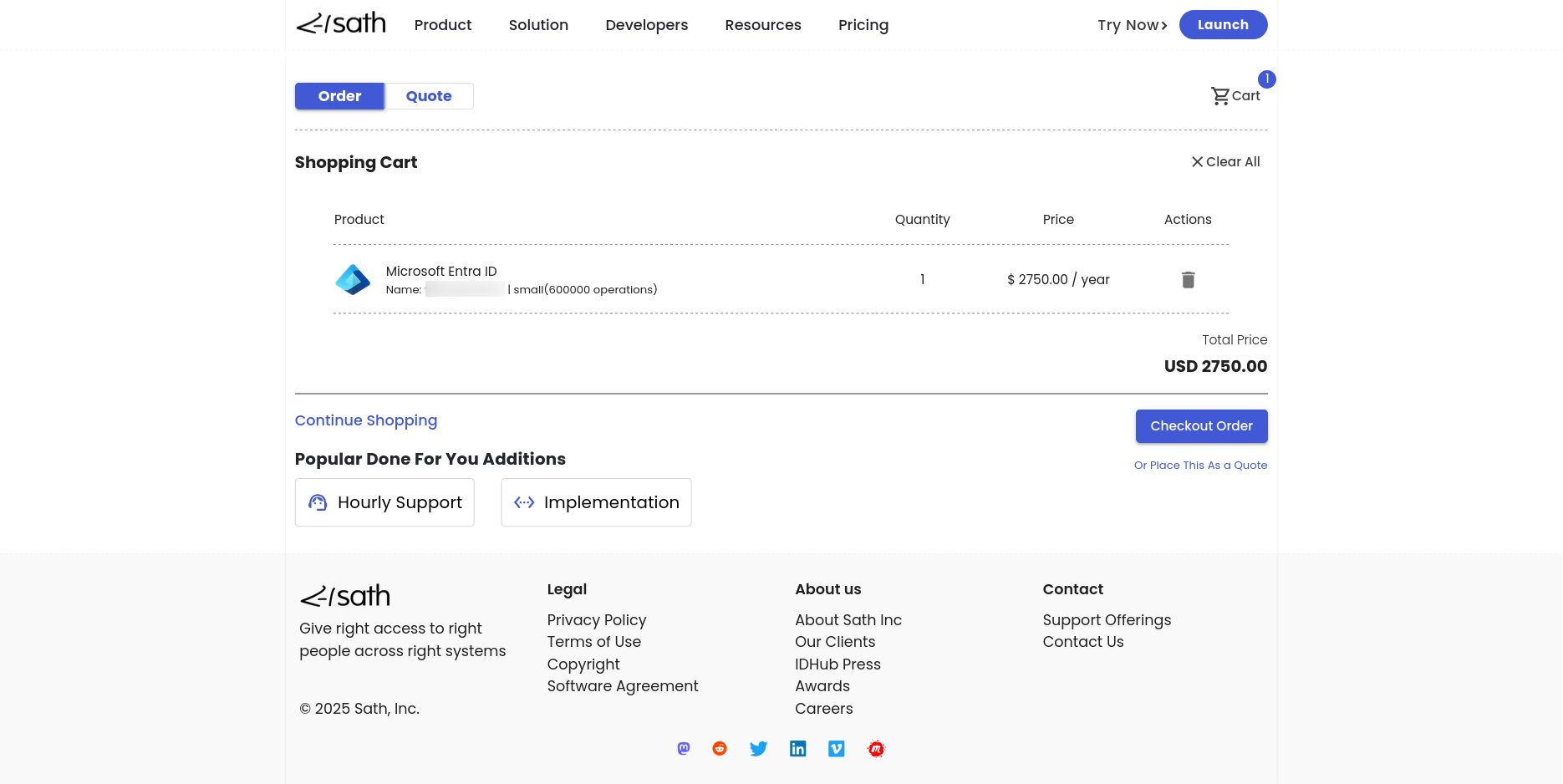
Enter contact details and other information in the checkout page and click on the button
Checkoutto complete the purchase.Click on the
Account Managementlink to go to your account management dashboard and then click onConnectorleft menu.
Installing the Connector
IDHub would start the installation of the connector. The health status would be installing as is shown in the screenshot below:
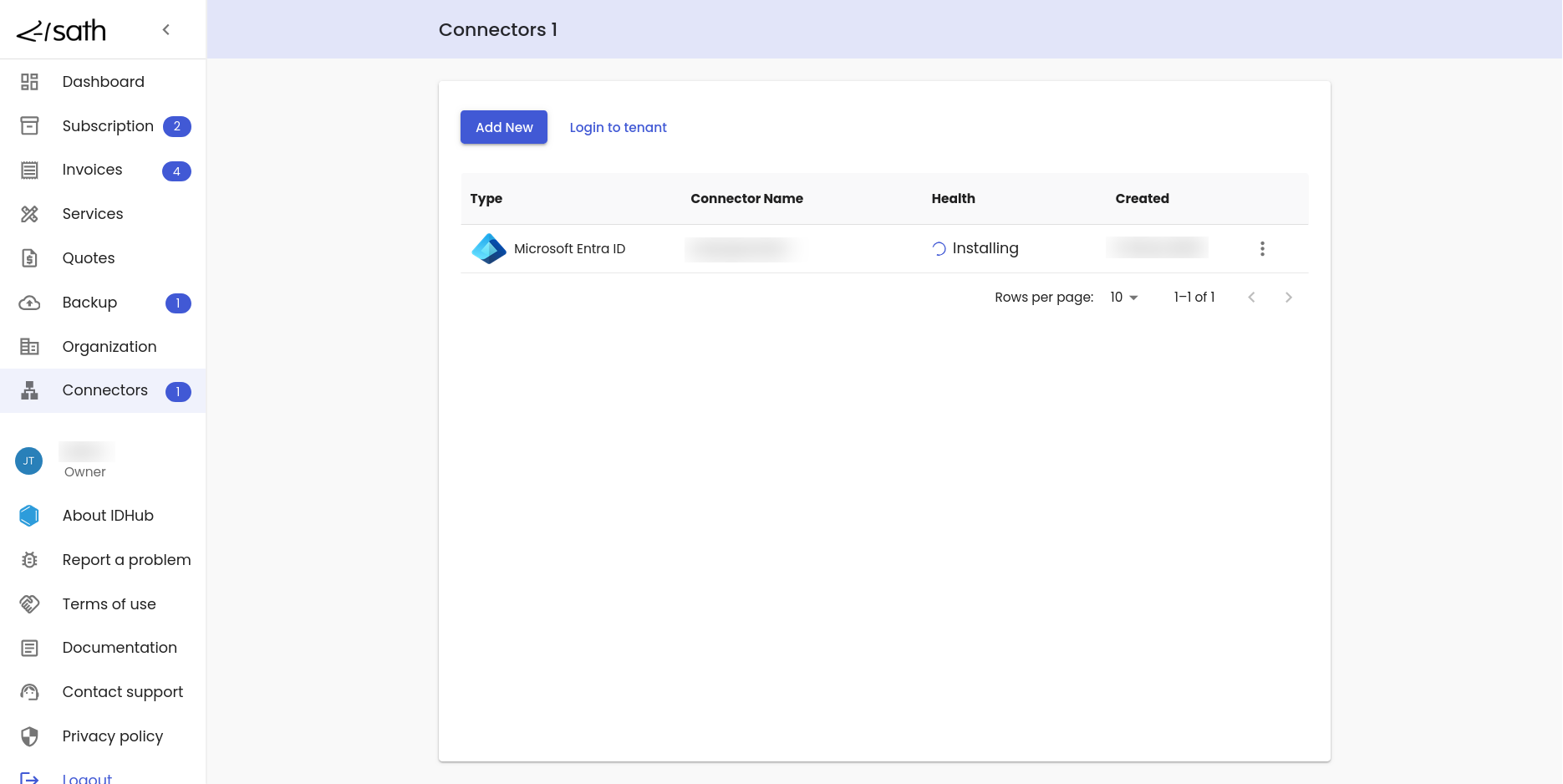
After the installation of the connector is finished, the health status of the connector would be updated to not configured

Connector Manager
- Click on the 3 dots menu for the connector and then click on the
ManagerMenu.
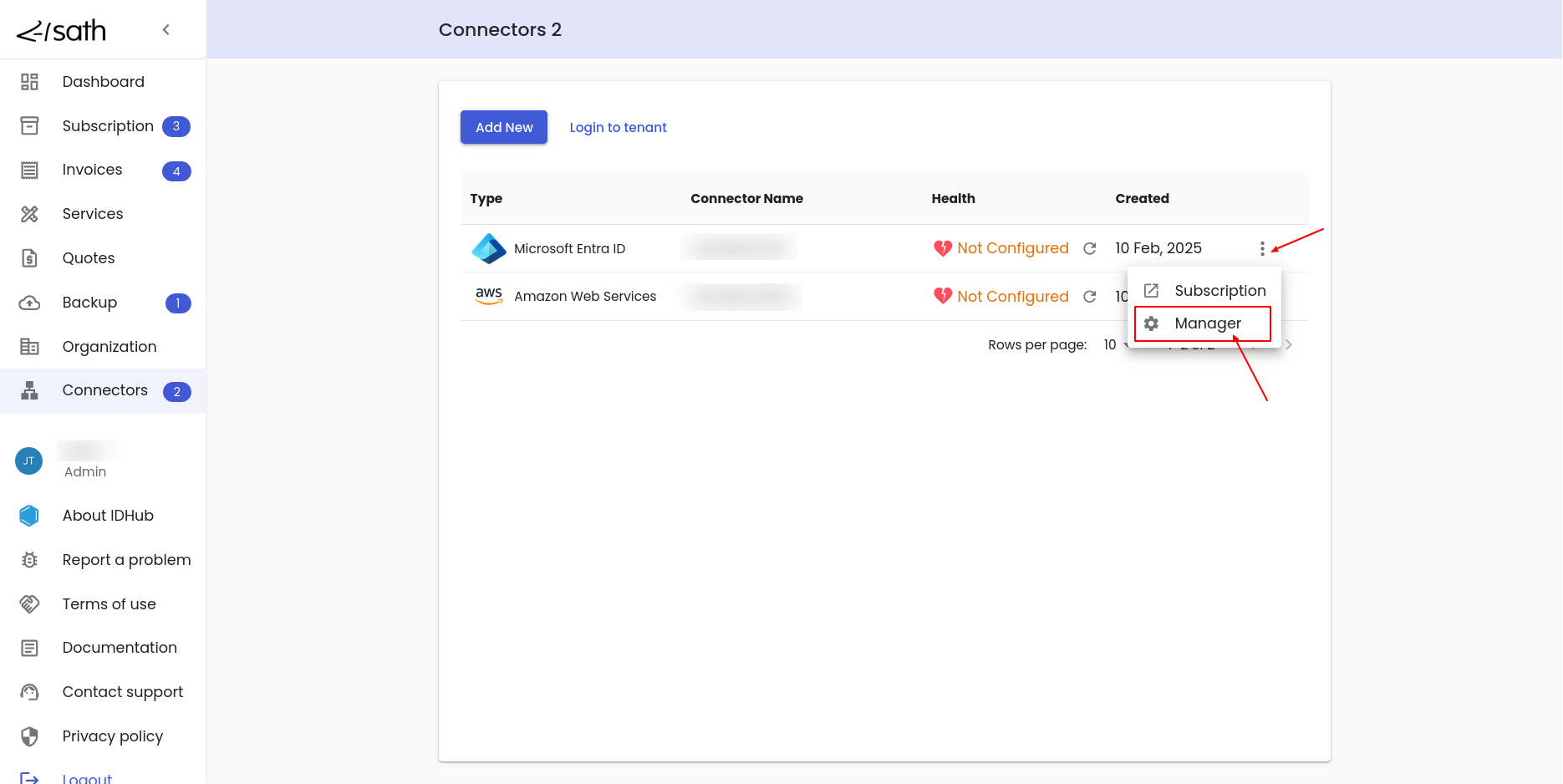
- You will be taken to the IDHub Connector manager page

- Enter the application URL and the tenant name. The application URL is the IDHub application URL for example:
https://app.sath.com - Click on the REGISTER button in order to proceed further.
Tenant Login and verification
Next you will be redirected to the tenant login page. (If you are not alerady logged into your IDHub tenant). Enter your IDHub tenant login credentials to proceed further.
Connector Information page
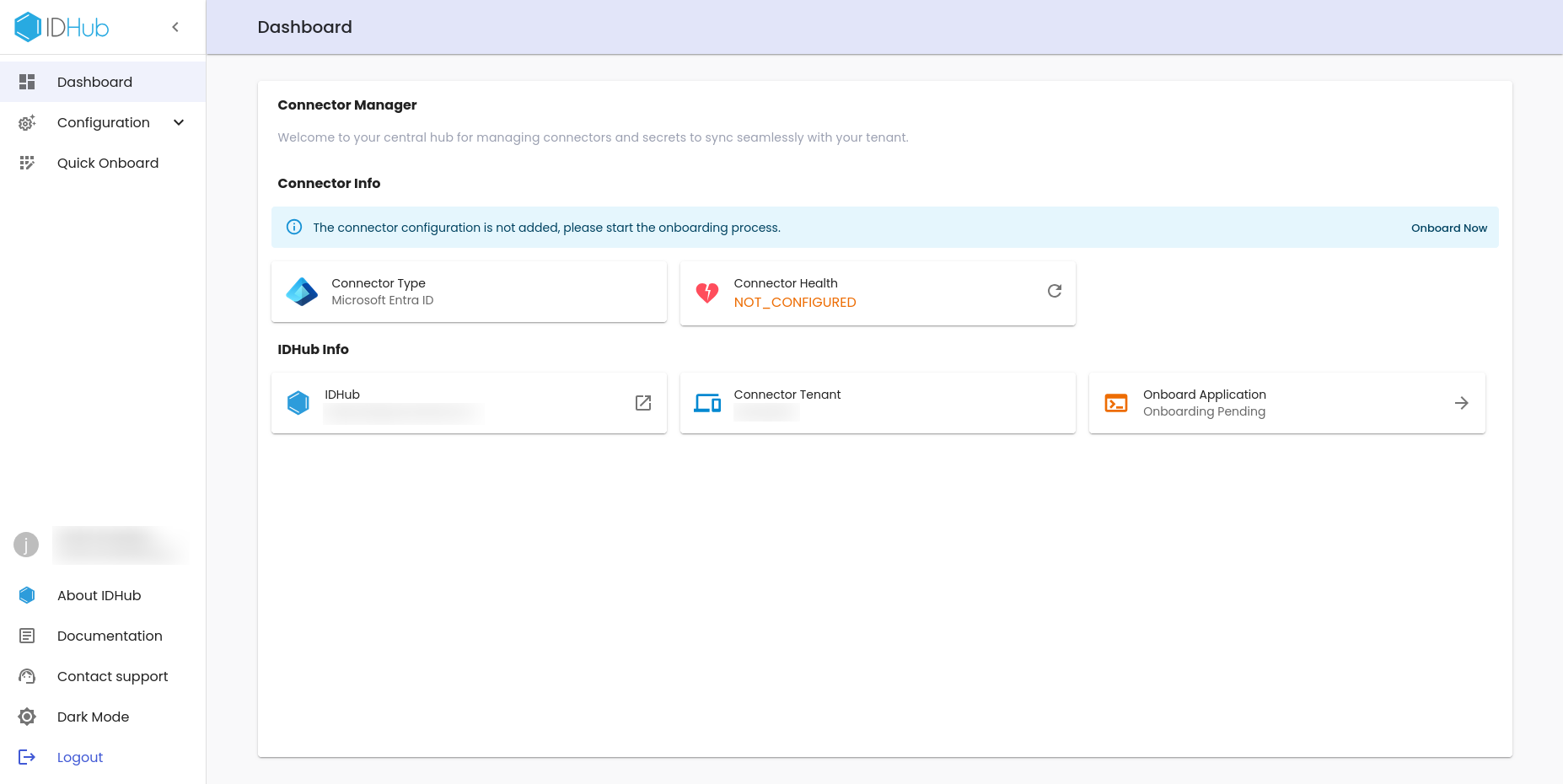 This page shows the following information:
This page shows the following information:
- Connector type
- Connector health
- IDHub info
- Application URL
- Connector tenant
- Onboard Application
Now click on the Onboard now link to proceed further
Enter the Application Credentials
For EntraID connector you have to enter the Application credentials are as follows:
- Client ID
- Client Secret
- Tenant ID
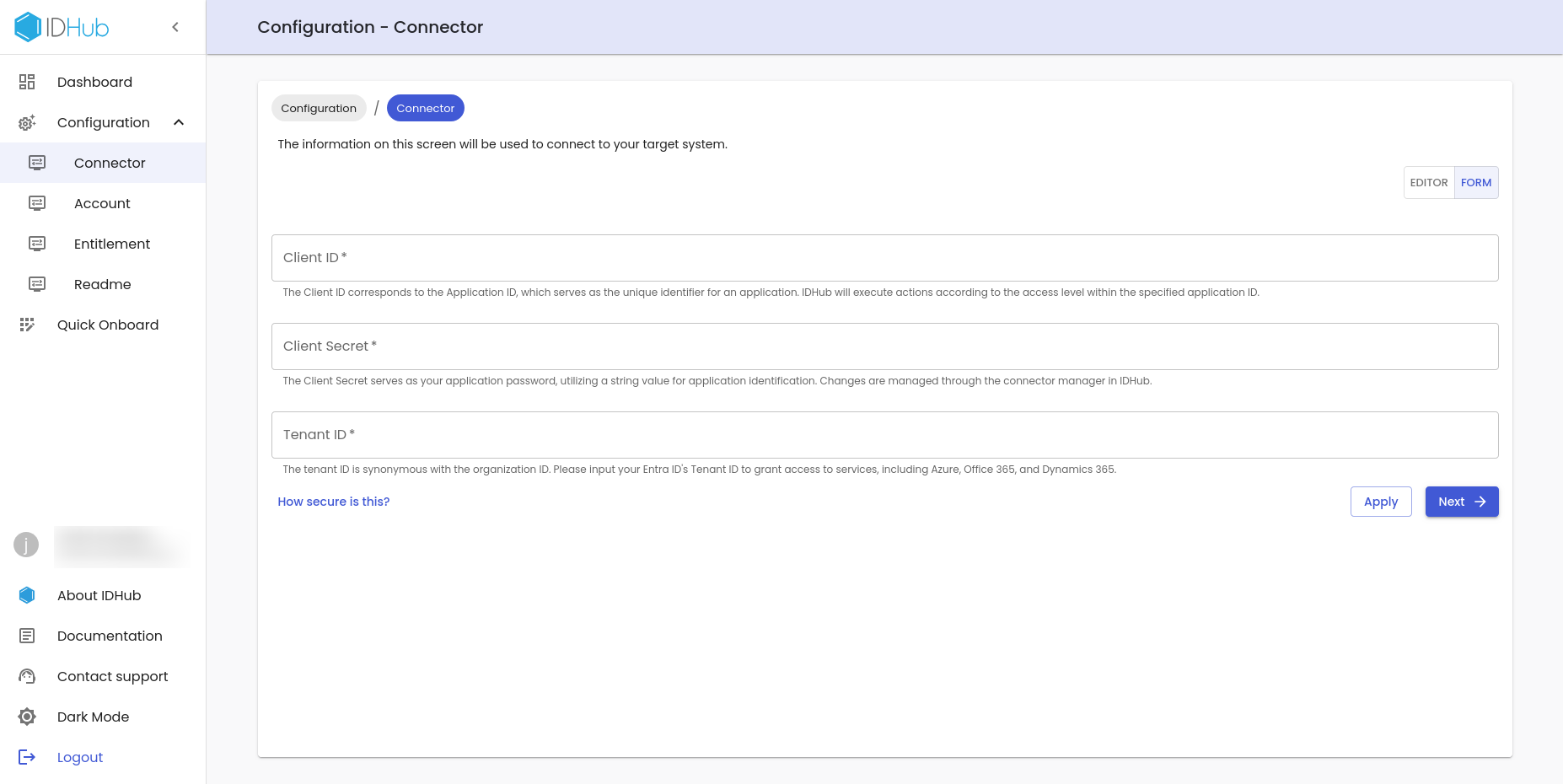
Click on the Apply and Next button to proceed further.
Now you will be taken to the Account JSON editor page as is shown below:
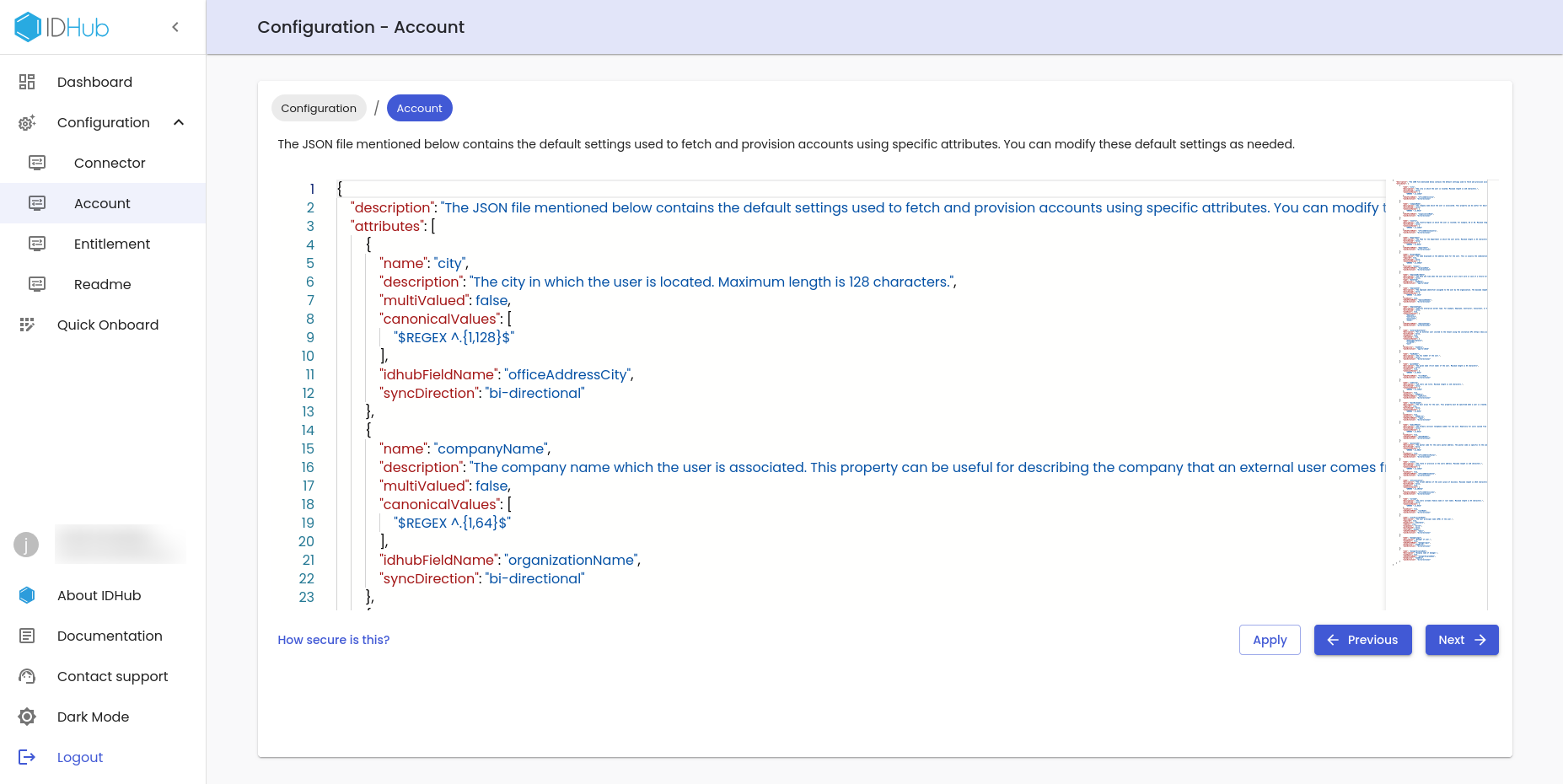
This page contains the default configuration used to fetch and provision accounts using specific attributes. You can modify these default settings as needed.
Click on the Apply and Next button to proceed further to the Entitlement JSON editor page.
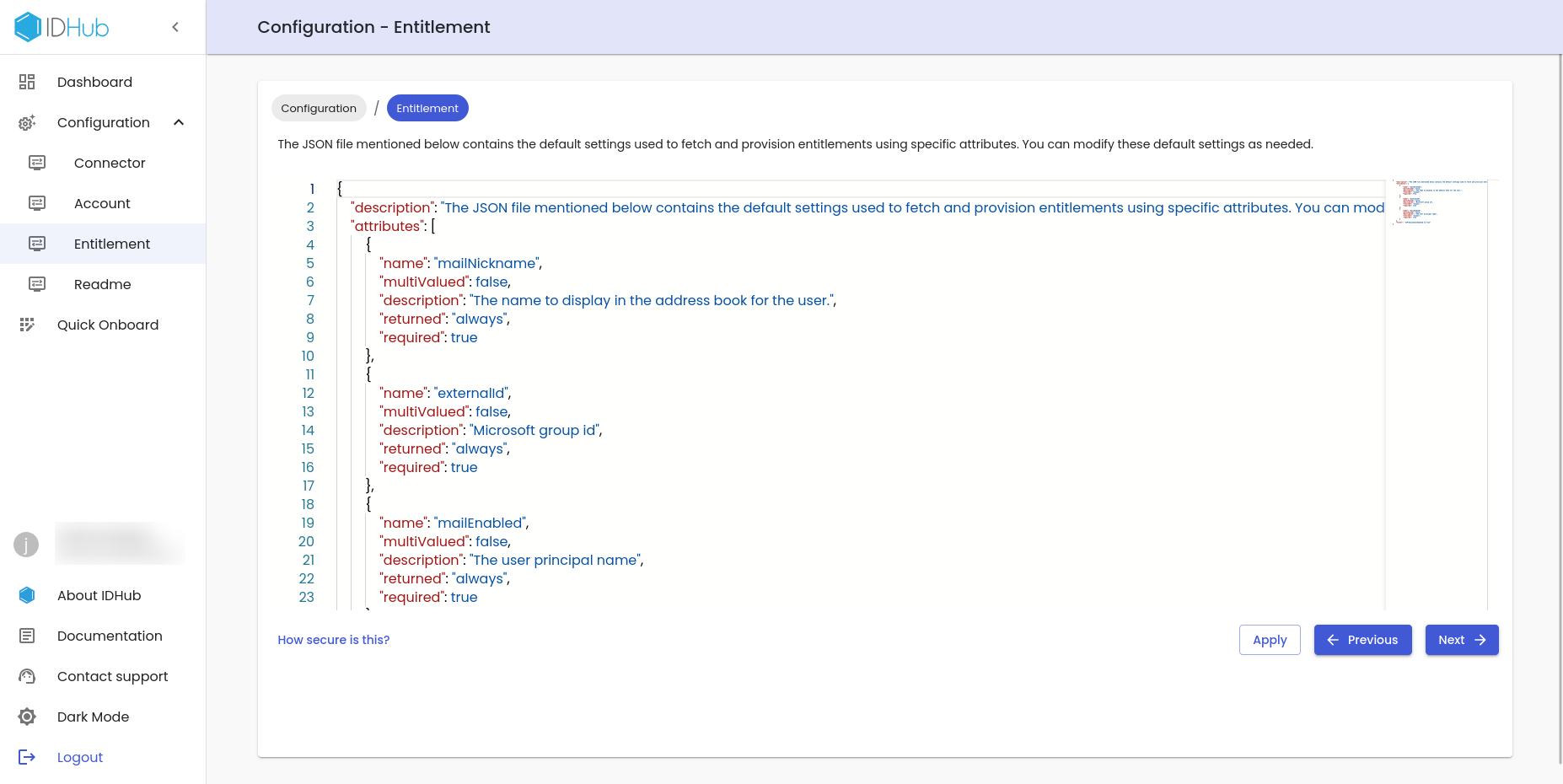
This page contains the default settings used to fetch and provision entitlements using specific attributes. You can modify these default settings as needed.
Click on the Apply and Next button to proceed further.
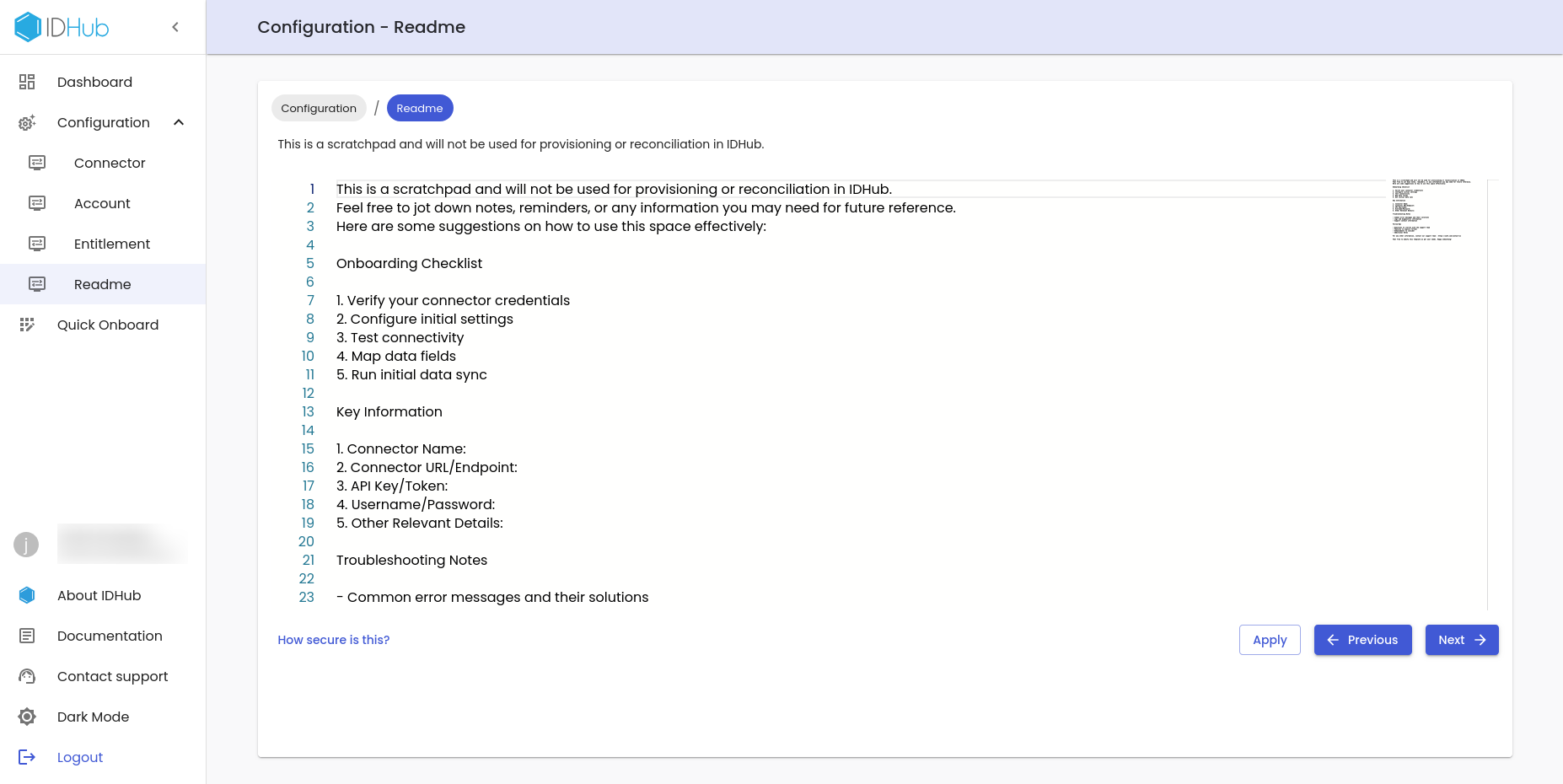 This page functions as the scratch pad for the connector configuration. Here you can enter any notes, reminders, or any information you may need for future reference for the connector configuration.
This page functions as the scratch pad for the connector configuration. Here you can enter any notes, reminders, or any information you may need for future reference for the connector configuration.
Information entered in this page, will not be used for provisioning or reconciliation in IDHub.
Now click on the next button and then click on the ONBOARD button.
Enter Application Name
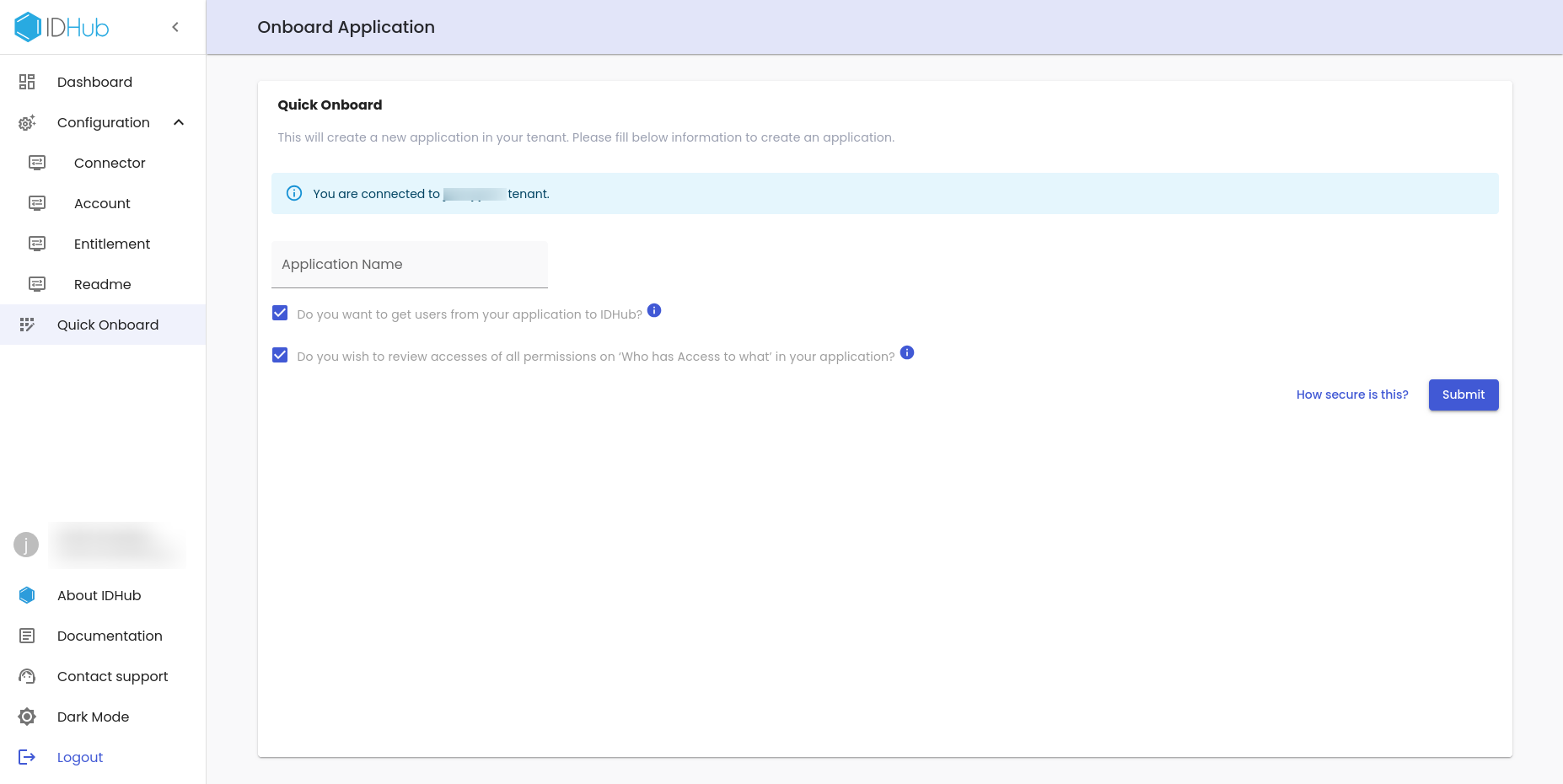 In this screen enter the name of the application. There are two additional checkboxes which are as follows:
In this screen enter the name of the application. There are two additional checkboxes which are as follows:
- Do you want to get users from your application to IDHub
- If checked, then the Entra ID is created as a "Trusted App" in IDHub. All users with unique email addresses in the Entra ID instance would be added to IDHub.
- Do you want to review accesses of all permissions on "Who has access to what" in your application
- This will create a certificate definition for you in your IDHub tenant. This you can later modify for performing access reviews on your Entra ID accounts.
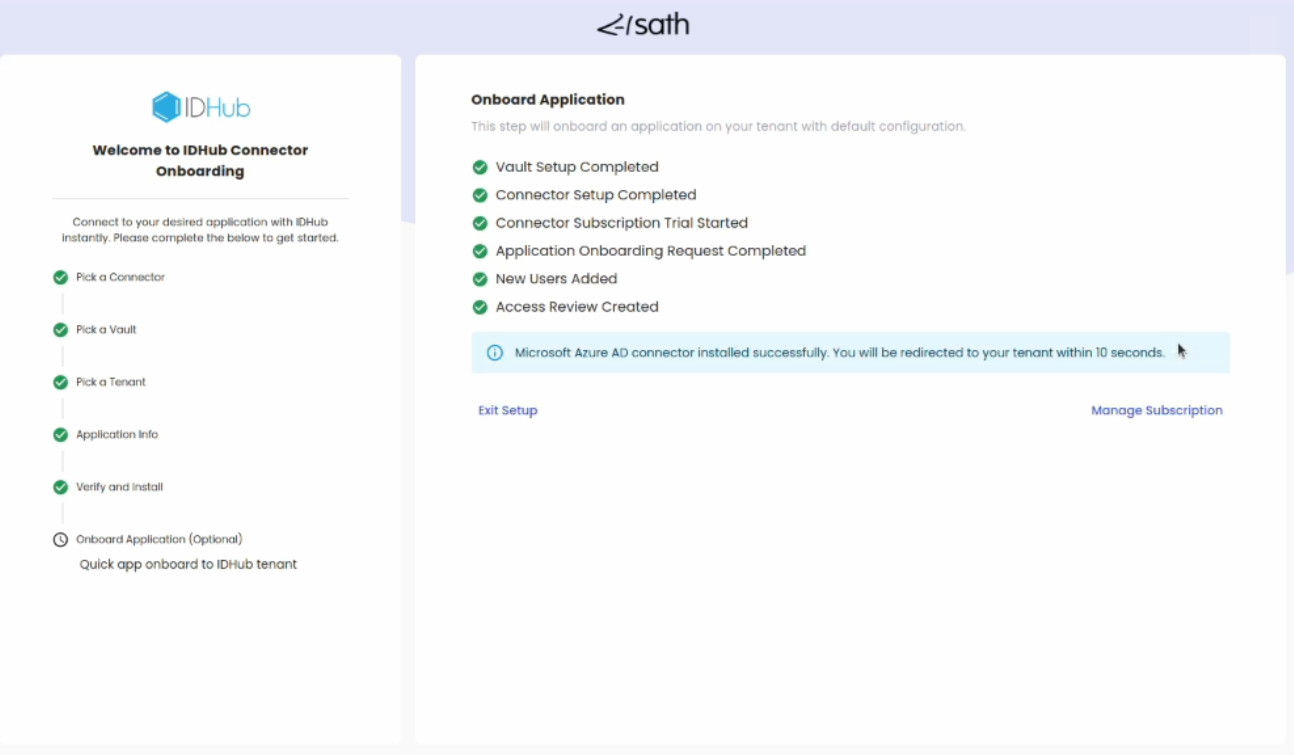
Setup will take some time and display the confirmation message. At this stage, Entra ID is successfully installed and optionally your Entra ID application is also onboarded to IDHub.
Verify the onboarded Entra ID Application
Now, log into your IDHub tenant and then click on the Manage catalog. You will see the Entra ID application. Click on it. You can see the details of the application

Click on the attributes tab and it will show you the different attributes of the application along with it’s sync directions.

Click on the Entitlements tab and it will show you the different Entra ID groups as entitlements.
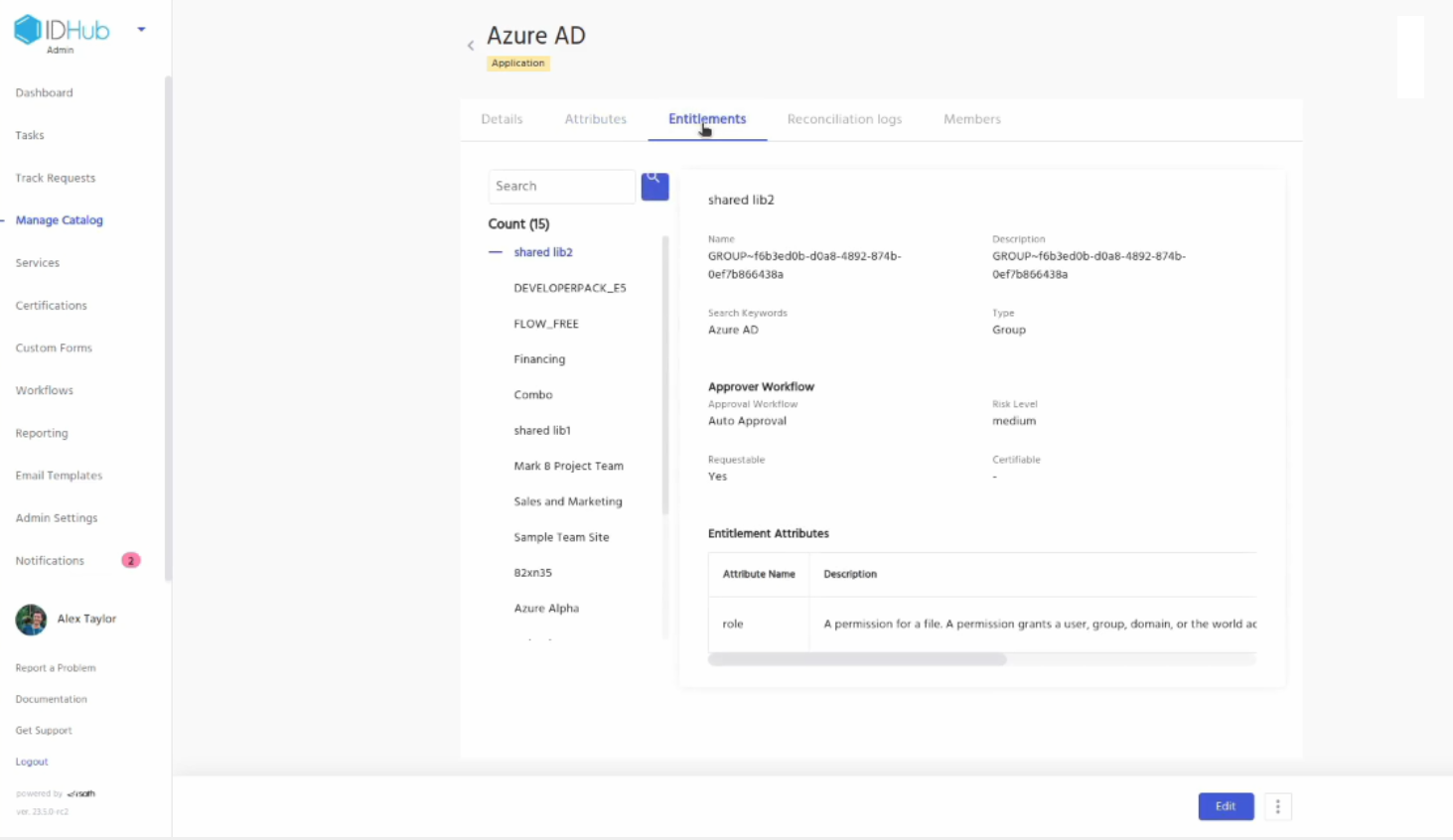
Click on the Reconciliation logs and it will display the reconciliations that IDHub has made for the application
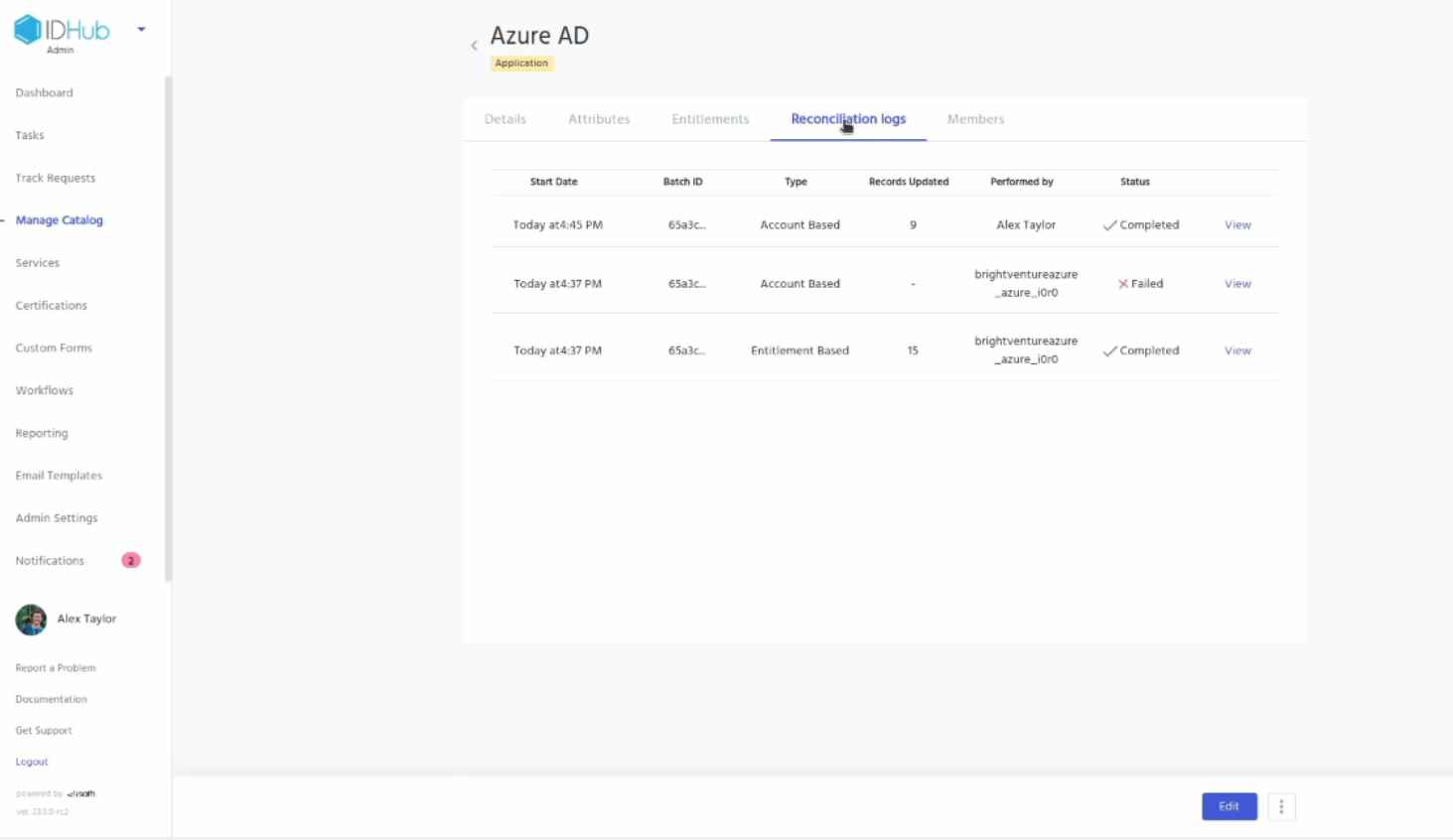
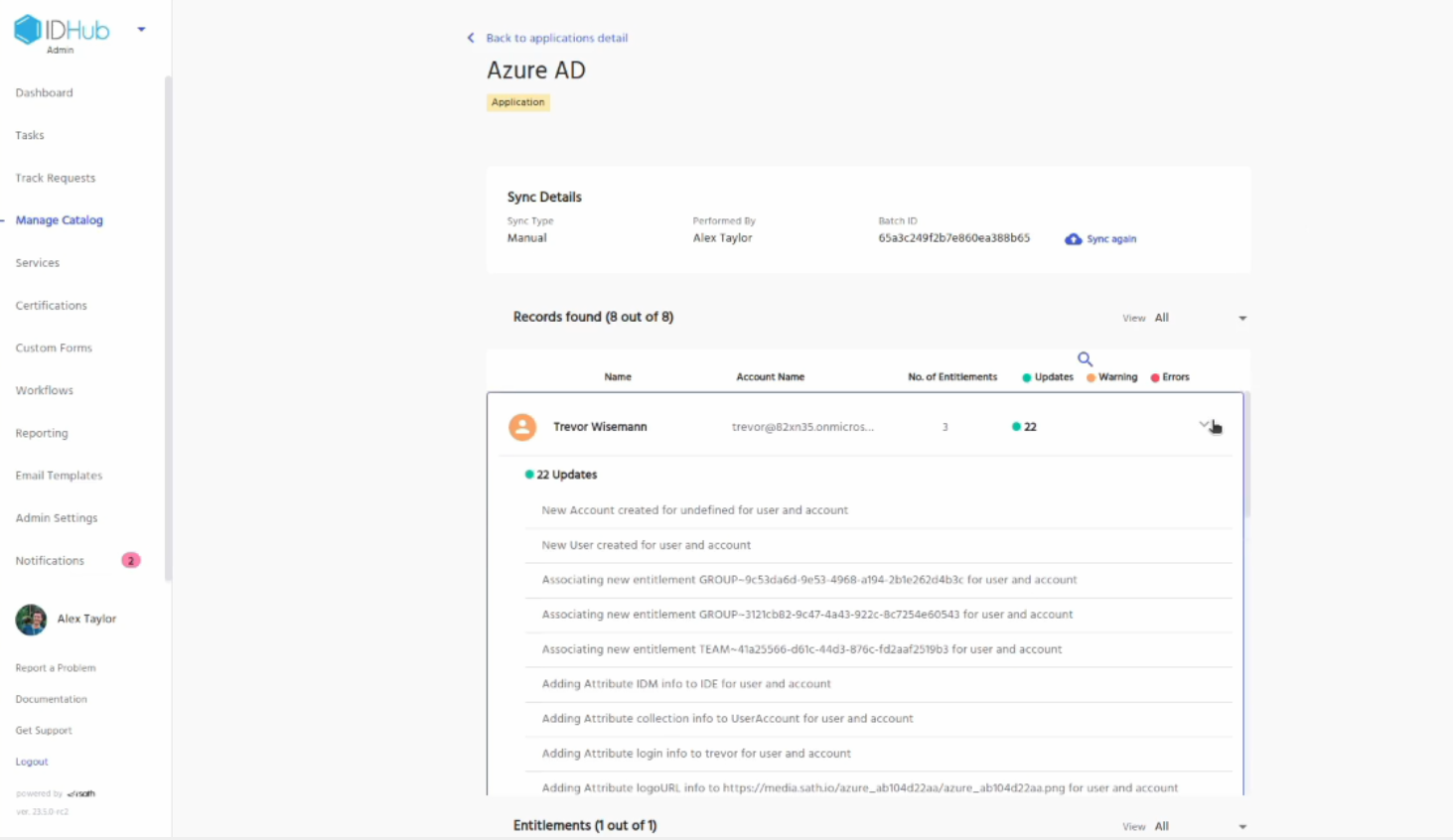
Click on the view link in one of the logs. You will be redirected to the details of the log where you can see the users or entitlements that have been synced.

You can also click on the down arrow for each account and see the updates that have been made for each one of them.
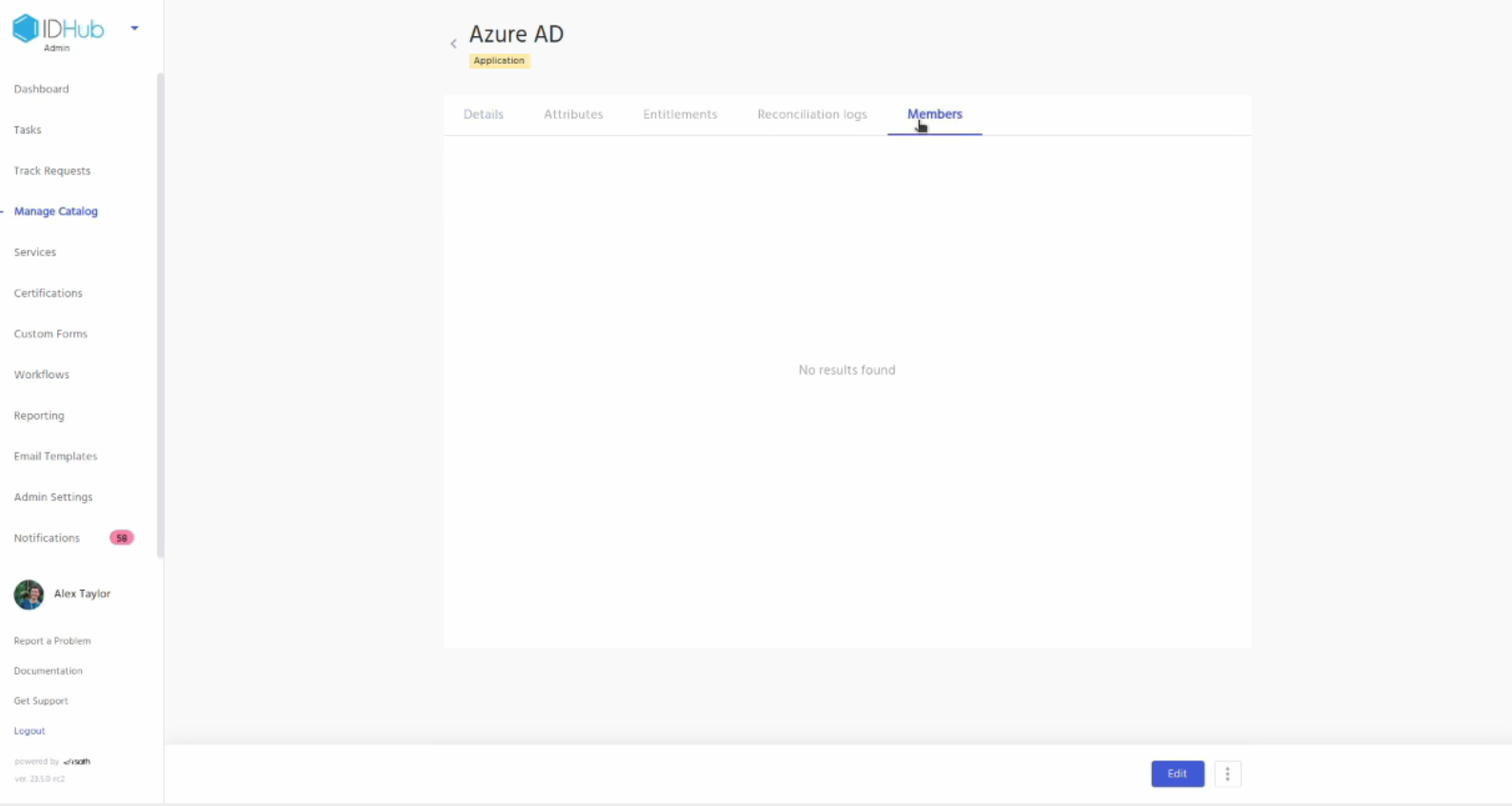
Click on the members tab, Here you will see the users who have access to the application.
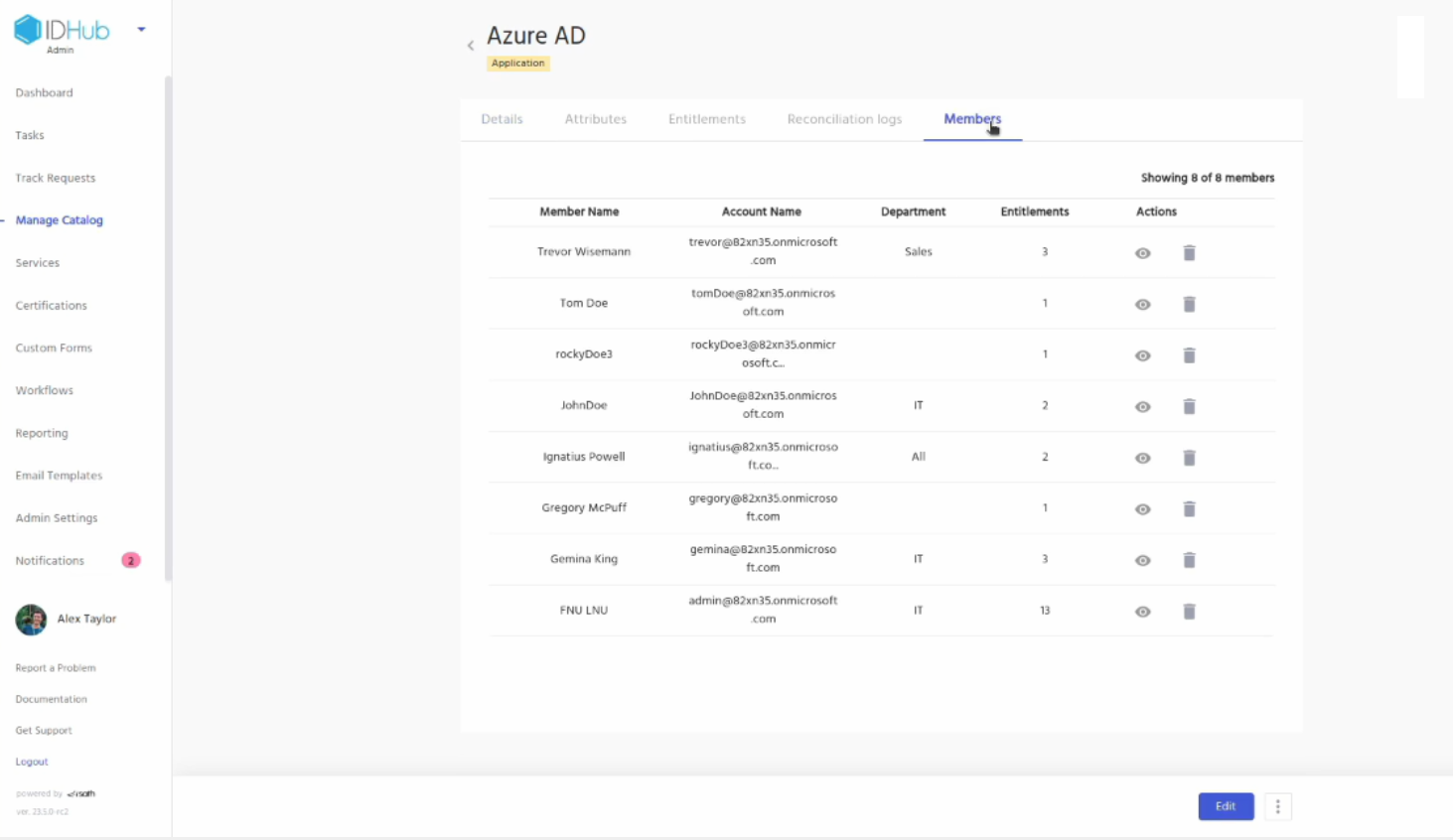
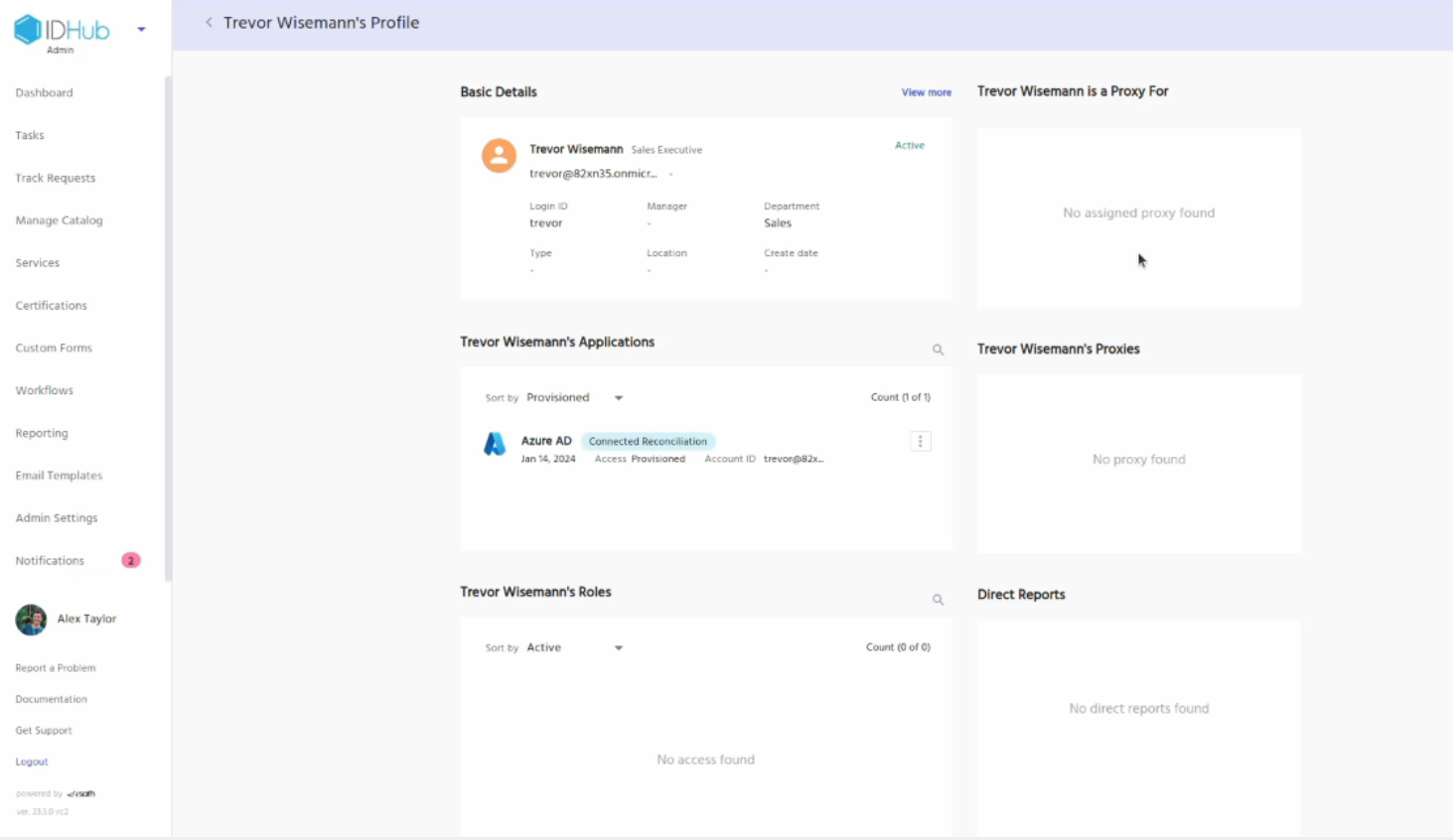
Click on the view profile button for one of them user, This will take you to the user profile page. Here you can see that the Entra ID application is provisioned for the user.
Birth-right role And Auto Provisioning
Creating a Birth-right Role For User
Now let’s create a role with a condition that all users who have a department is sales can automatically get Entra ID provisioned for them. This is particularly important if you have a scenario where users of a certain department would like to automatically get access to Entra ID.
For creating a role, goto Manage Catalog and then click on the Create Role button. You will get a screen as shown below:

In the first screen enter the required basic details of the role and then click on the next button. In the next screen add a condition, that department is sales as shown below.
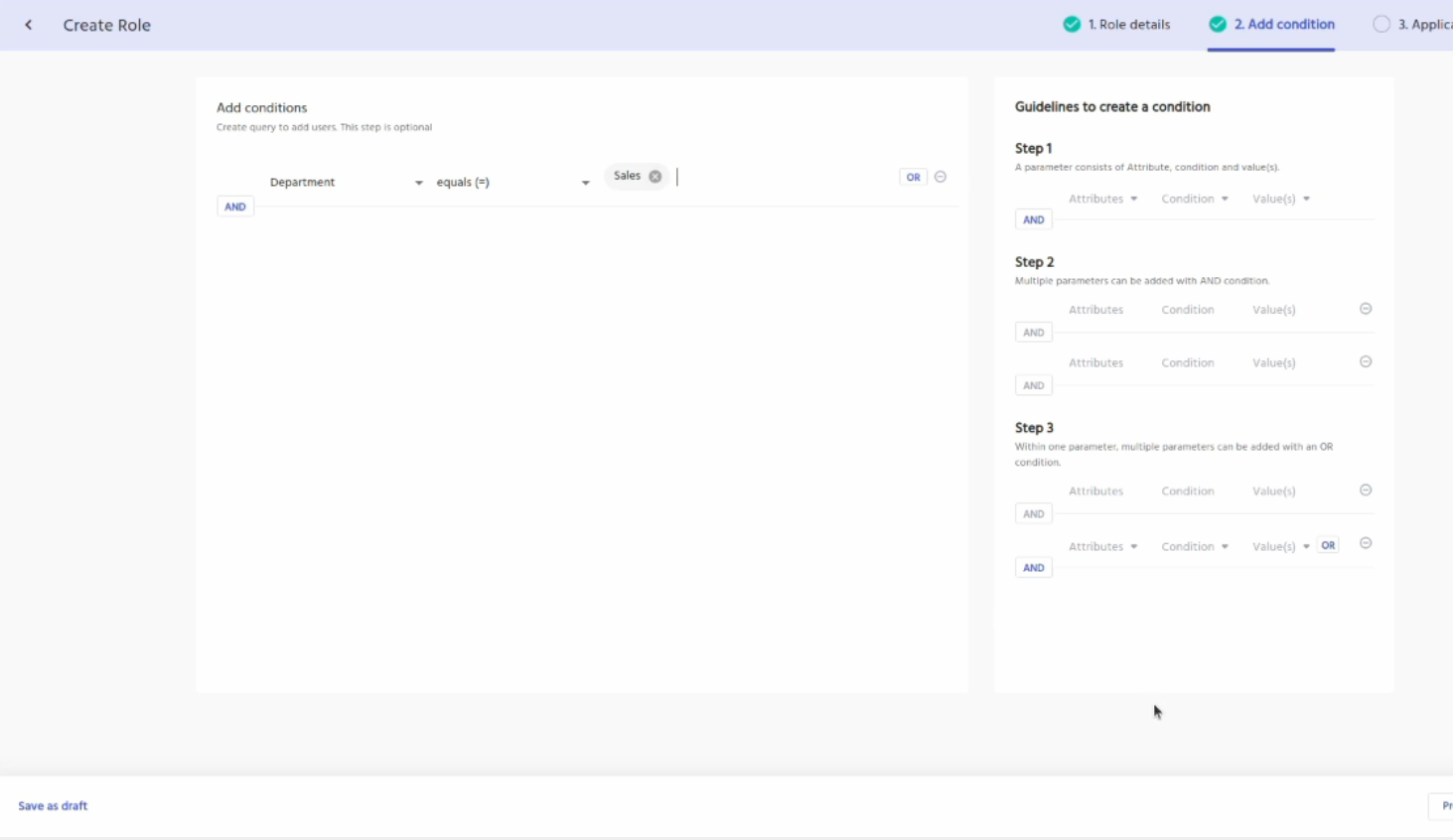
Next, Add the application Entra ID by clicking on the plus button. Click on the down arrow and you will see the entitlements. Optionally you can add entitlements to the role as well. For entitlements, you might have to specify whether the entitlement attribute is of a member type or owner type or both.

Click on the submit button. Enter a reason for creating the role.
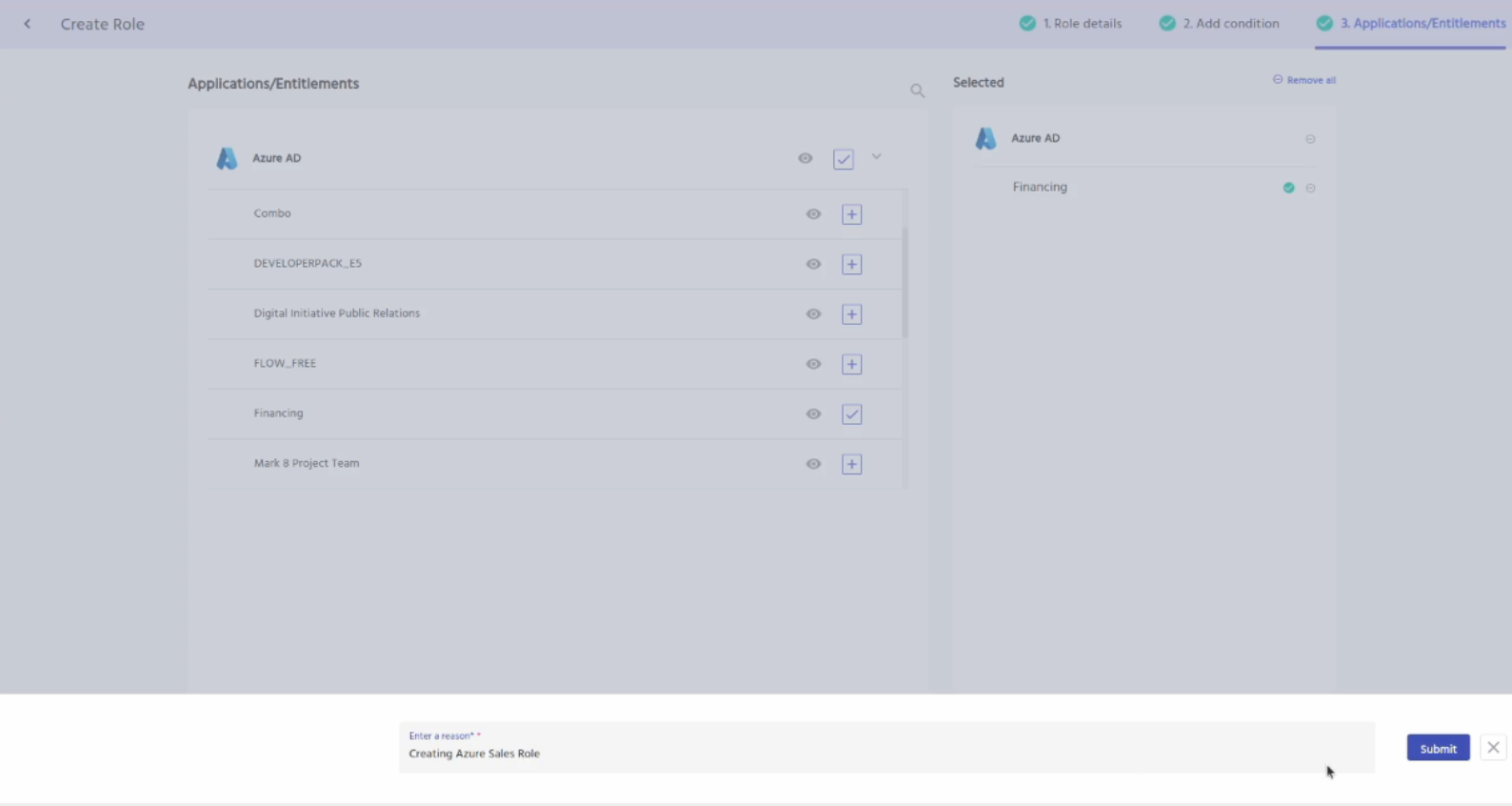
Click on the submit button again. Goto tasks, claim and approve the role.
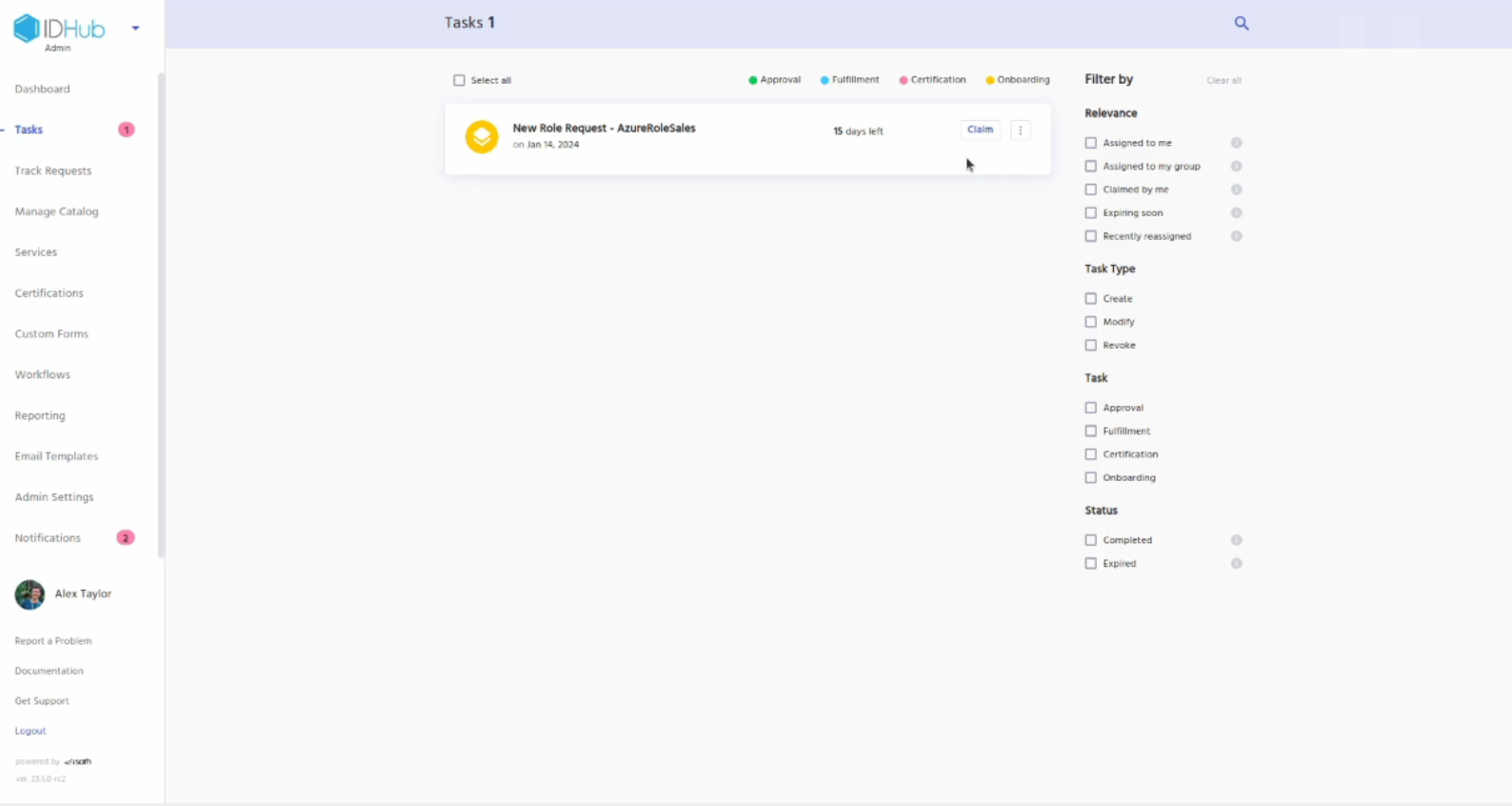
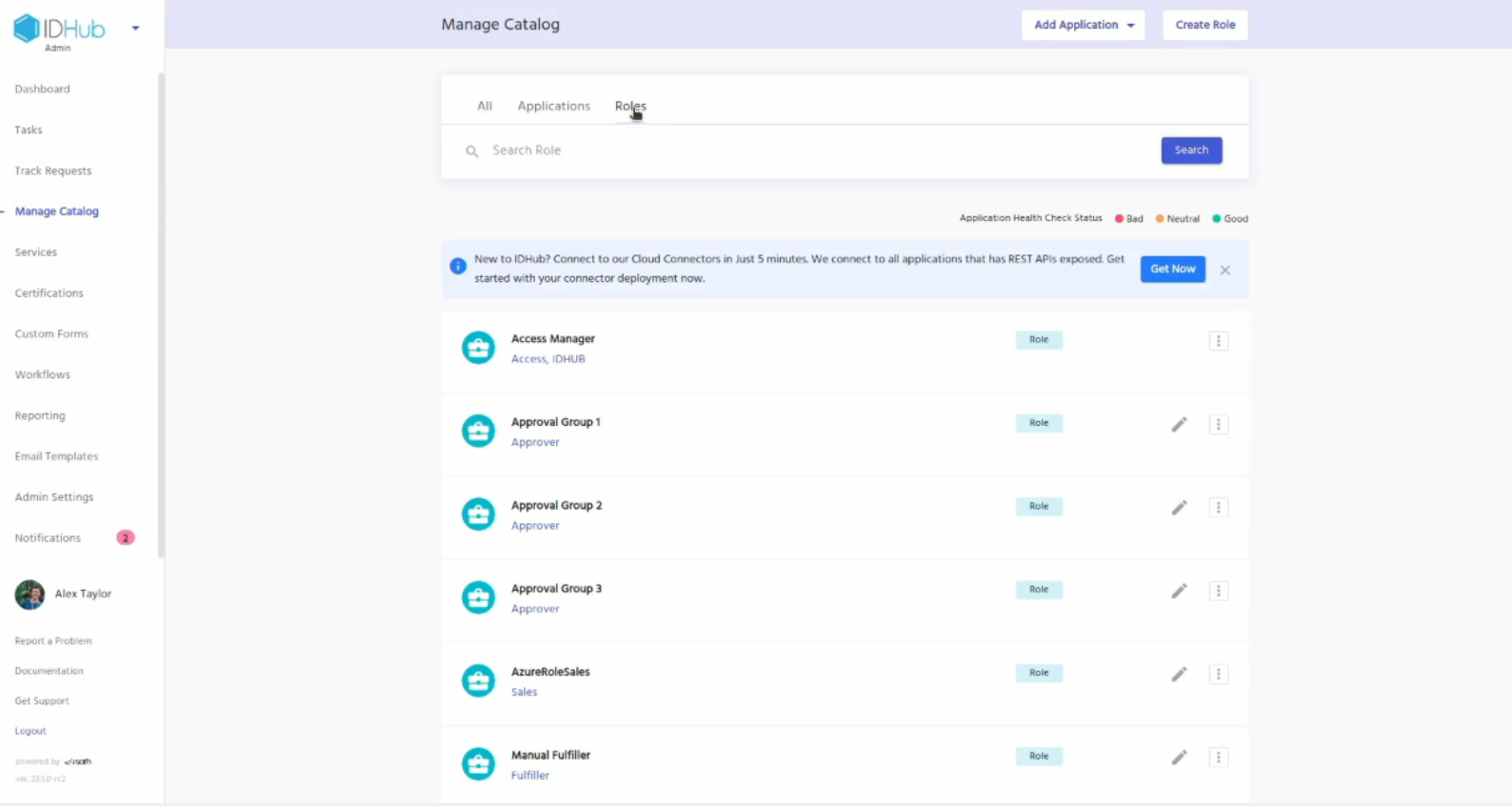
Goto manage catalog and click on the roles tab. There you will see the role that you just created.
Creating a New User whose attributes matches the role condition
Now let’s create a new user whose department is sales to check whether that user automatically provisioned Entra ID application or not. For creating a new user goto the IDHub user app, click on the search catalog, click on the service requests tab and then click on the new user request. Add it to the cart and click on the proceed button and you will be taken to the screen as shown below:
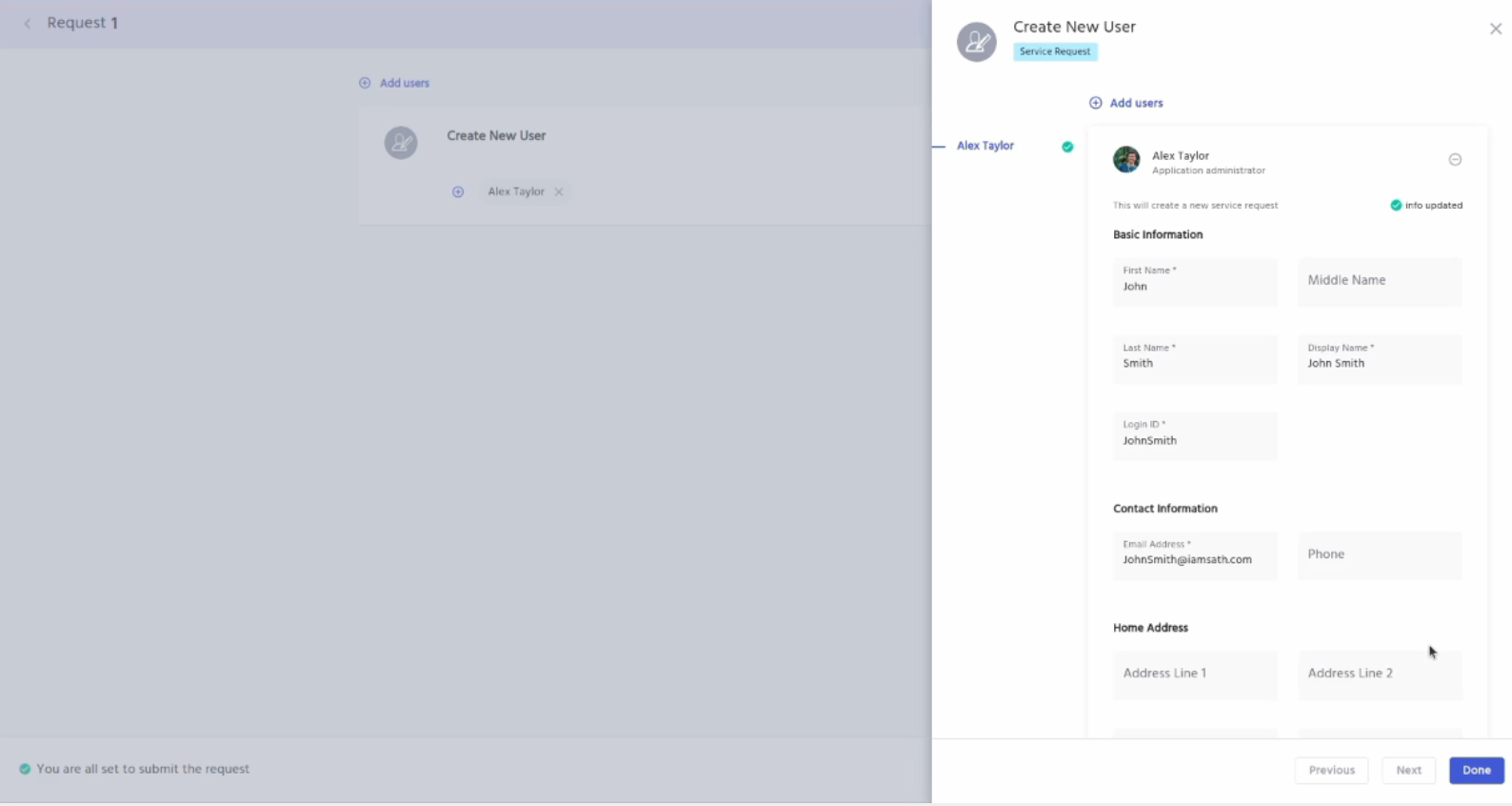
Here enter the required information to create the new user. Make sure that the email address of the new user should have the same domain name as your Entra ID instance. Click on the DONE button. Click on the continue button.
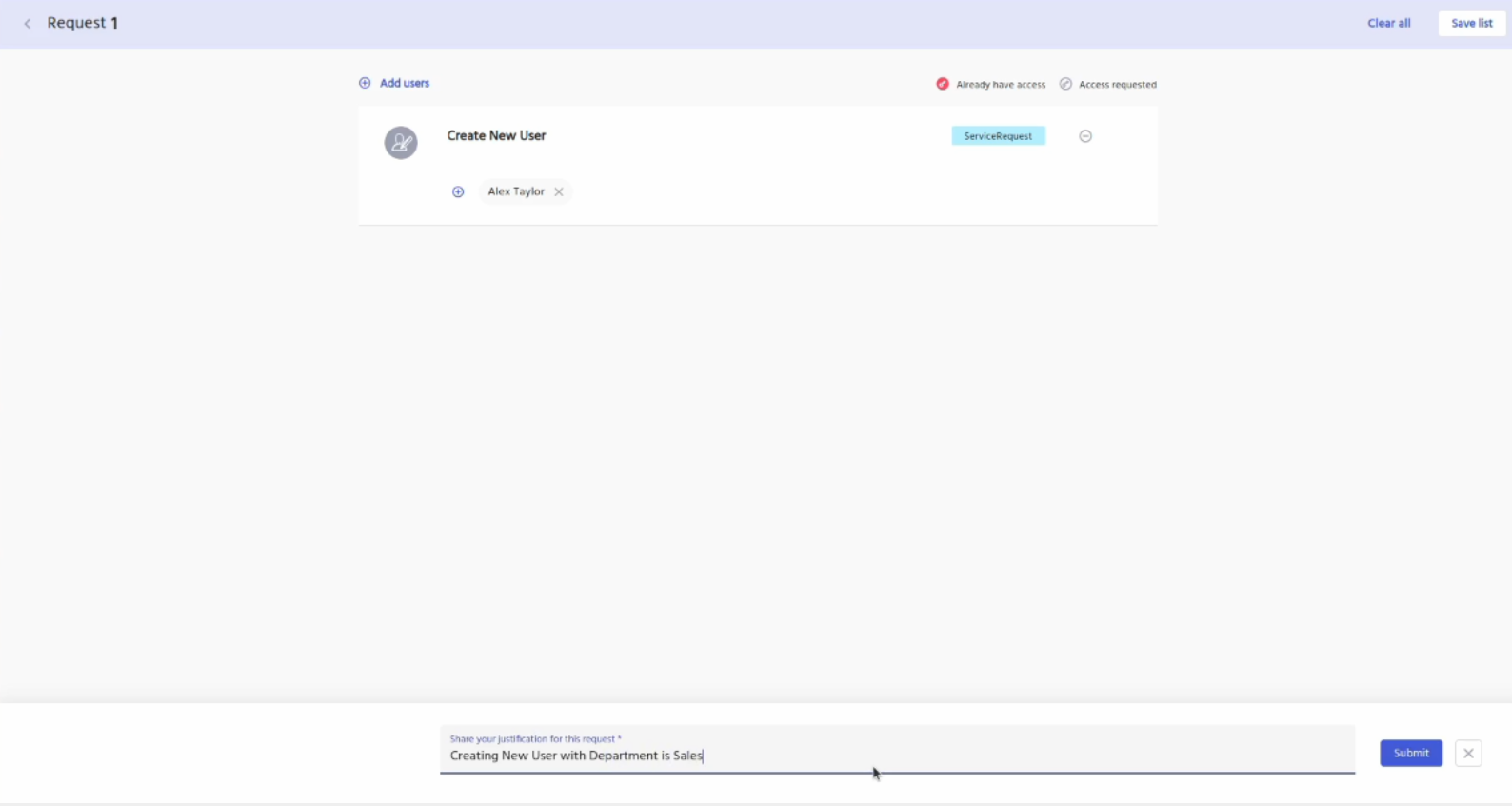
Enter a justification for the request and then click on the submit button.
Now, Goto tasks and then claim and approve the request.
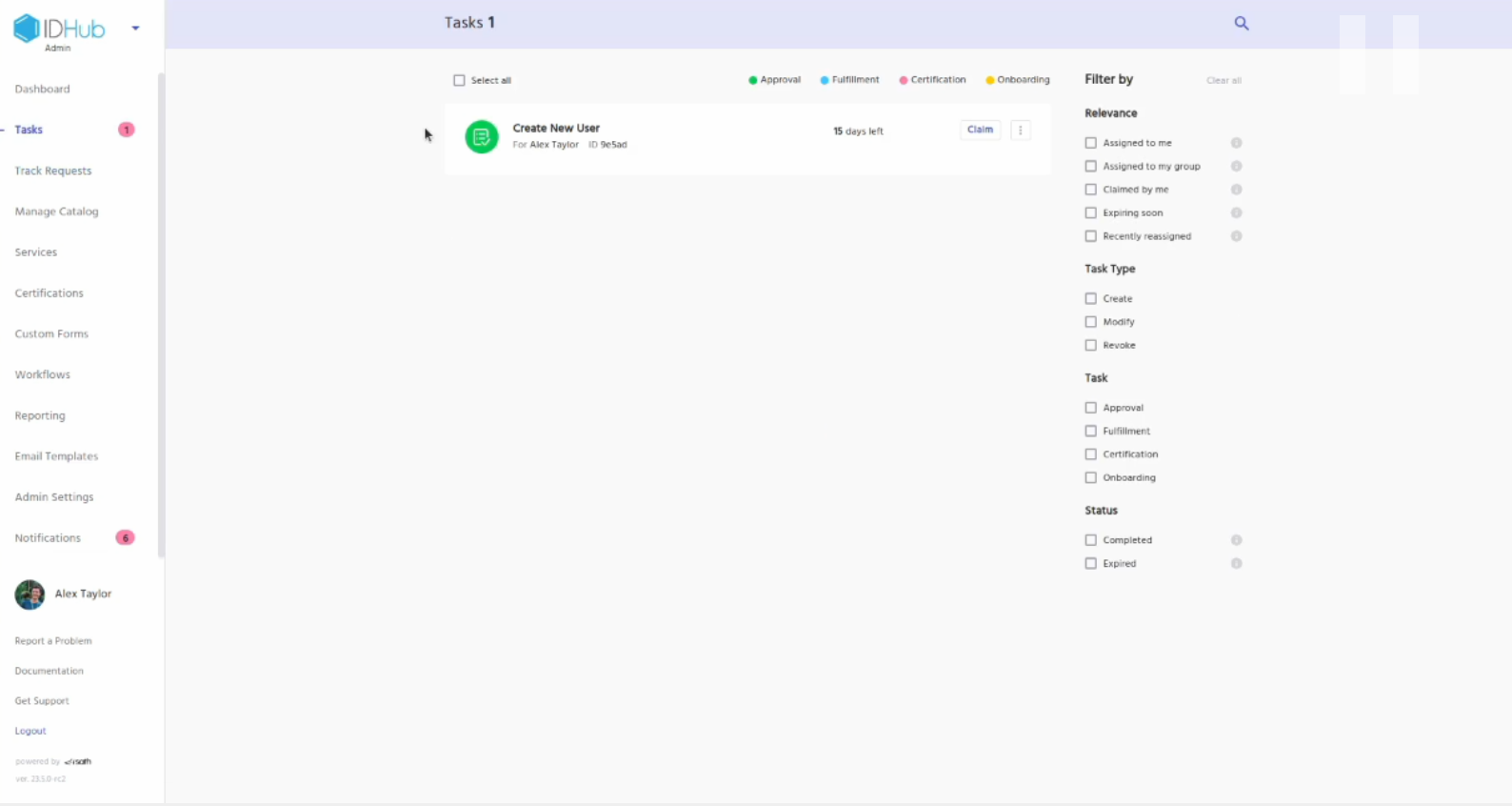
Goto Search catalog and click on the user tab. You will see the new user that you just created.

Click on the user card. A RHS will be displayed, Click on the AccessTo tab of the RHS and there you will see that the Entra ID application along with the role is auto-provisioned for the user.

Removing User and Auto Revocation
Removing a User
Go to the manage catalog. Click on the Entra ID application card and then click on the member tab. There also you will see the users who have access to the Entra ID application.

Now let’s remove that user and see if the revocation is automatically done for the user.
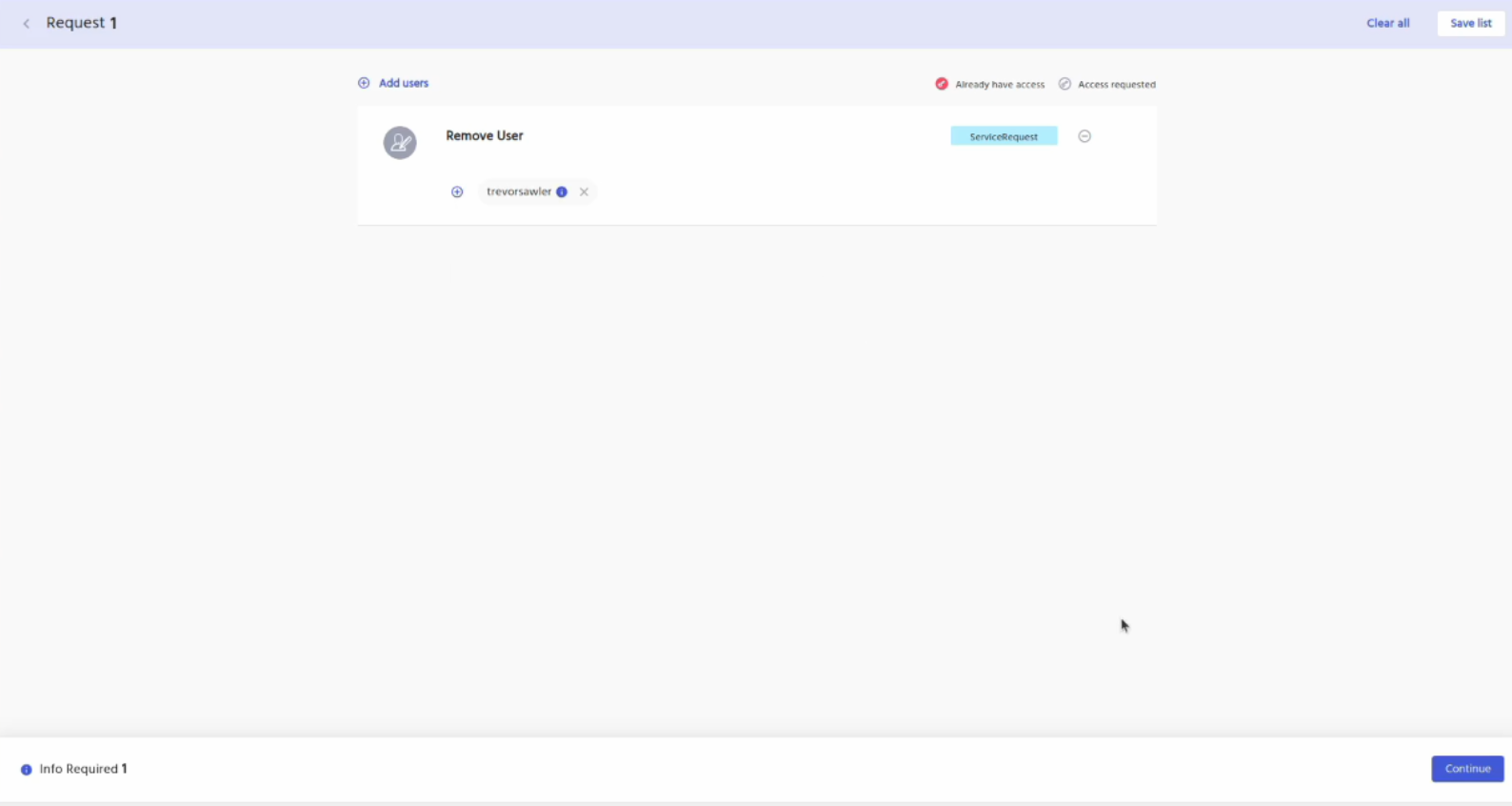
Goto search catalog, click on the services tab and then add remove user to the cart and click on the proceed button. In the next screen enter the user who you wish to remove and then click on the continue button
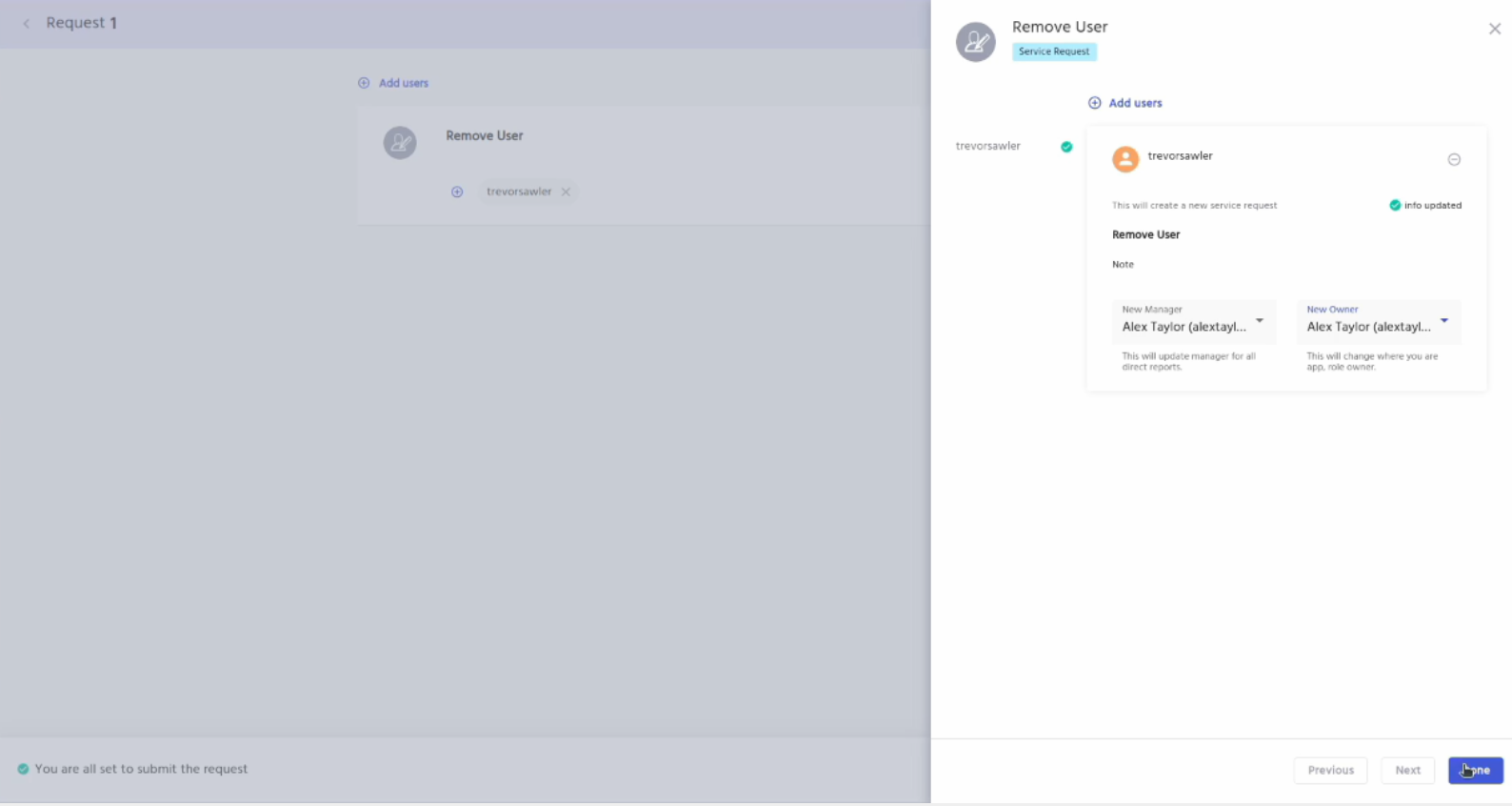
Enter the new manager and the owner and click on the done button.
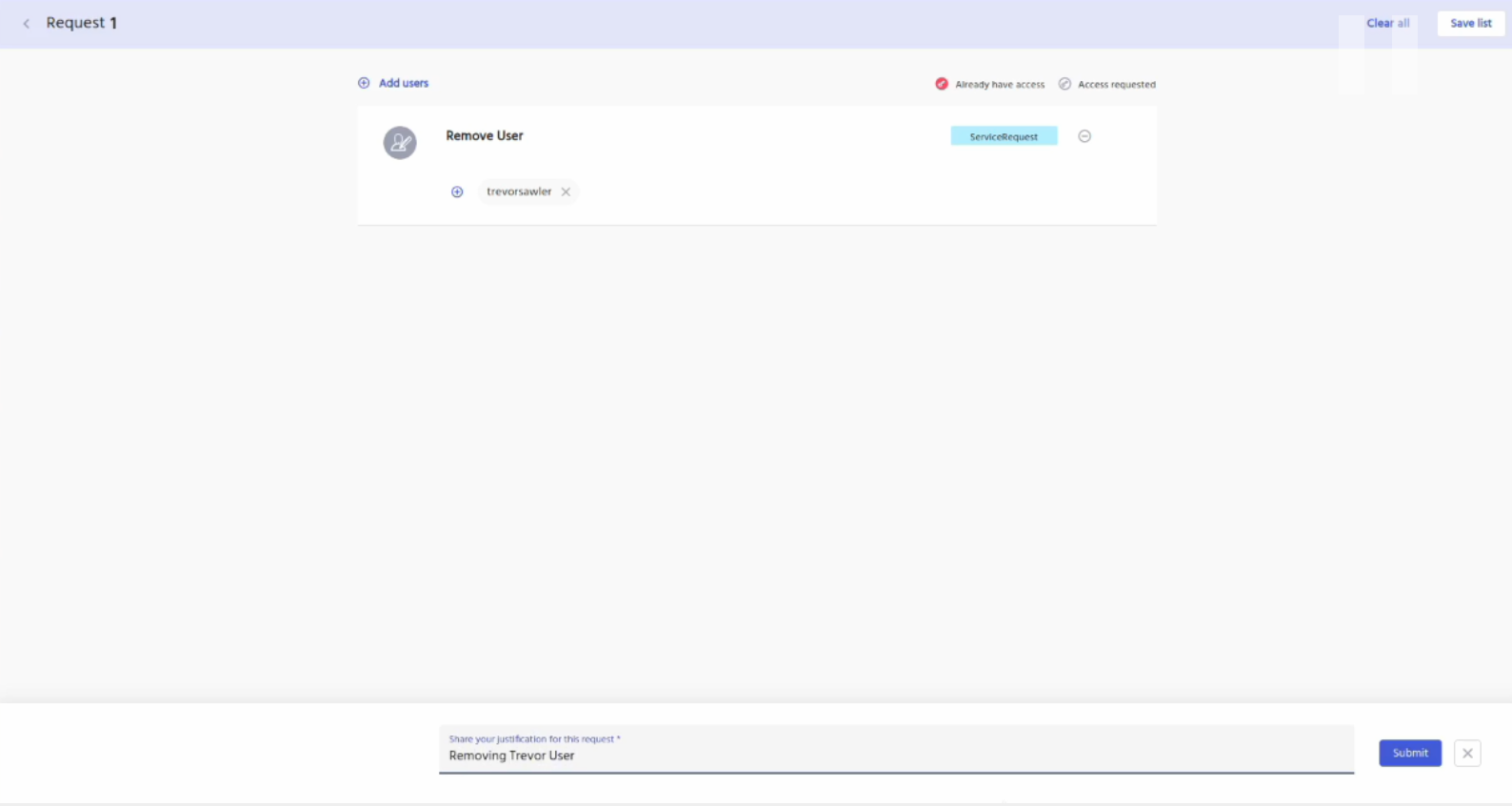
Enter your justification for the request and then click on the submit button.
Goto tasks, claim and approve the request.

Verify the user is revoked from Entra ID application
Now to verify if the user has been revoked from the Entra ID application, goto manage catalog, click on the Entra ID application and then click on the members tab, there you will see that the user who has been removed will also not be displayed there.
Add User in Entra ID & Auto-Provisioning
Add a User in your Entra ID Instance
Now let’s create a new user in your Entra ID target system. Under Users Click on Add New button and you will see the following screen:
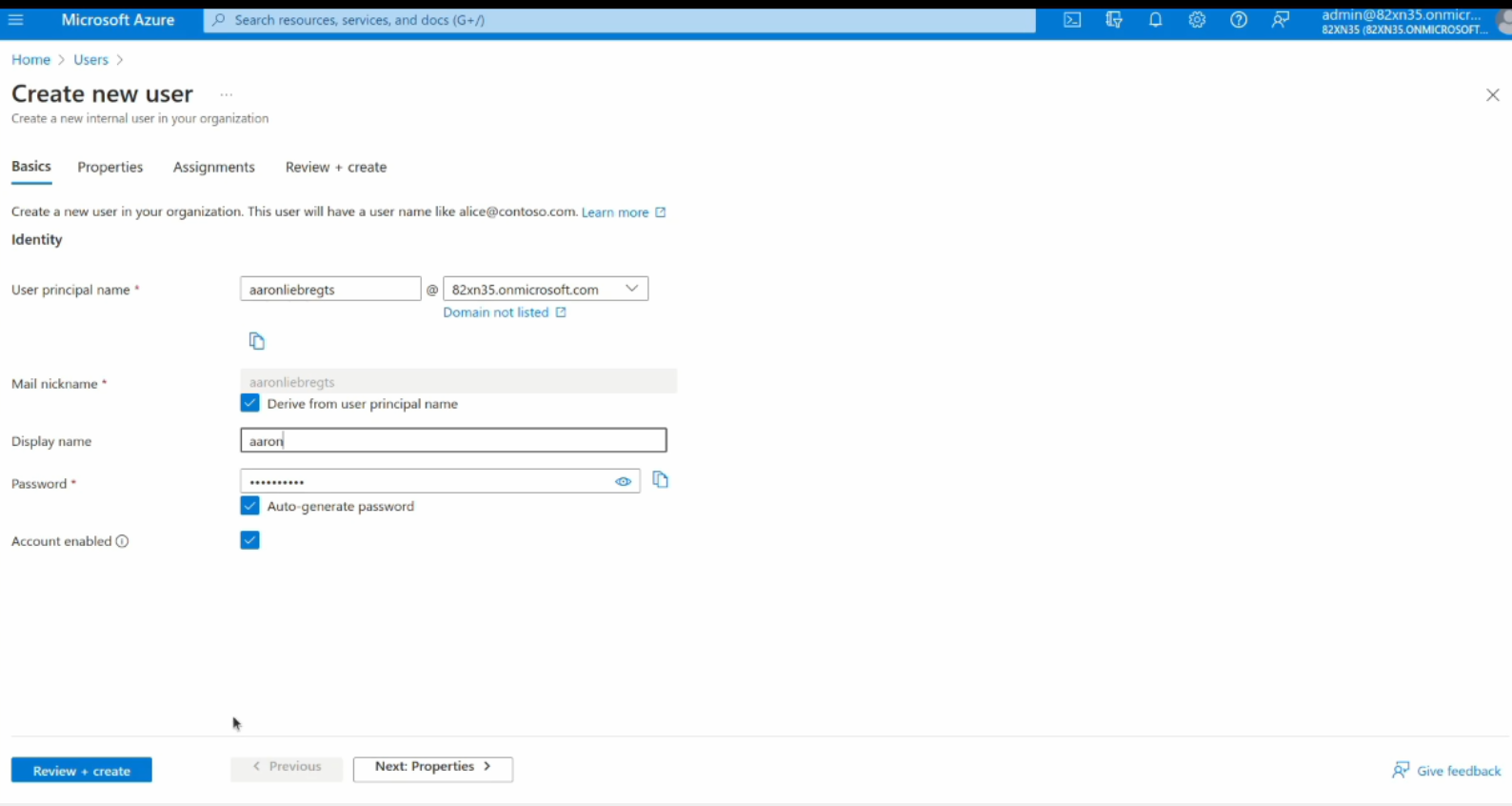
In this screen add the user principal name, display name and password and click on the Review & Create button below.
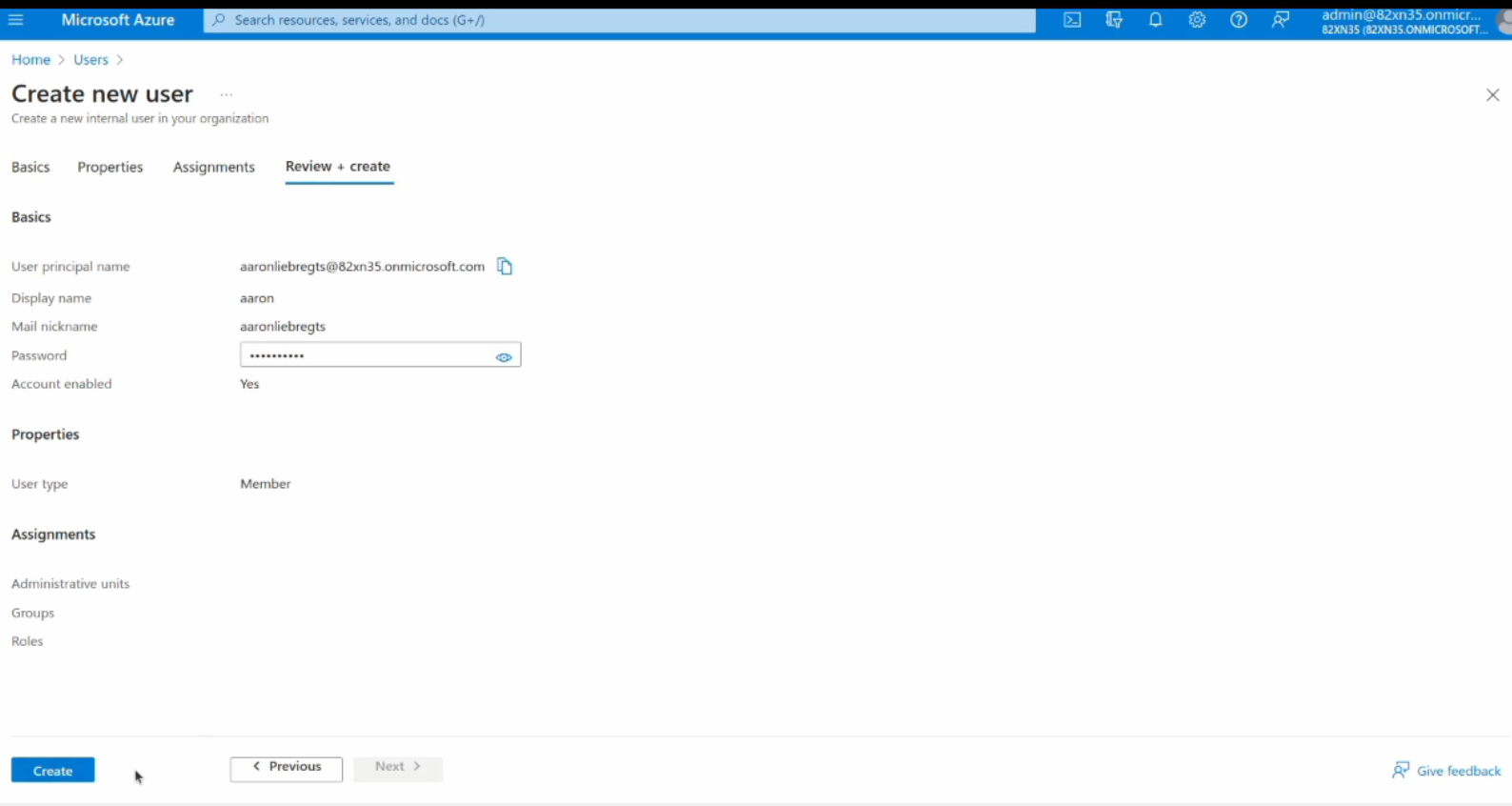
Another screen will display the confirmation page and you need to click on the create button to add the new user to your Entra ID instance.
Reconcile Accounts
Now goto manage catalog, click on the 3 dots menu for the Entra ID application, click on the Application Sync menu
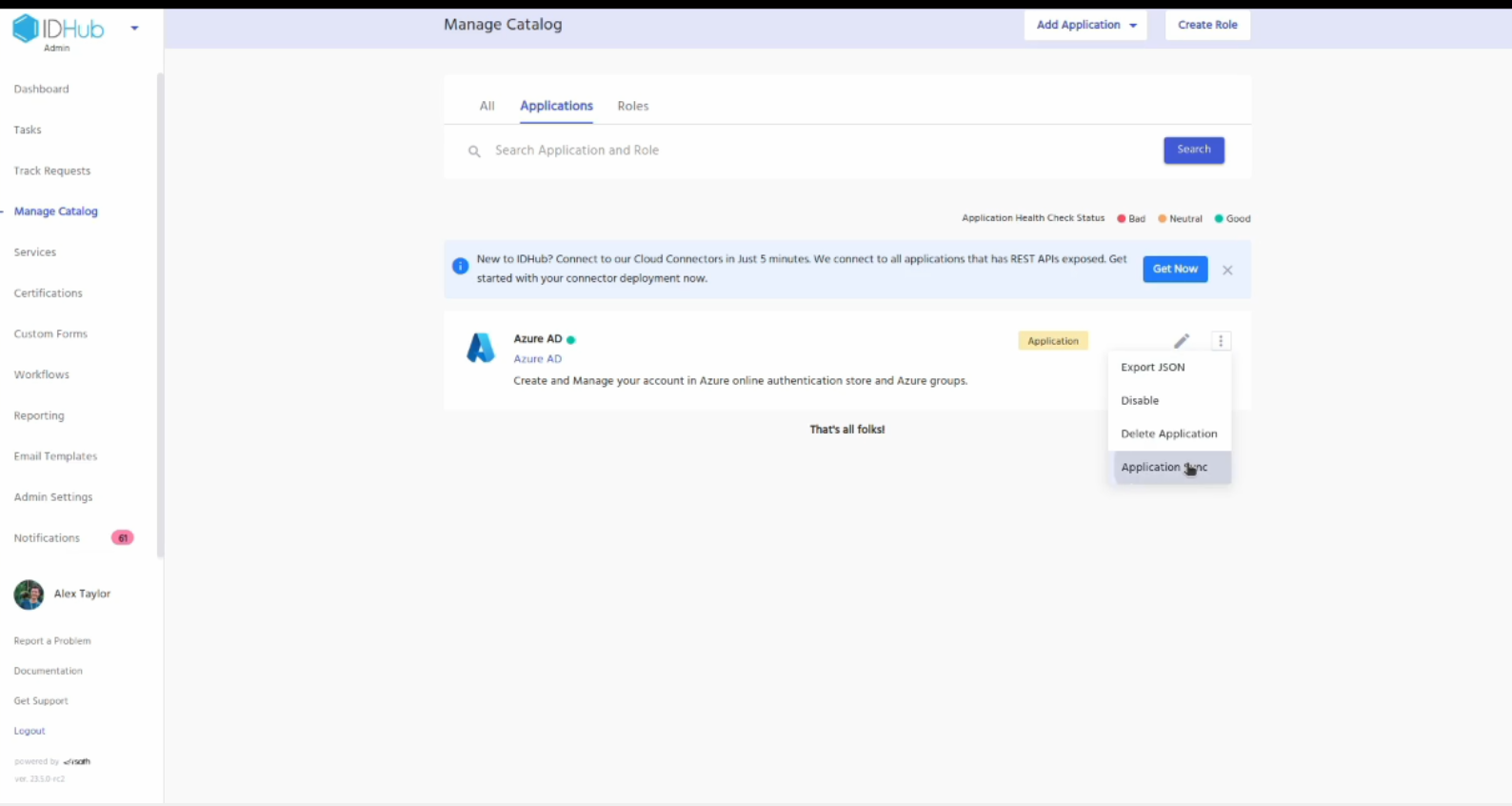
Pop-up window will be displayed. Click on the reconcile button and then hit the submit button.

Click on the yes button in the pop-up window.
Now again click on the application and then goto the application reconciliation logs. You will see that the sync is in progress. Wait for a few minutes for the sync to get completed.
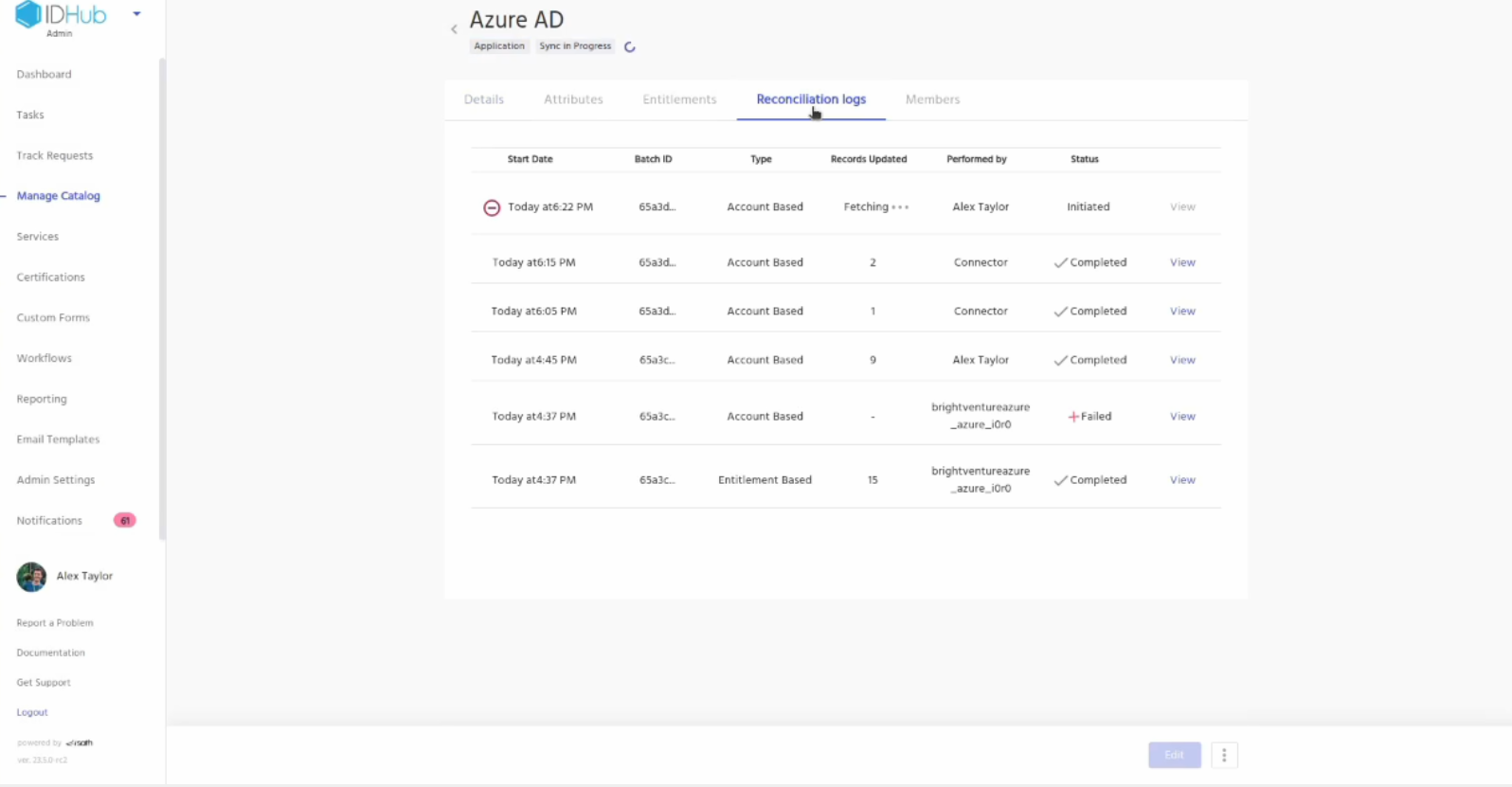
Once finished click on the view link for the log, there you will see that the new user that you had created in your Entra ID target system has been automatically synced into IDHub.

NOTE: There is an auto-stream feature in Entra ID connector that we have developed, which will automatically reconcile accounts from your Entra ID instance to IDHub every few minutes.
Running Certification & Auto-Revocation
Running the Certificate and Revoking Access
Now goto certifications and click on the 3 dots menu for the Entra ID Access Review certification and then click on the run now.

Click on the yes button in the pop-up window

Goto tasks and there you will see the certification tasks
Click on one of the certification task
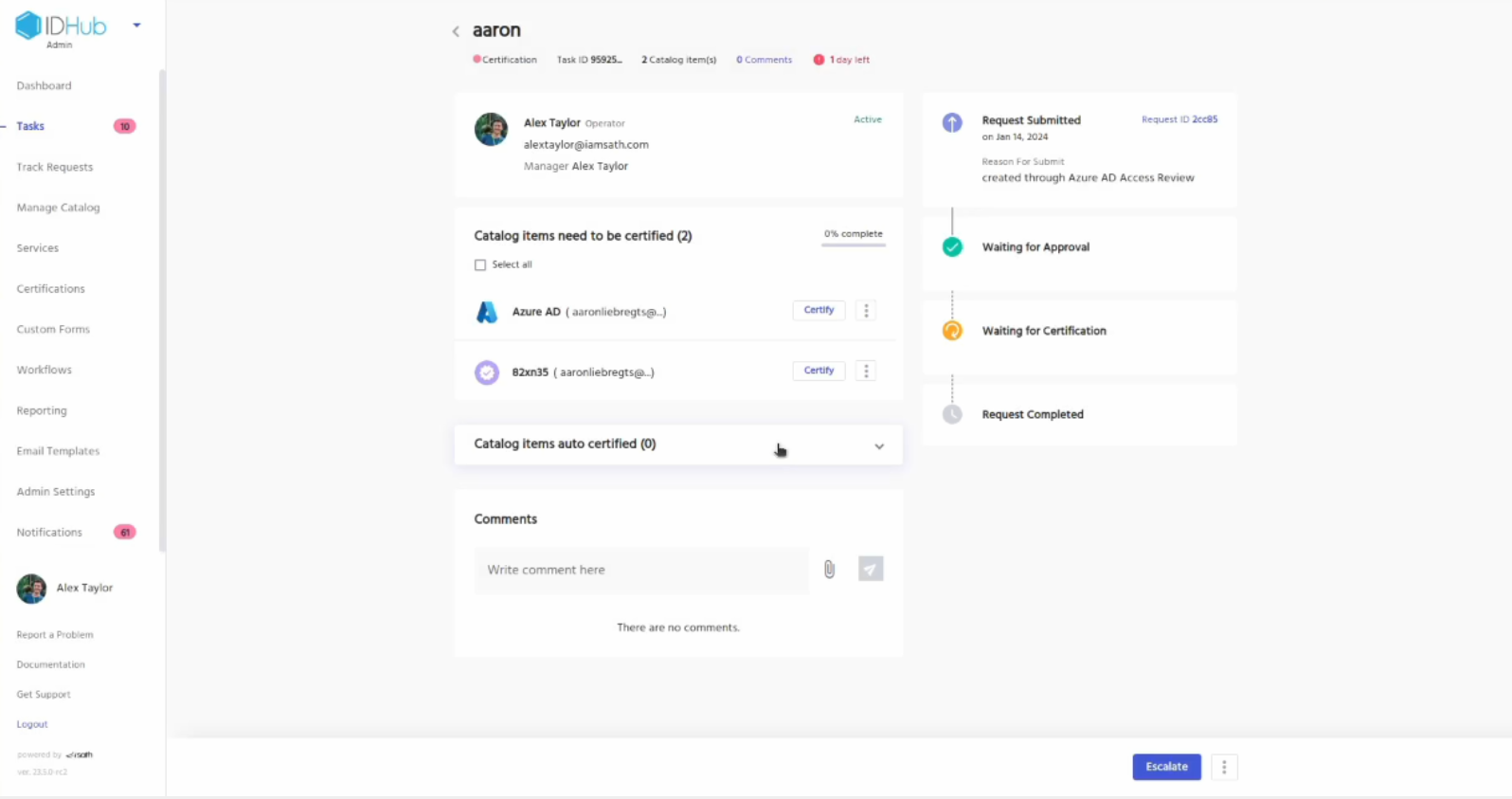
Let’s revoke access to Entra ID for the user. Click on the revoke button for Entra ID
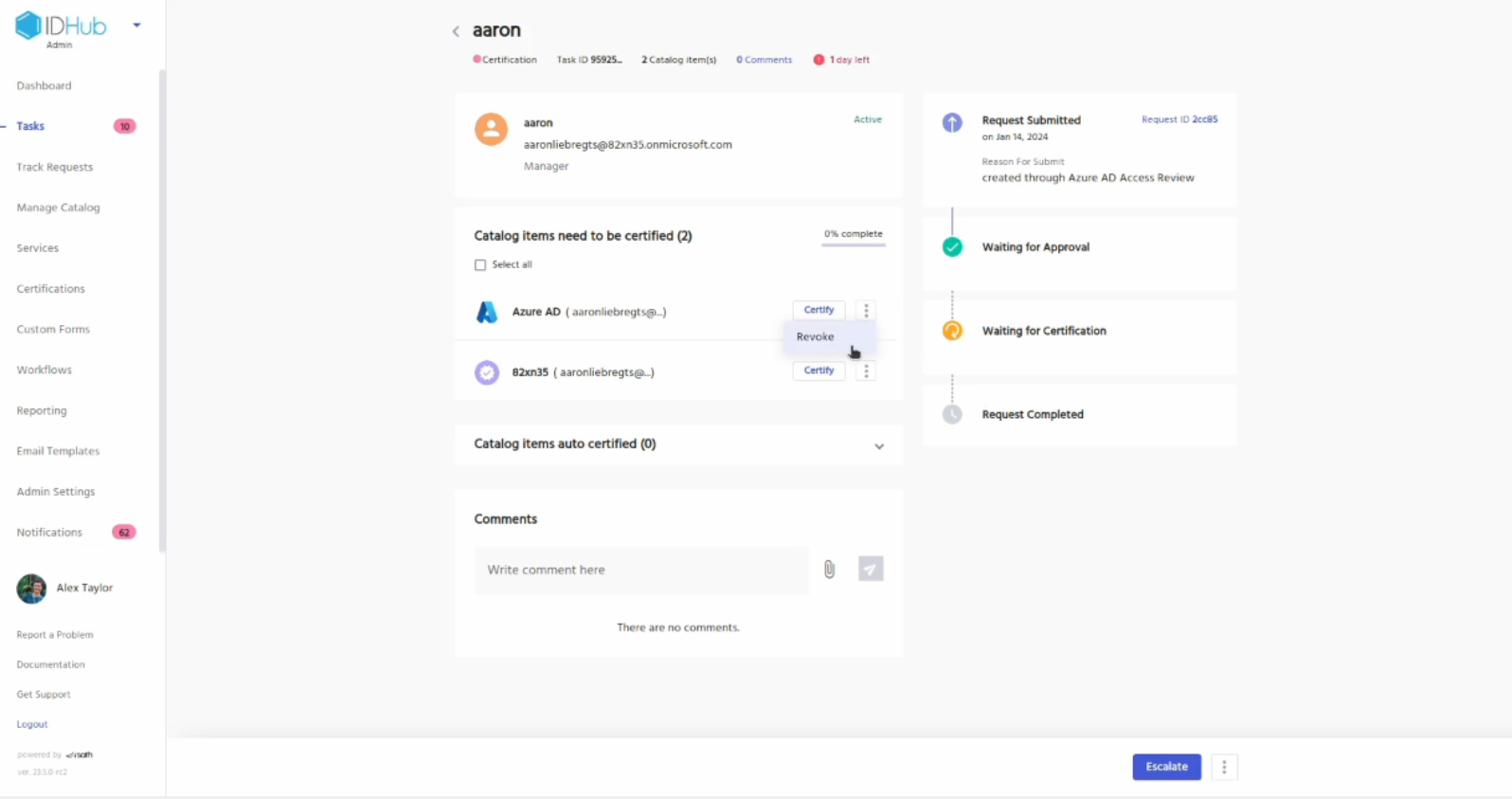
Enter a reason for the revocation and click on the revoke button.
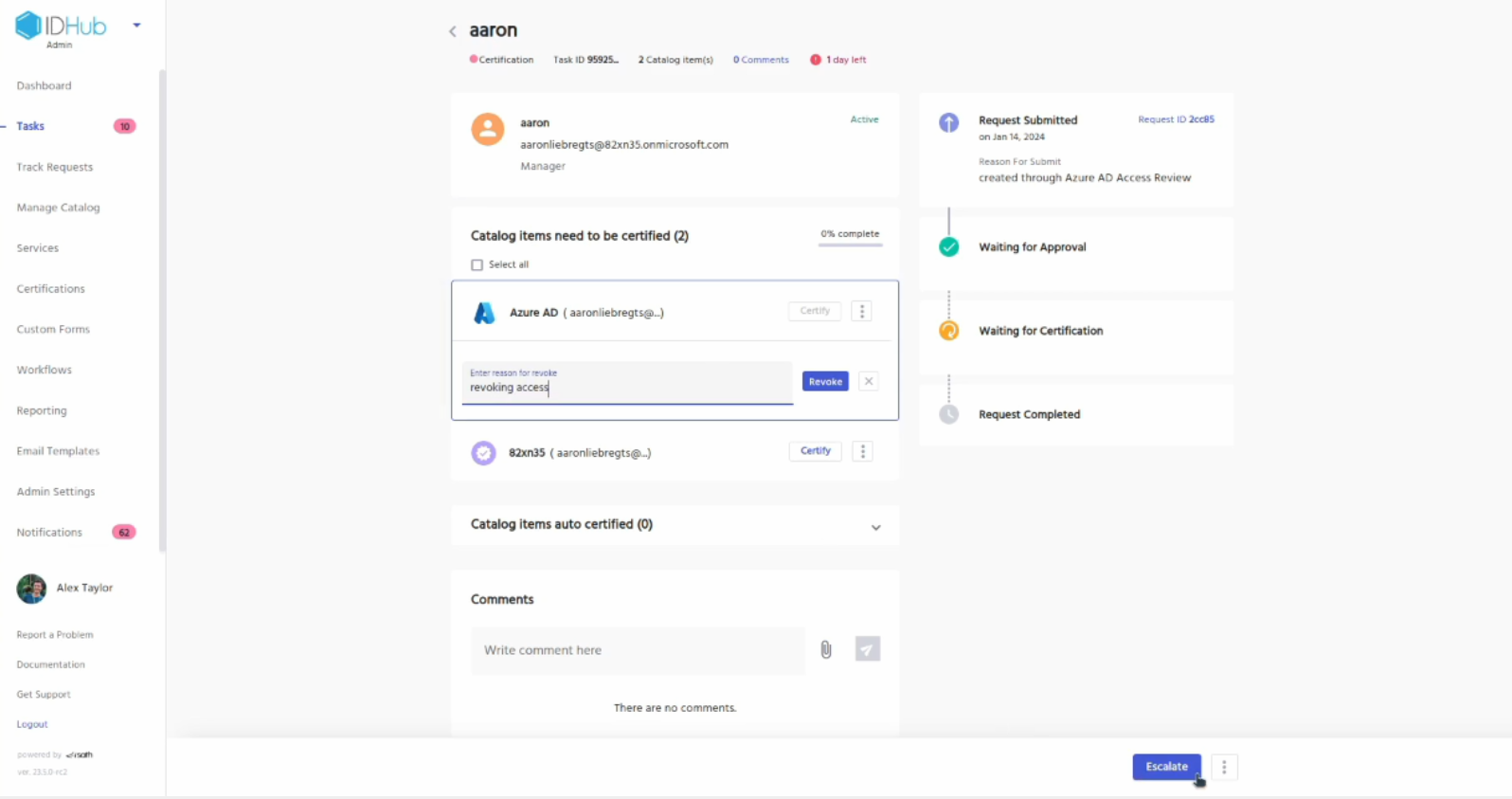
Similarly you can certify the other resources if you want and then click on the complete button.

Verifying if the user has been revoked
Go to IDHub user app, click on the search catalog and then click on the users tab. Search for the user whom you have just revoked access via certification.

Click on the user. A RHS will be displayed. Click on the AccessTo tab of the RHS. You will see that the Entra ID application has been revoked for the user.
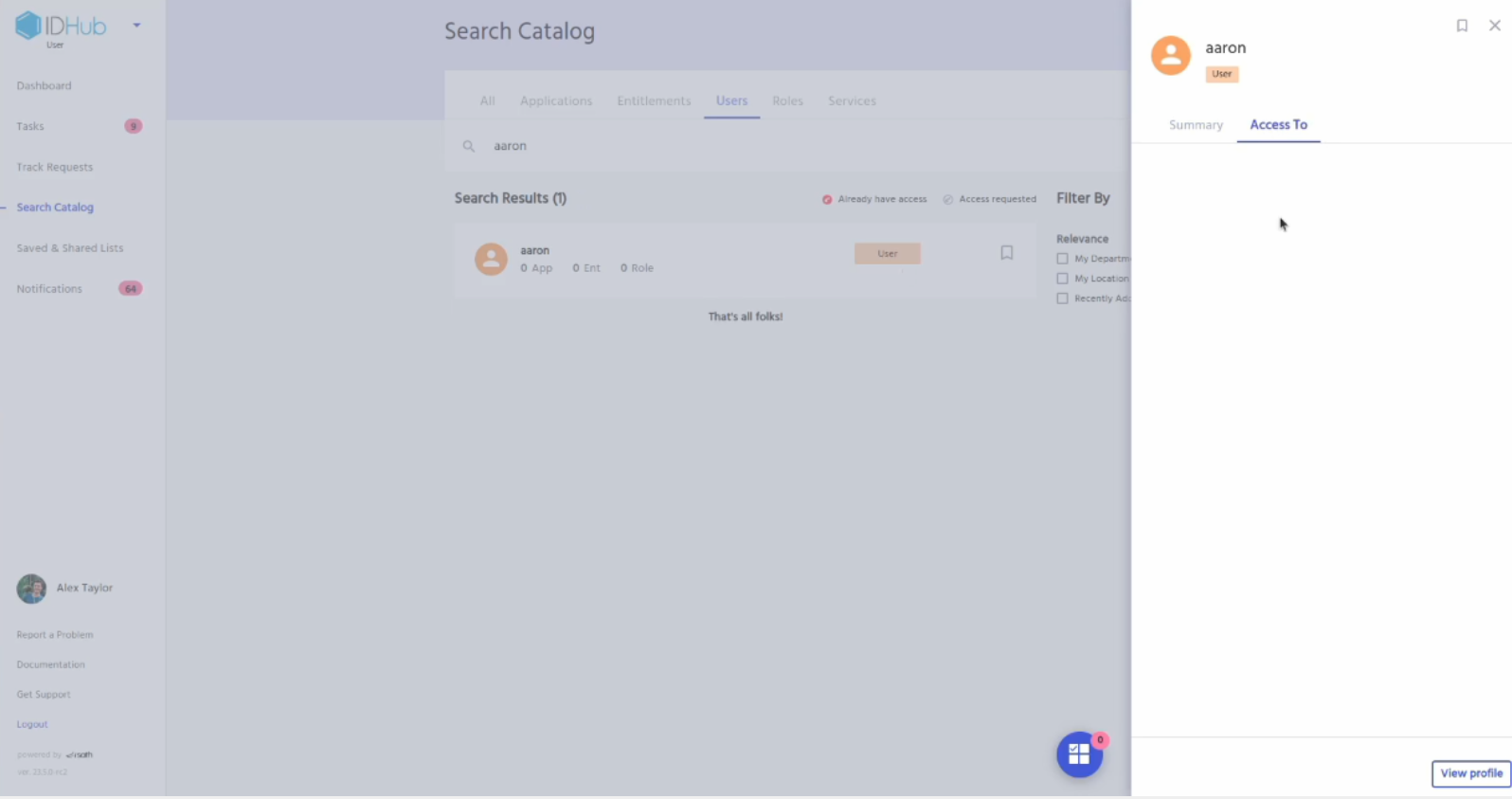
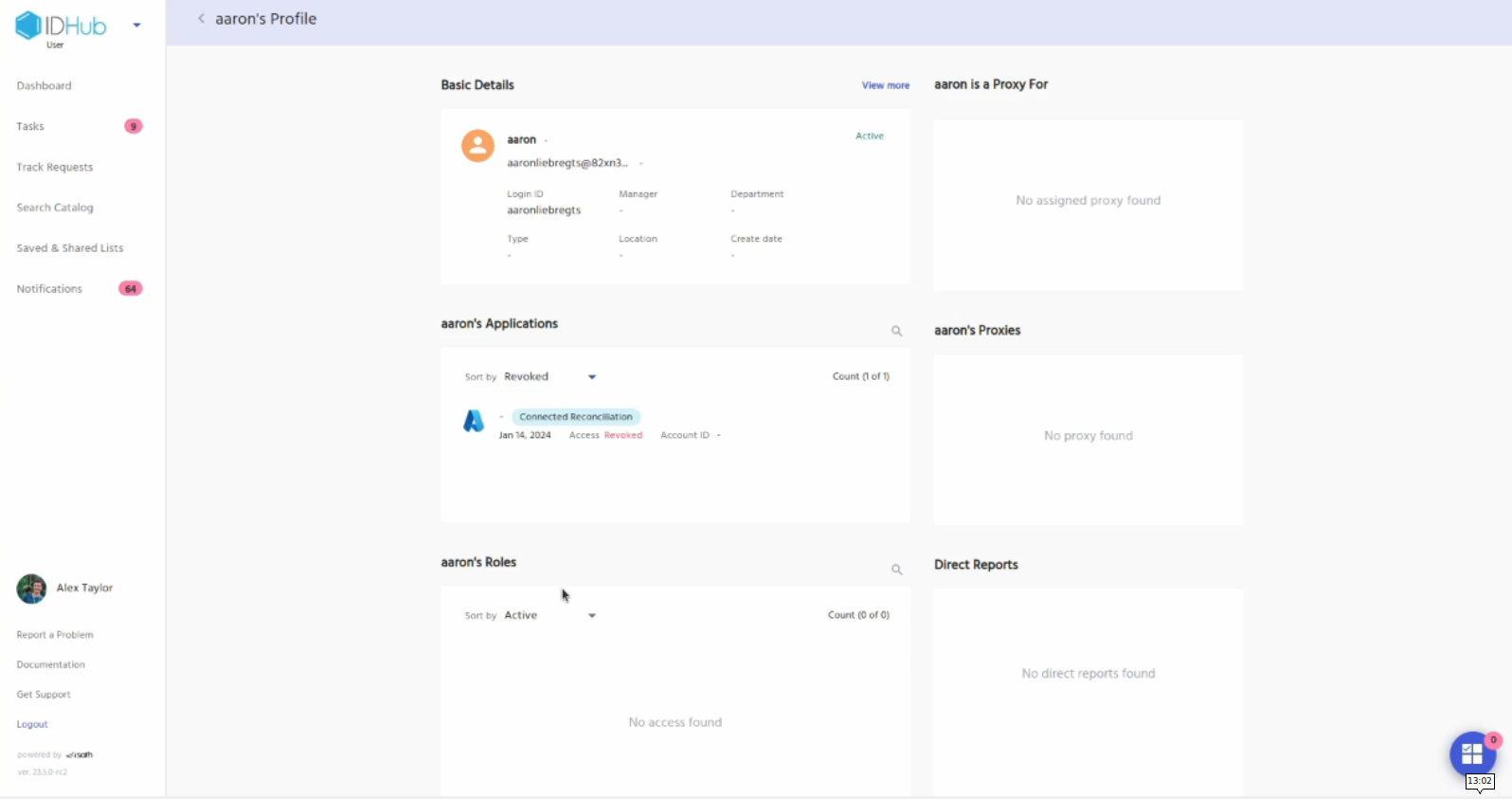
Click on the View profile button of the RHS. This will redirect you to the user profile page.

Under applications section, click on the drop-down and then select revoked, this will show the Entra ID application with revoked status.
Ending Notes
We've reached the end of this tutorial and IDHub team would like to extend our heartfelt thanks to you for taking the time to engage with this content. Your dedication to learning and growth is what fuels the creation of resources such as this.
We hope that this tutorial has been informative, helpful, and has enriched your knowledge on the topic. Your willingness to learn is admirable, and we hope that the insights provided here have added value to your journey.
If you have any questions or concerns, or if there are areas you wish to explore further, please feel free to reach out here. Your feedback is incredibly valuable, not only in improving these resources, but also in helping to shape future content.