
Introduction
With over 200 banking laws across the U.S., maintaining compliance is more challenging than ever. The recent $135.6 million fine against Citibank for ongoing compliance issues highlights the real financial risks of falling short. Access reviews, Identity and Access Management (IAM), and reporting play a critical role in managing who has access to your systems, helping your institution adhere to regulations such as FFIEC, SEC, FINRA, GDPR, SOX, and PCI-DSS. In this post, we’ll explore how improving these practices can help reduce risks, strengthen compliance, and keep your financial institution on a secure and compliant path.
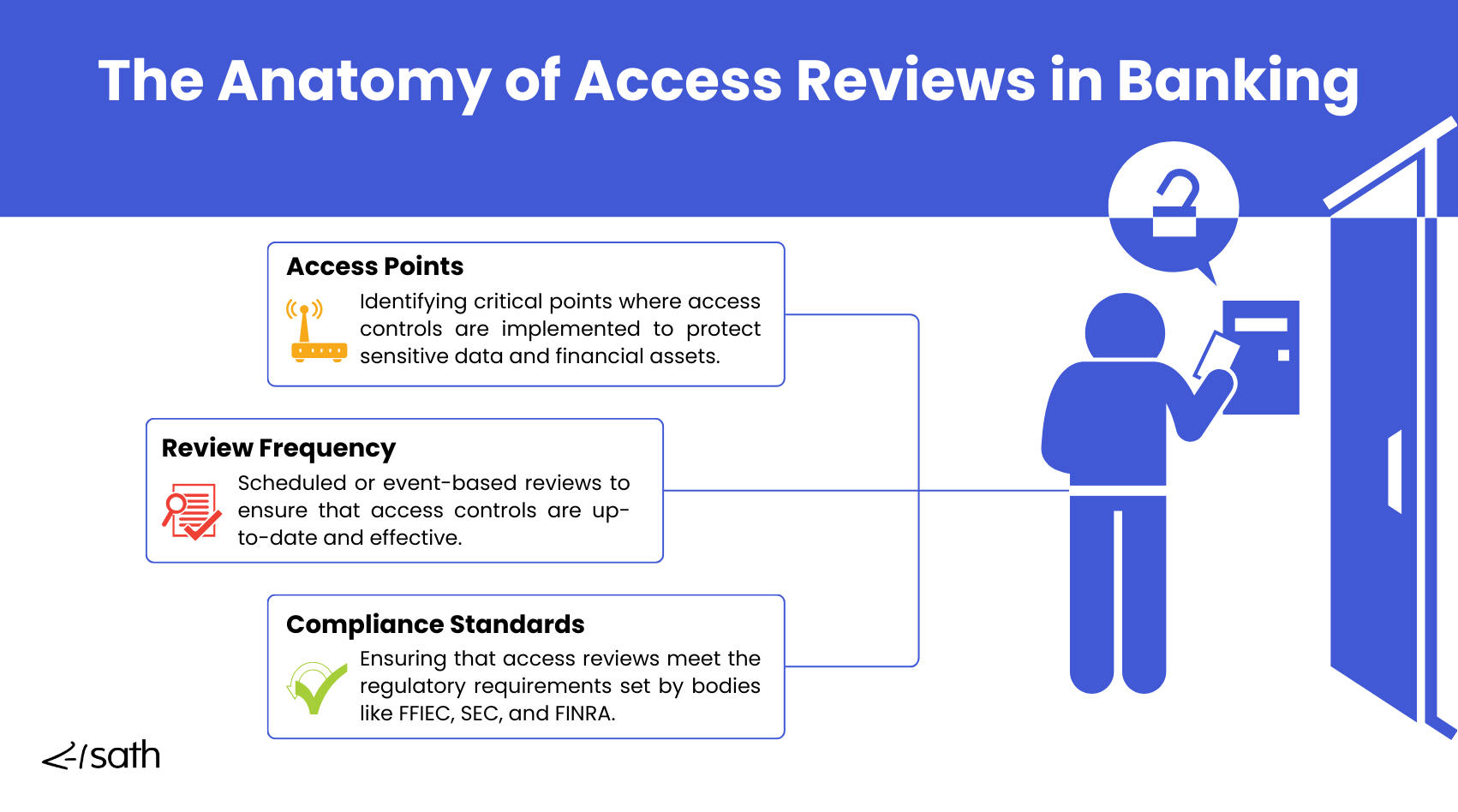
Understanding Access Reviews in Banking Compliance
What are Access Reviews?
Banking access reviews, as part of Identity and Access Management, are systematic checks designed to verify that only the right individuals can access specific data and systems within the organization. These reviews help financial institutions maintain control over sensitive information, reduce the risk of unauthorized access, and ensure access rights align with current job responsibilities.
Types of Access Reviews
Access reviews can be periodic, occurring on a regular schedule like quarterly or annually, or triggered by specific events, such as role changes, employee departures, or security incidents. Periodic reviews help maintain ongoing compliance, while event-based reviews respond to immediate changes, ensuring that access permissions are always current and appropriate.
Why Access Reviews Are Essential?
Protecting Sensitive Data and Financial Assets
Access reviews protect an institution’s sensitive data and financial assets. By incorporating Identity and Access Management (IAM) practices and routinely checking who has access to critical systems, financial institutions can prevent unauthorized individuals from gaining access to valuable or confidential information, thereby reducing the risk of internal fraud or data theft.
Preventing Unauthorized Access and Potential Data Breaches
Regular access reviews help identify and revoke unnecessary or outdated access permissions, reducing the risk of unauthorized access that could lead to data breaches. This proactive measure is a key component in a bank’s overall security strategy, helping to mitigate potential threats before they materialize.
Access Controls for Authorized Personnel
An essential function of Identity and Access Management and access reviews is confirming that only those with a legitimate need have access to specific systems and data. This selective access supports the principle of least privilege. It helps ensure that sensitive information is handled by trained and authorized personnel, essential for maintaining security and operational integrity.
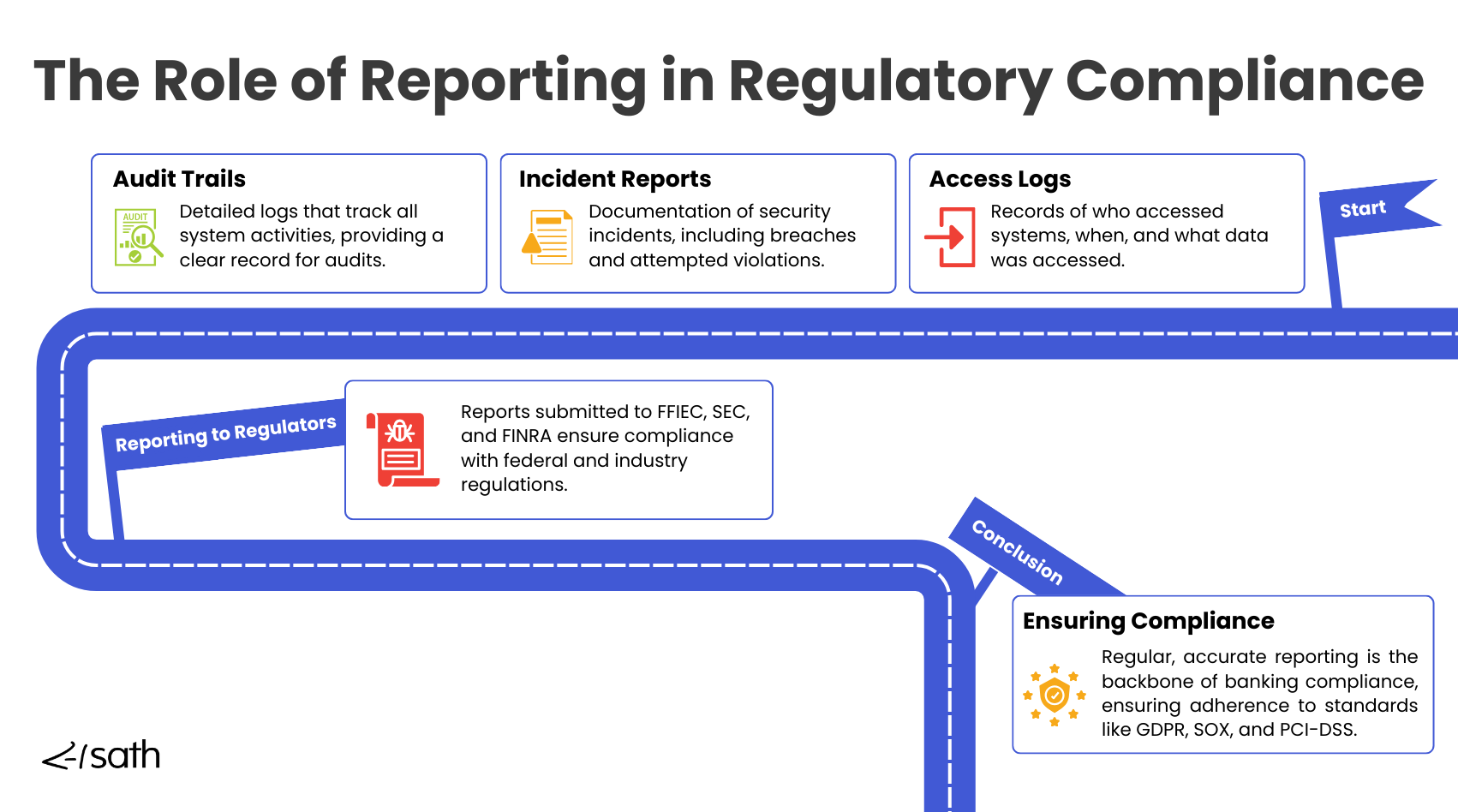
The Role of Reporting in Banking Compliance
Effective reporting, coupled with IAM data, depends on three main factors: accuracy, timeliness, and thoroughness. Accuracy means that every data in the report reflects what’s happening in the bank, leaving no room for errors.
Timeliness is about submitting these reports on schedule, which is important to avoid regulatory penalties. Thoroughness means covering all necessary aspects, from financial transactions to audit findings, so that regulators have a complete view of the bank’s operations.
Reporting as a Tool for Compliance
Regular reporting plays a big role in helping banks meet their compliance obligations under FFIEC, SEC, and FINRA regulations. By submitting detailed and consistent reports, banks can show that they are managing risks properly, maintaining strong internal controls, and following the rules set by regulators. This practice also helps identify potential compliance issues early, allowing one to address them before they escalate.
Transparency and Accountability in Reporting Practices
In the financial sector, transparency in reporting means being straightforward about the bank’s activities and providing complete and accurate data. This approach builds trust with regulators by showing that the bank has nothing to hide. Accountability comes from taking responsibility for the accuracy of these reports, making sure that any mistakes are corrected quickly and that the data presented is reliable.
How Regulators Use These Reports
Regulators use banks' reports to assess how well they comply with relevant laws and regulations. They examine the data to evaluate the effectiveness of the bank’s risk management practices, internal controls, and overall financial health.
These reports help regulators identify potential issues, such as security gaps or inconsistencies in financial reporting, which could lead to further scrutiny or audits.
Financial regulators often require several types of reports to monitor compliance:
- Access Logs: Document who accessed specific systems or data, allowing regulators to evaluate the effectiveness of access controls.
- Incident Reports: Provide details on any security breaches or operational incidents, including the impact and how the bank responded to the situation.
- Audit Trails: Offer a complete history of financial transactions and other critical activities, helping regulators verify the accuracy and integrity of financial operations.

Download our free info-graphic on how to mater IAM!
How Access Reviews and Reporting Work Together
Access reviews, part of a broader Identity and Access Management (IAM) framework, are important in gathering the data needed for regulatory reports. When banks conduct access reviews, they carefully examine who has access to various systems and sensitive information.
This review generates detailed records that show whether access is properly restricted and if any unauthorized access has occurred. These records are then used in regulatory reports to demonstrate that the bank is actively managing and controlling access to critical data, a key requirement for compliance with various regulations.
Access reviews and reporting are part of a continuous cycle that helps banks stay compliant and improve their processes over time. First, access reviews identify potential issues with who can access sensitive systems. Then, the findings from these reviews are documented and included in regulatory reports.
Once these reports are submitted, the bank can use feedback from regulators and internal assessments to refine its access control policies and procedures. This cycle of reviewing, reporting, and making improvements helps the bank strengthen its overall compliance framework and reduce risks.
Check out this influencer video demo to learn more about how IDHub uses Access Reviews and Reporting to meet regulatory compliance.

The Impact of Key Compliance Standards on Access Reviews and Reporting
FFIEC Guidelines
The FFIEC (Federal Financial Institutions Examination Council) outlines specific requirements for access reviews and reporting under its IT Examination Handbook, particularly in the Information Security and IT Risk Management sections. Financial institutions are expected to conduct regular Identity and Access Management (IAM)-driven access reviews to verify that access permissions align with job responsibilities and that any unnecessary or outdated access rights are promptly removed.
The FFIEC guidelines also emphasize the need for comprehensive documentation of these reviews, which should include details on who has access to critical systems, the level of access granted, and the justification for this access.
Institutions should implement structured processes defining access rights assigned, reviewed, and revoked to meet these requirements. This includes setting up automated tools for tracking access rights, scheduling regular review intervals (e.g., quarterly or annually), and documenting the outcomes of these reviews.
Such processes help institutions comply with FFIEC standards by ensuring that access controls are consistently enforced and that any issues identified during reviews are promptly addressed and reported.
SEC and FINRA Regulations
The SEC (Securities and Exchange Commission) and FINRA (Financial Industry Regulatory Authority) impose stringent access controls and reporting requirements, particularly through regulations like SEC Rule 17a-4 and FINRA Rule 4511, which focus on record-keeping and data security.
These regulations require financial firms to maintain tight access controls over systems that contain sensitive financial data, such as trading systems, customer records, and compliance-related documentation. Regular access reviews are mandatory to ensure that access is limited to individuals with a legitimate business need and that any unauthorized access attempts are swiftly identified and reported.
Firms are expected to conduct periodic reviews to assess the effectiveness of their access controls, ensuring that access rights are aligned with the principle of least privilege. This means granting the minimum necessary access for users to perform their roles.
Detailed records of these reviews, including access logs, audit trails, and incident reports, must be maintained and made available for regulatory inspection. These documents help demonstrate the firm’s compliance with SEC and FINRA regulations, showing that it actively monitors and manages access to critical systems.
GDPR Considerations
The GDPR (General Data Protection Regulation) imposes rigorous data protection and privacy standards, particularly concerning the access and processing of personal data. Articles 25 (Data Protection by Design and Default) and 32 (Security of Processing) of the GDPR require financial institutions to implement access controls that limit data access to only those individuals who need it for specific, authorized purposes.
GDPR also mandates that institutions conduct regular audits and review access controls to ensure ongoing compliance and that any data breaches be reported to the relevant supervisory authority within 72 hours under Article 33.
To comply with GDPR, financial institutions must integrate data protection into their access review processes. This involves conducting detailed access audits to verify that access rights are correctly assigned and promptly adjusted when an individual’s role changes or when they leave the organization. Institutions must also maintain records of these reviews, documenting who has access to personal data, the rationale for granting access, and any actions taken to address unauthorized access.
SOX Compliance
Access reviews and reporting are crucial for meeting the Sarbanes-Oxley Act (SOX) requirements, particularly under Sections 302 and 404, which focus on internal controls over financial reporting (ICFR). These processes ensure that access to financial systems is tightly controlled, reducing the risk of unauthorized changes that could compromise the accuracy and integrity of financial data.
Regular access reviews help verify that only authorized personnel have the necessary access, supporting the segregation of duties—a key control mechanism under SOX. Comprehensive reporting provides an audit trail that documents who has access to financial systems, when changes are made, and how any issues are resolved, demonstrating compliance to auditors and regulators.
PCI-DSS Standards
Access reviews are essential for complying with the Payment Card Industry Data Security Standard (PCI-DSS), particularly in safeguarding cardholder data. Requirement 7 of PCI-DSS mandates that access to cardholder data be restricted based on business needs. Regular access reviews help verify that only authorized individuals can access sensitive data, reducing the risk of data breaches.
These reviews also ensure access controls remain effective and aligned with PCI-DSS standards. Additionally, detailed reporting of access reviews is a critical component of PCI-DSS compliance audits, as it provides the necessary documentation to demonstrate that the institution has implemented and maintained appropriate security measures, including logging user activity and enforcing security policies.
Conclusion
Identity and Access Management (IAM), along with access reviews and reporting are important for managing who can access sensitive information and for meeting regulatory standards. This post has demonstrated how these practices help comply with FFIEC, SEC, FINRA, GDPR, SOX, and PCI-DSS regulations. Keeping up with these reviews and reports helps banks protect their assets and stay prepared for future challenges. To strengthen your institution’s compliance, book a call to see how IDHub can help you stay on track.
Continue Part 4 of this finance series: How IAM Mitigates Insider Threats
