Healthcare Compliance
Identity and access management (IAM) is essential for healthcare technology organizations to securely manage and control access to sensitive patient data, safeguarding privacy and ensuring full compliance with regulatory requirements enforced by agencies such as HIPAA, HHS, OCR, and FDA.
Identity Managment in Healthcare
Hospitals and healthcare organizations face the dual challenge of rapidly enabling staff access while defending against sophisticated cyber threats. Navigating complex compliance requirements—such as HIPAA and HITECH—adds further pressure, making manual identity management processes impractical and risky.
Healthcare IAM must address the unique complexity of users with multiple roles and diverse authoritative sources across a large, dynamic workforce. Effective identity and access management helps healthcare providers strengthen their security posture while improving operational efficiency.
Key benefits include:
- Ensuring users have precisely the access they need—no more, no less
- Minimizing friction between clinicians and IT security teams to maintain workflow efficiency
- Reducing the administrative burden of manual identity and access management tasks
- Simplifying audit preparation and making compliance demonstrations straightforward and reliable
By adopting advanced Identity and Access Management (IAM) strategies, healthcare organizations can protect sensitive patient data, meet stringent regulatory demands, and empower their workforce with seamless, secure access.
IAM Features for Healthcare Cybersecurity
Healthcare organizations handle highly sensitive data and must meet strict regulatory requirements. Identity and Access Management (IAM) helps control who can access what, minimizing the risk of unauthorized access and data breaches.
Implementing these Identity and Access Management (IAM) features helps healthcare organizations strengthen access control, reduce manual errors, and meet regulatory demands with less overhead.
Key IAM features that support cybersecurity and compliance in healthcare:
Role-Based Access Control (RBAC)
RBAC Limits access based on job responsibilities to prevent unnecessary data exposure.
Multi-Factor Authentication (MFA)
Requires multiple verification steps to reduce the risk of compromised accounts.
Automated Provisioning and Deprovisioning
Automated provisioning and deprovisioning ensures users have the right access when they need it—and removes it when they don’t.
Audit Logging and Reporting
Audit logs and reporting tracks all access activity to support investigations and meet HIPAA, HITECH, and FDA audit requirements.
Single Sign-On (SSO)
SSO provides secure access to multiple systems without requiring multiple logins.
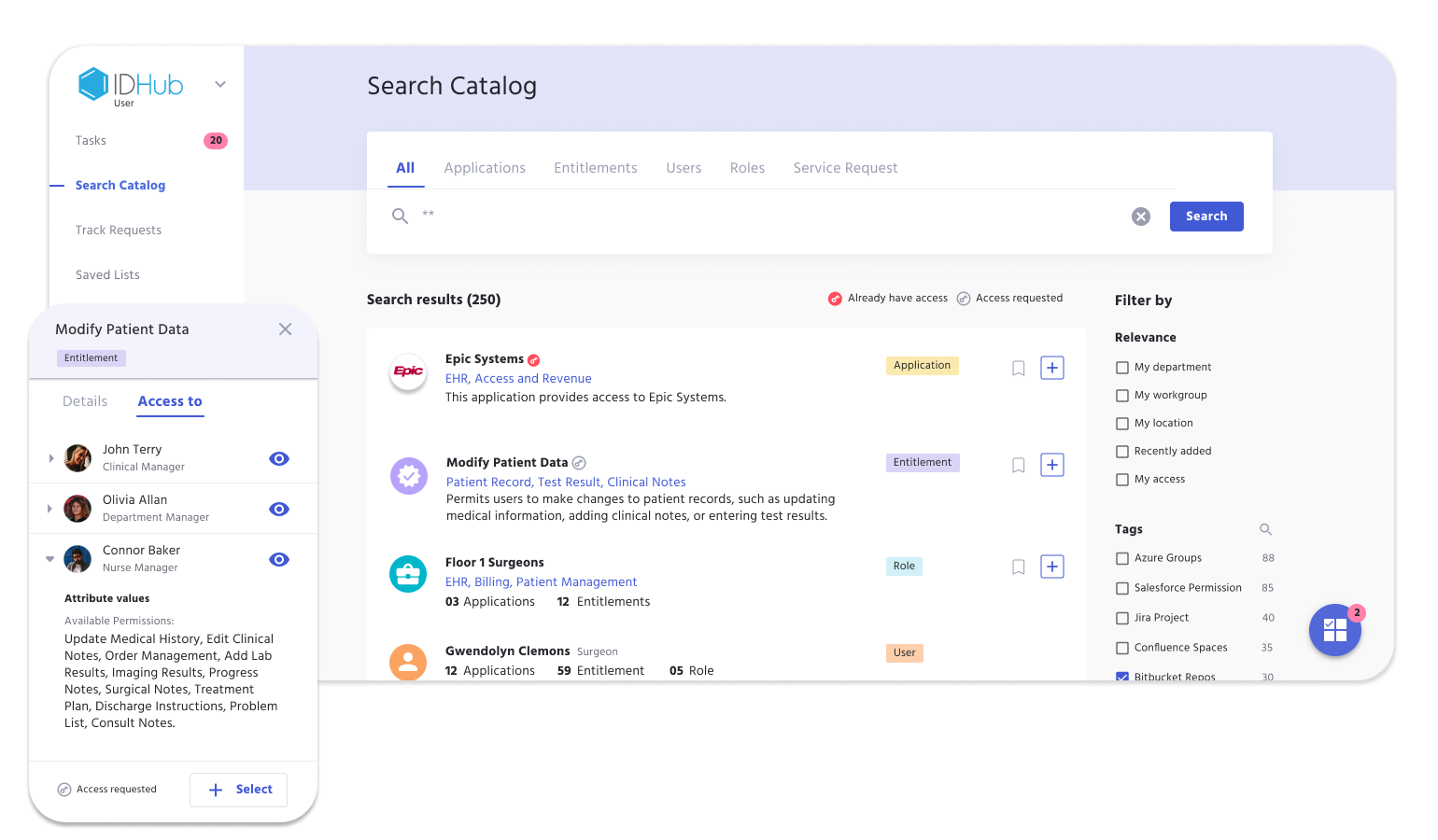
Grant Secure Access Automatically
Provision
Automate Provisioning
Securely enable clinicians and staff to be productive from Day 1 .
Support
Greatly Reduce IT Burdens
Reduce the strain on IT by automating manual processes and workflows.
Govern
Govern Third Party Access
Track affiliated physicians, travel nurses and other users’ access and activity.
Integrate with Healthcare Applications
Epic
Learn how to automate Epic EMP (Employees) and Epic SER (Schedulable Epic Resource) provisioning.
Cerner
Allow consistent enforcement of access and corporate compliance policies across Cerner EHR.
MEDITECH
Provide deep integration to govern identities with management of Accounts and Roles.
Compliance Tools for Cyber Security
Cyber Security Tools

Healthcare Identity and Access Management (IAM)
Our blog post Healthcare IAM explores how IAM solutions can transform your institution's security and operational efficiency.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Protect Patient Data
Our blog post How IAM Protects Patient Data explains how managing access, enforcing compliance, and automating security