Compliance Management
Ensure regulatory cybersecurity compliance through Identity and Access Management. Implement automated controls, audit-ready reporting, and secure access processes that align with frameworks like HIPAA, SOX, PCI-DSS, and GDPR—minimizing risk while maintaining operational integrity.
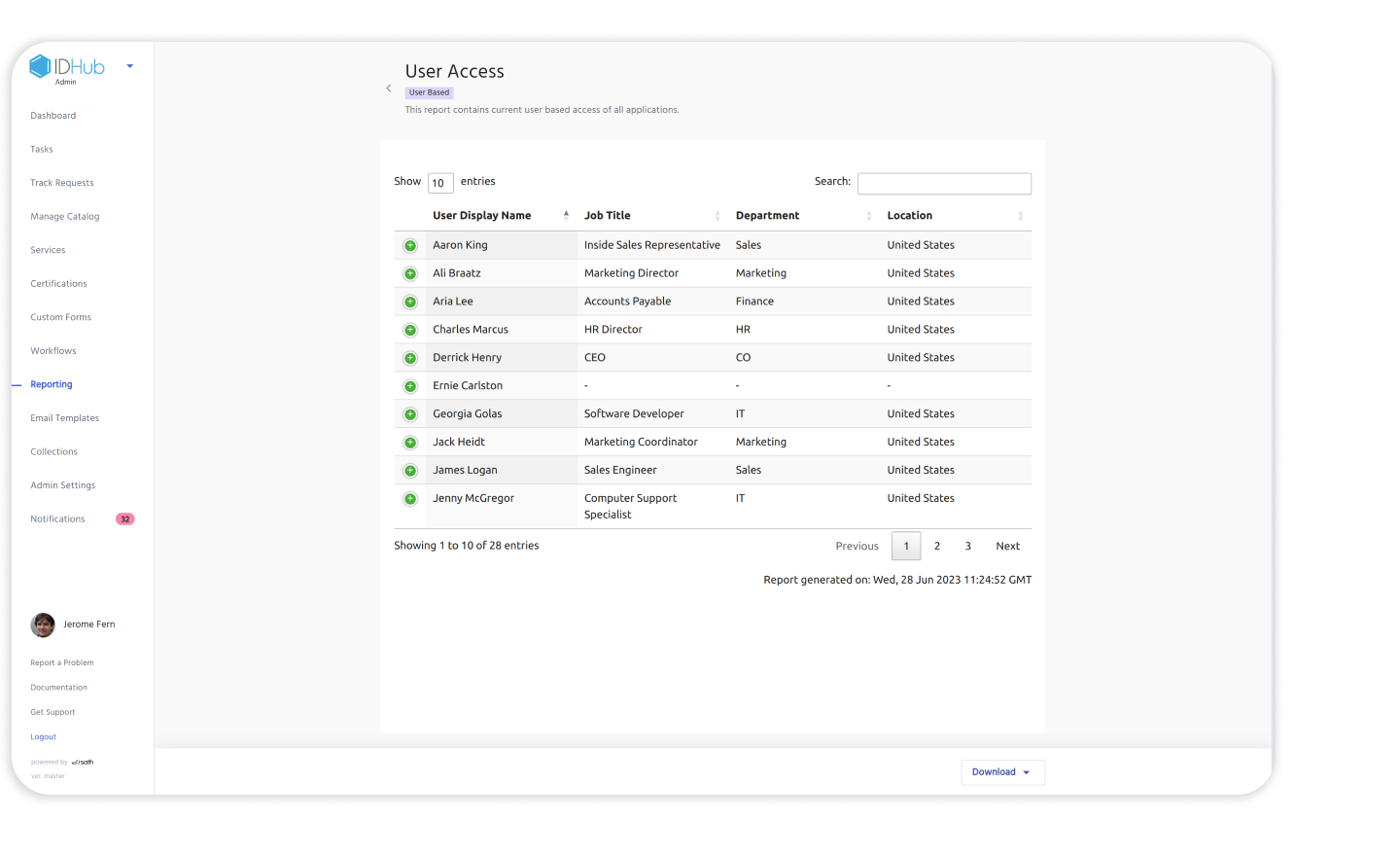
What Is Identity and Access Management (IAM) Compliance?
IAM compliance is the process of aligning identity and access management practices with cybersecurity regulations, data privacy laws, and industry-specific standards. It ensures that user identities, authentication methods, and access controls meet legal and regulatory requirements.
Why Identity and Access Management Is Critical for Regulatory Compliance?
IAM is essential for securing user access to sensitive systems and data. It enforces authentication, authorization, and least privilege policies—core requirements for complying with frameworks like HIPAA, SOX, PCI-DSS, and GDPR.
Aligning IAM with Cybersecurity and Data Protection Standards
By implementing Identity and Access Management (IAM) solutions that support standards such as NIST, ISO 27001, and industry-specific mandates, organizations can reduce access-related risks, streamline audits, and demonstrate ongoing compliance with evolving cybersecurity regulations.
IAM Compliance Solutions
IDHub combines Identity Governance and Administration (IGA) with advanced Access Management to help organizations achieve and maintain regulatory compliance.
Compliance Integrations
Regulatory Frameworks
The compliance management feature integrates with relevant regulatory frameworks, industry standards, and best practices to ensure that the organization's identity security practices align with specific compliance requirements. IDHub includes pre-configured templates, mappings, or guidelines for common regulations like GDPR, HIPAA, or PCI DSS.
RBAC
Role Based Access Control
RBAC enables organizations to manage access privileges based on predefined roles, ensuring access permissions are aligned with regulatory requirements and best practices. RBAC allows organizations to enforce the principle of least privilege and minimize the risk of unauthorized access.
Compliance Check
Assessments and Audits
IDHub offers tools to assess and evaluate the compliance posture of the organization. It includes features like automated compliance assessments, vulnerability scanning, security auditing, and reporting capabilities to identify any gaps or non-compliance issues.
Access Control
Audit Trails and Audit Logs
IDHub provides comprehensive logging and auditing capabilities to track and monitor user activities, access requests, and changes made to the identity and access management system. This helps in demonstrating compliance, investigating security incidents, and generating compliance reports.
Analytics Reporting
Compliance Dashboards
IDHub offers reporting and analytics features to generate compliance reports, track key compliance metrics, and provide visibility into the overall compliance status. Compliance dashboards provide a centralized view of compliance-related information and assist in demonstrating adherence to regulatory requirements.
Regulatory Policy
Security Frameworks
IDHub provides a framework to define and enforce policies and regulations related to identity and access management. It allows organizations to establish rules and guidelines for user provisioning, access control, authentication, password policies, data protection, and other relevant areas.
User Access Reviews for Compliance
Conducting regular user access reviews is critical for maintaining regulatory compliance and protecting sensitive information. These reviews help organizations validate access rights, detect policy violations, and address risks before they lead to audit failures or data breaches.
Importance of Access Reviews in Cybersecurity Compliance
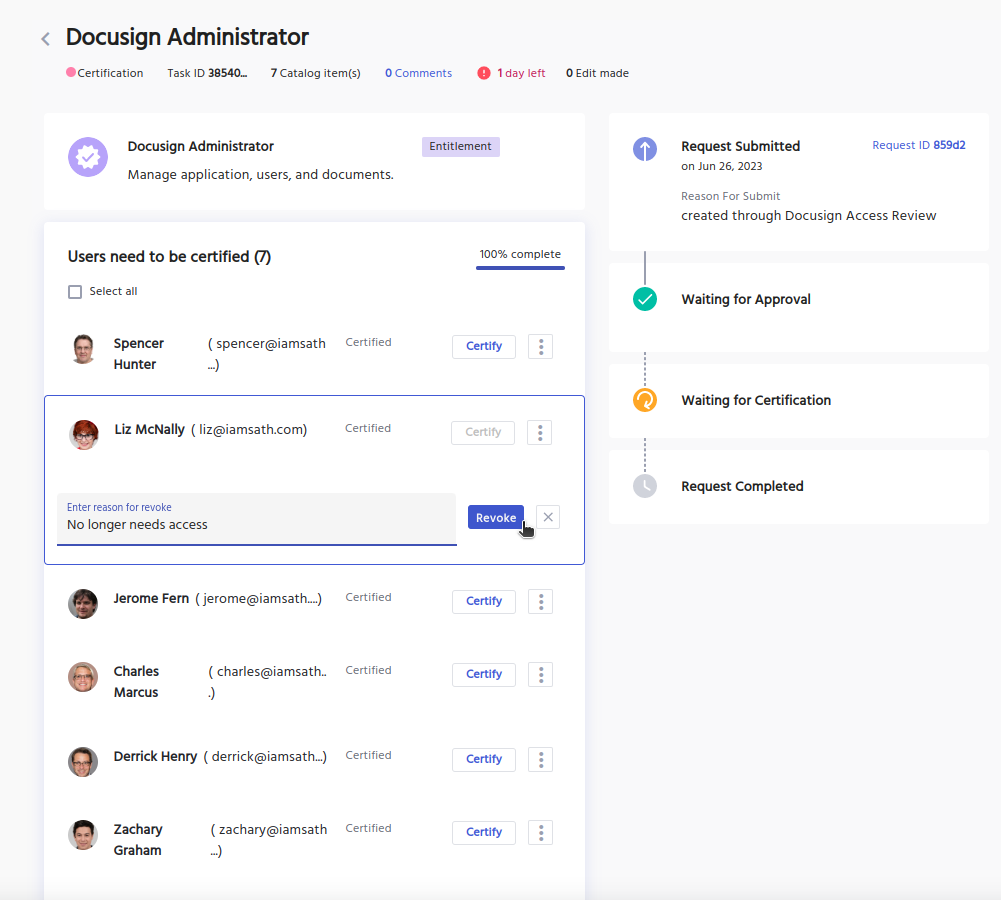
Routine access certifications ensure users have appropriate access based on their roles, reducing the risk of over-permissioning. These reviews are often required under regulatory standards such as HIPAA, SOX, PCI-DSS, and NERC-CIP.
Tag-Based Access Certification by Regulatory Framework
IDHub simplifies the review process with tag-based functionality that maps applications and permissions to specific compliance requirements.
Regulatory Tags for Access Review Automation
Organizations can tag users, applications, and entitlements by framework (e.g., HIPAA, NERC-SIP), enabling faster, targeted access certifications and compliance reporting.
Explore how IDHub uses tagging to streamline compliance:
Identity Access Reporting and Compliance Analytics
Identity and Access Management (IAM) reporting is vital for maintaining regulatory compliance, auditing user activity, and detecting access risks across your organization. These analytics tools help organizations in highly regulated industries monitor access trends, enforce security policies, and pass audits with confidence.
Monitor User Access and Meet Compliance Requirements
By analyzing identity management data, organizations can:
- Detect anomalies in user access patterns
- Identify compliance violations and access risks
- Optimize provisioning and deprovisioning workflows
- Generate audit-ready reports for HIPAA, SOX, PCI-DSS, and more
Out-of-the-Box and Custom IAM Reports
IDHub includes a wide range of pre-built reports tailored to compliance standards and access control metrics. It also supports custom report creation through JS Reports, enabling detailed visibility into identity governance performance.
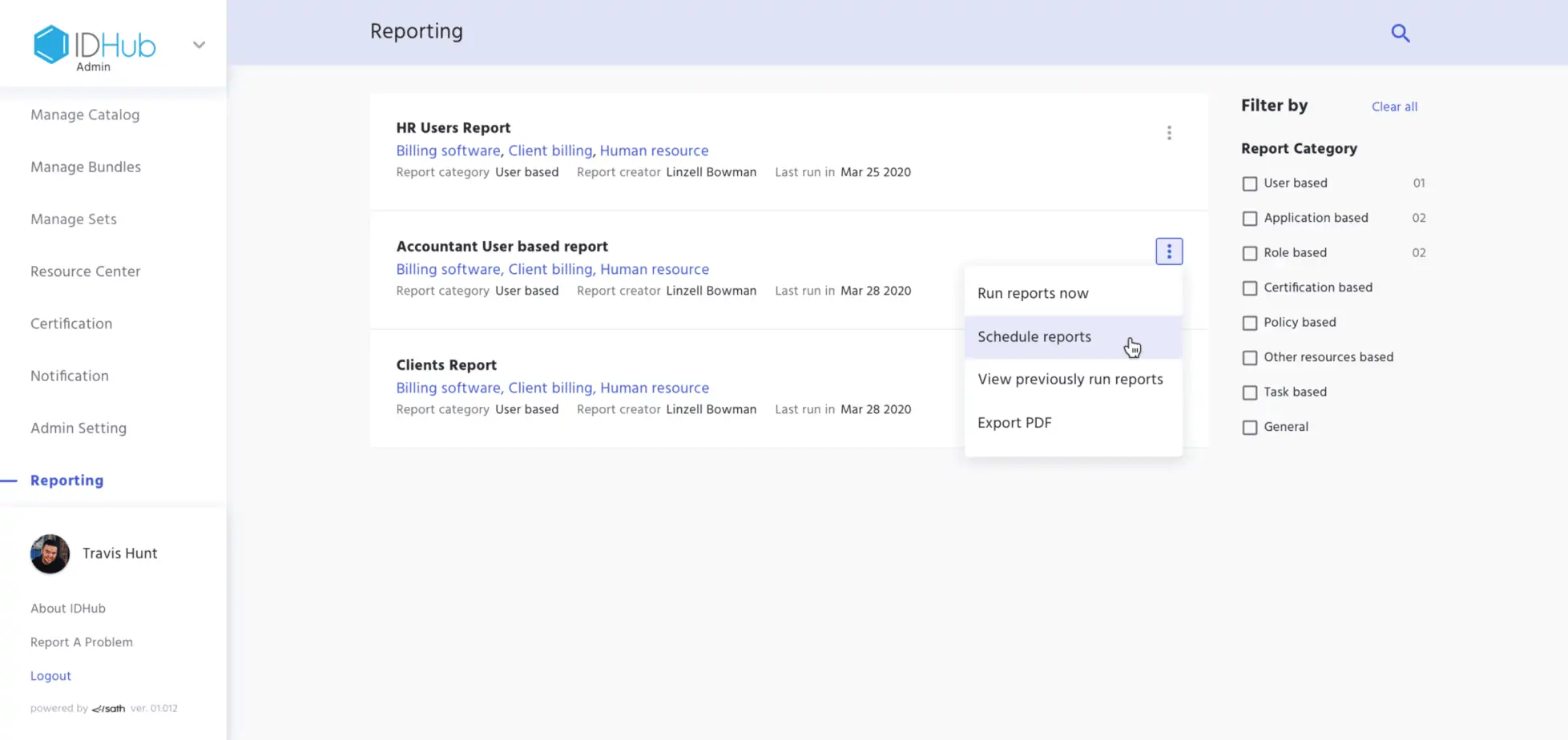
Identity Access Review and Audit Reporting Demo
Watch this IAM tutorial video to learn how IDHub simplifies user access reviews and audit reporting for regulatory compliance. See how organizations can:
- Automatically verify role-based access
- Identify excessive or outdated permissions
- Generate audit-ready compliance reports in minutes
Ensure your users have only the access they need—and nothing more—while meeting standards like HIPAA, SOX, PCI-DSS, and GDPR.
Secure your data
Data Encryption Methods
Transit Encryption
IDHub supports encryption of data in transit using Transport Layer Security (TLS) protocol. This ensures secure communication between IDHub and the client server.
Data Encryption
IDHub provides encryption and decryption services for data at rest. It allows you to encrypt sensitive data, such as passwords, API keys, and certificates, using various encryption algorithms and key management strategies.
Key Management
IDHub offers a secure key management system that enables you to generate, rotate, and revoke encryption keys. It supports symmetric and asymmetric key encryption methods.
Key Wrapping and Unwrapping
IDHub allows you to wrap and unwrap encryption keys. Key wrapping involves encrypting a key with a master key, while key unwrapping is the reverse process of decrypting a wrapped key.
Dynamic Secrets Encryption
IDHub supports dynamic secrets, where it generates short-lived credentials for various systems, databases, and APIs. These dynamic secrets are encrypted and managed securely by IDHub.
Key Encryption and Transit Encryption
IDHub separates key encryption and transit encryption. You can encrypt keys with one encryption method and use a different encryption method for transit encryption, providing flexibility and security.
Secure Service Mesh
IDHub integrates with service mesh technologies, to provide encryption and secure communication between services. It enables encrypted communication channels and mutual TLS authentication between services in a distributed environment.
Encryption of Key-Value Store
IDHub's key-value store can be configured to encrypt data at rest. This ensures that sensitive configuration data stored in IDHub key-value store is encrypted and protected from unauthorized access
Identity and Access Management (IAM)
Security and Compliance
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.

The Price of Identity Access Management
Why is IAM so expensive? Learn how the benefits outweigh the initial price tag in our post on Identity and Access Management, and why it seems like a high ticket.