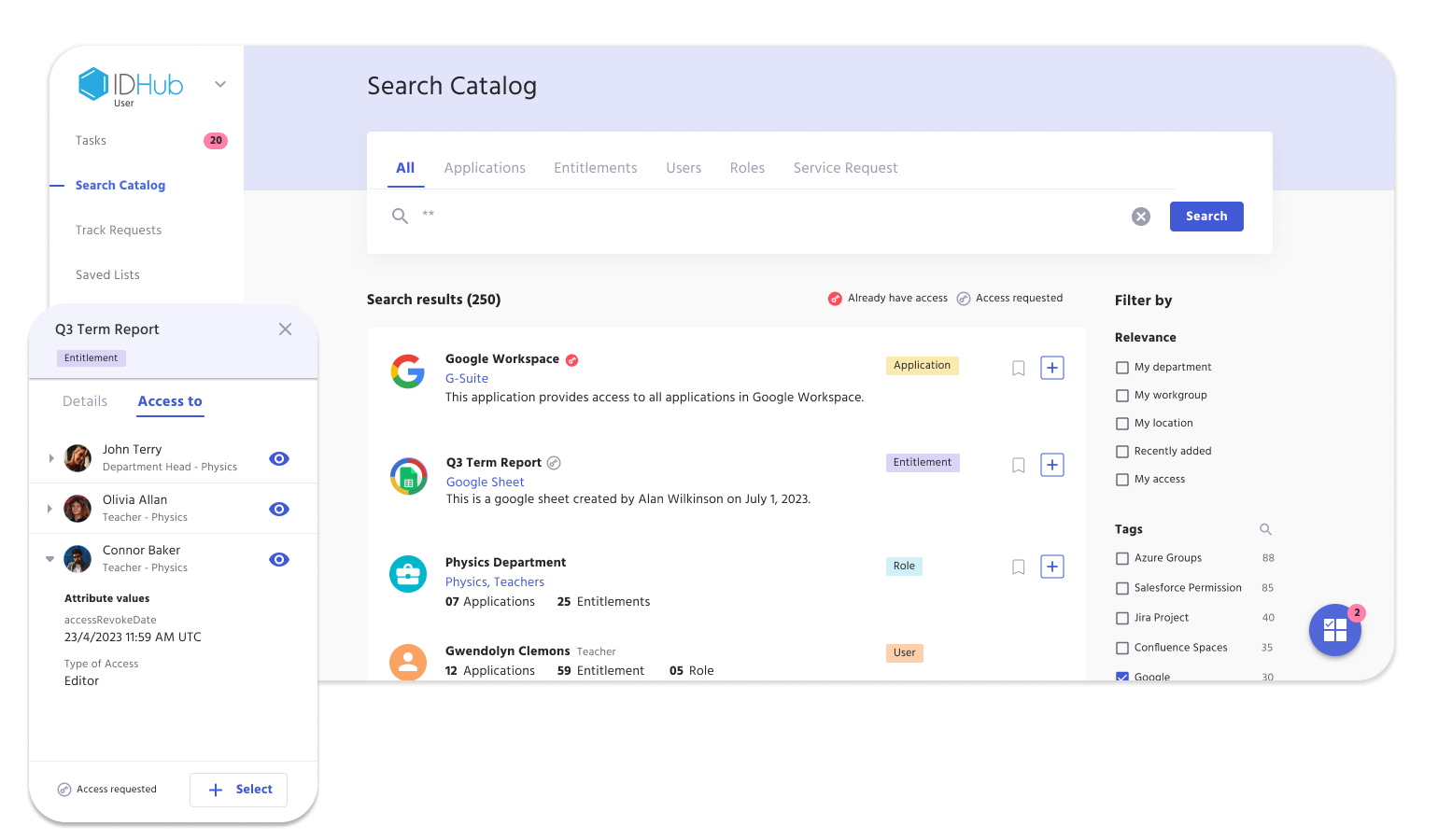
Identity Security
Faculty, staff, and students demand fast, seamless access to campus applications and data—but institutions must also meet strict regulatory obligations like FERPA, GDPR, and COPPA. Manual processes can’t keep up with complex user affiliations and compliance mandates.
IDHub’s identity security platform simplifies compliance and reduces risk by:
Automating Regulatory Controls
Enforce FERPA and GDPR access rules with built-in policies, real-time auditing, and reporting that’s always audit-ready.
Streamlining Role-Based Access Control (RBAC)
Automatically provision, adjust, or revoke access as users change roles, ensuring compliance and reducing administrative overhead.
Simplifying User Interaction
Offer self-service access requests and password resets—reducing IT burden while keeping access secure and compliant.
Maintaining Central Oversight
Gain visibility with a single-pane of glass into who has access to what, and ensure access policies are enforced across cloud and on-prem systems.
Comply with FERPA & GLBA Regulations
IDHub delivers centralized authentication and authorization to ensure secure access to sensitive student education records. By enforcing robust password policies and multi-factor authentication, it significantly reduces the risk of unauthorized access.
With role-based access control (RBAC), IDHub limits users to only the information necessary for their specific responsibilities, supporting compliance with regulations such as FERPA and GLBA.
Additionally, its detailed auditing and reporting capabilities provide continuous visibility into who accesses student data and when, facilitating audit readiness and regulatory adherence.
Together, these features empower your institution to maintain strong data protection while simplifying compliance management across campus systems.
Higher Education Cyber Security
Colleges and universities are prime targets for cyberattacks, facing threats from ransomware, phishing, and insider misuse. With growing digital footprints and diverse user populations—from students and faculty to contractors and alumni—higher education institutions must protect sensitive research, student data, and institutional systems while navigating complex access requirements.
A modern identity and access management (IAM) strategy helps institutions:
Strengthen Campus-Wide Security
Apply identity-based controls across networks, applications, and learning systems to mitigate data breaches and unauthorized access.
Unify Security for Hybrid Learning
Protect access across on-campus, remote, and hybrid environments with consistent, policy-based identity controls.
Manage Complex User Roles
Streamline role assignments for users who serve multiple functions—like students who are also research assistants or part-time staff.
Support a Zero Trust Approach
Implement strong verification practices and privileged access management (PAM) to reduce insider threats and ensure access is only granted when needed.
Cybersecurity in higher education isn’t optional—it’s foundational. Identity governance and Identity and Access Management (IAM) provides the visibility and control needed to defend your institution against evolving threats.
Benefits
Facilitate secure user access
Boost user satisfaction with fast access
Empower staff and students to complete tasks themselves with self-service access requests and password resets.
Reduce IT burden and cost effectively
Automate time-intensive provisioning and deprovisioning. Spend less time managing your identity program easily.
Improve compliance and audit performance
Stay compliant with regulations including FERPA, GDPR, and CCPA and improve audit performance with automated policies.
Reduce risk of data breaches exponentially
Prevent risk from overprovisioning and turn vast amounts of identity data into actionable insights so you can spot potential risks faster.
Secure identities with multiple affiliations
Manage access with multiple authoritative sources within complex higher education user populations. Secure individuals with one-to-many roles.
Increase visibility into every resource
Get a 360 degree view into user populations with diverse identities including applicants, students, alumni, faculty, staff etc.
Compliance Tools for Cyber Security
Cyber Security Tools
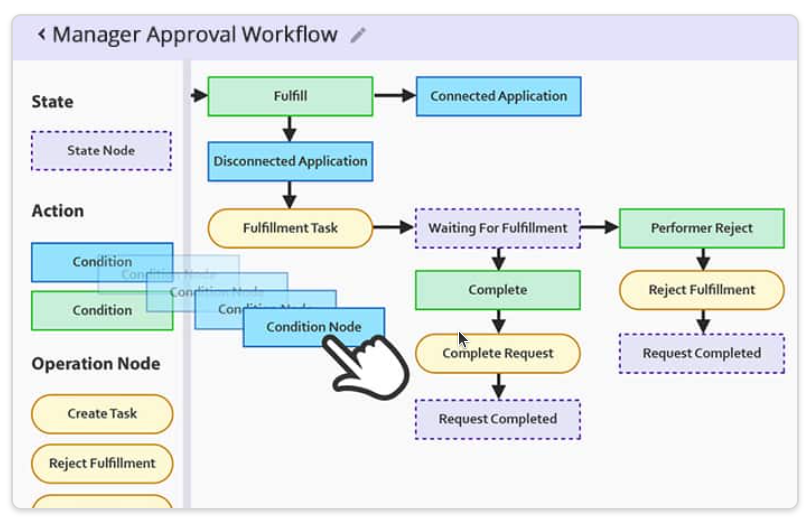
Customizable Approval Workflow Templates
Download our most common Workflow Templates, including editable versions in Visio, SVG, and PDF formats. Completely free to you.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.