What Is Role Based Access Control?
Identity and Access Management (IAM) Role Based Access Control (RBAC) is an effective security framework that enables organizations to efficiently manage access rights within their IT systems.
RBAC is a feature of IAM systems that secure the access of users to certain resources or applications on the basis of their individual roles within an organization. This system helps organizations maintain an appropriate level of security by limiting user access to the resources they need for their job roles.
RBAC meaning is to simplify and streamline access control processes, done by mapping users, or groups of users, with specific roles, and assigning privileges based on that role.
As a result, organizations can quickly grant or restrict access rights on an individual basis without having to go through a lengthy authorization process.
This not only helps to improve security, but also saves time and resources by reducing the amount of manual work required for access control processes.
Role-Based Access Control in IDHub
IDHub Role Based Access is a flexible and powerful tool used to assign resources to users based on their attributes.
IDHub admins are the only users who have access to the Role Based Access tool.
Below are the features available to admins:
- Wizard-Based Role Creation
- Conditional Based Role Queries
- Birthright Roles
- Bulk Role Upload Tool
- Manage Roles
- Easy Creation With No Technical Experience Needed
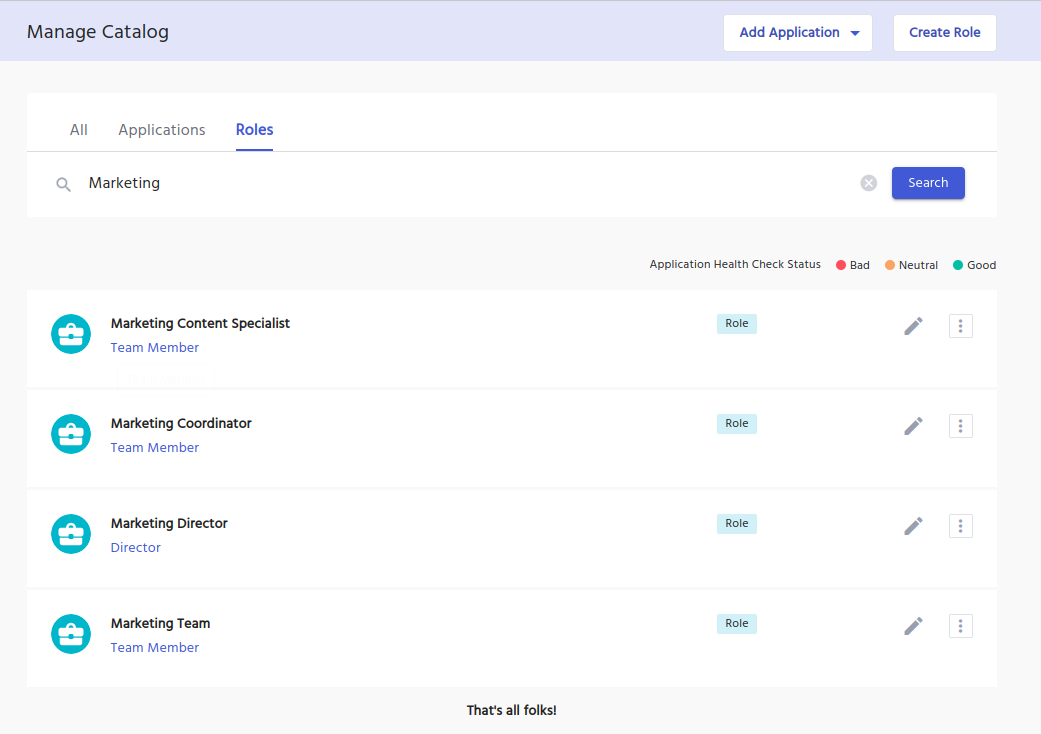
Access Requests
Roles can be configured so users can request access to them via an Access Request from the Search Catalog Page.
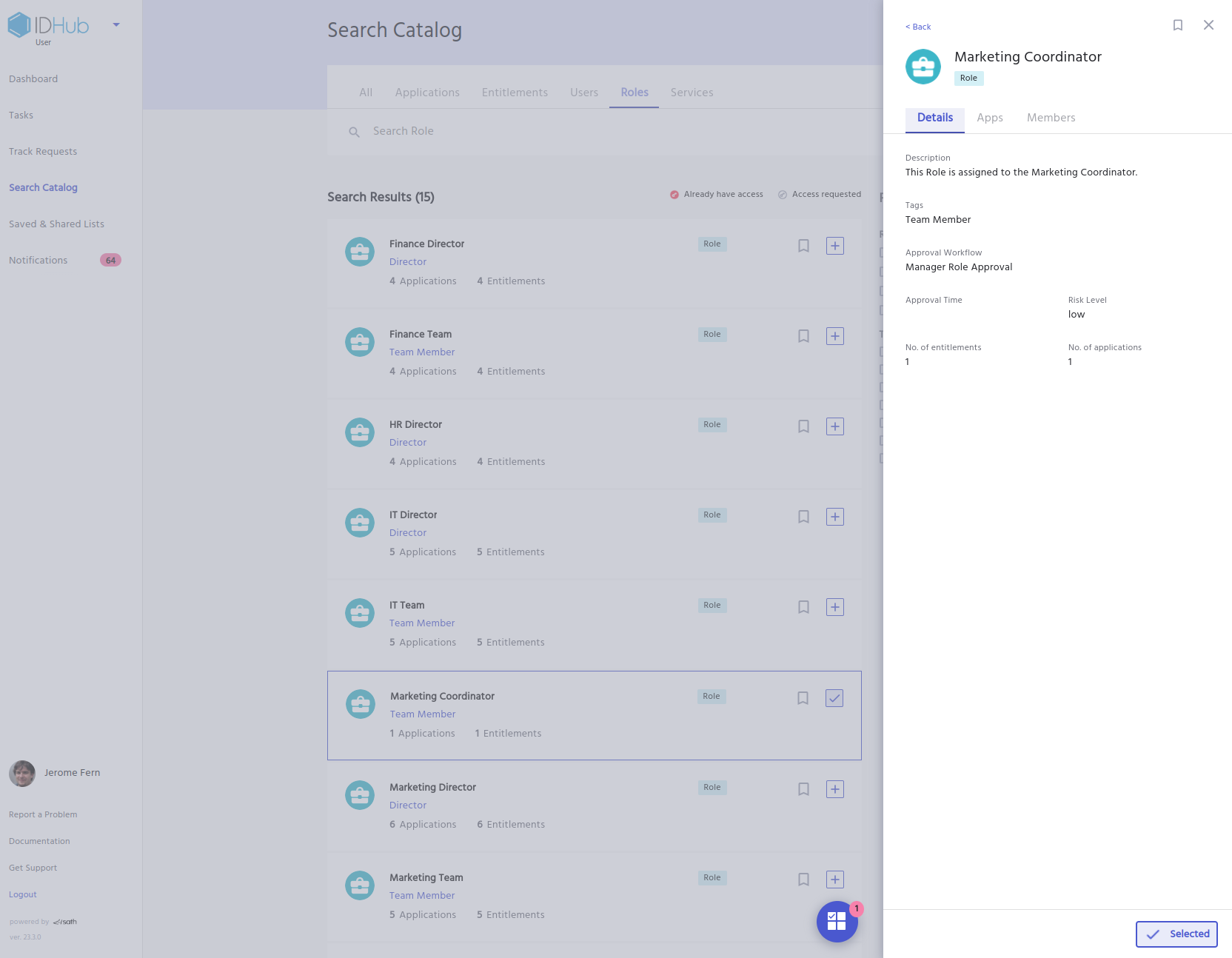
Birthright Access
IDHub makes it easy to manage role based permissions by providing an option to automatically assign a set of roles while onboarding all users as birthright access.
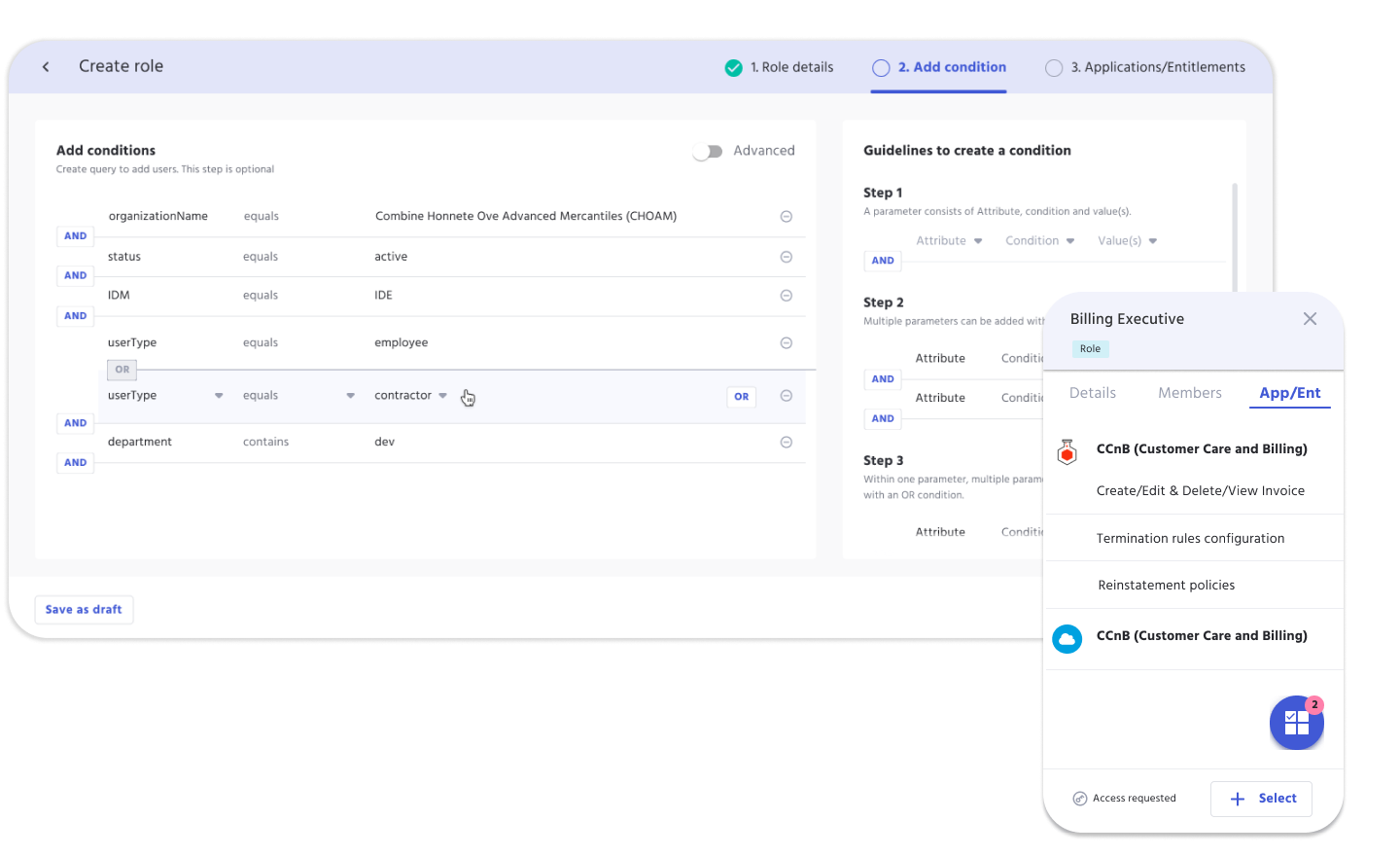
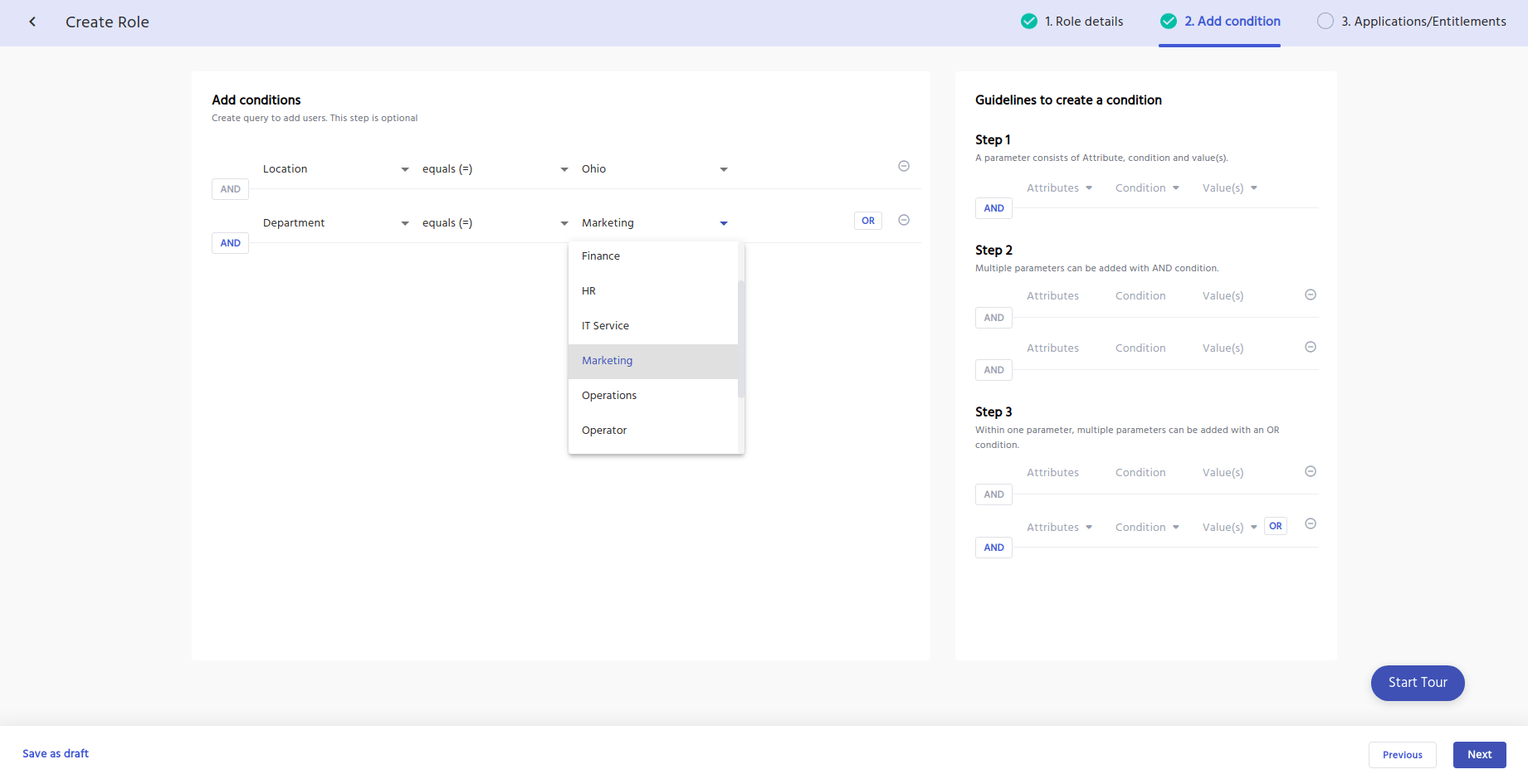
Taking it a step further, IDHub has an advanced role condition feature.
Role Conditions assist with determining various scenarios through a configured set of rules or conditions.
IDHub uses conditional rules to automatically assign birth right access to newly onboarded users with the role condition query.
This query allows for multiple conditions using and/or to form the query.
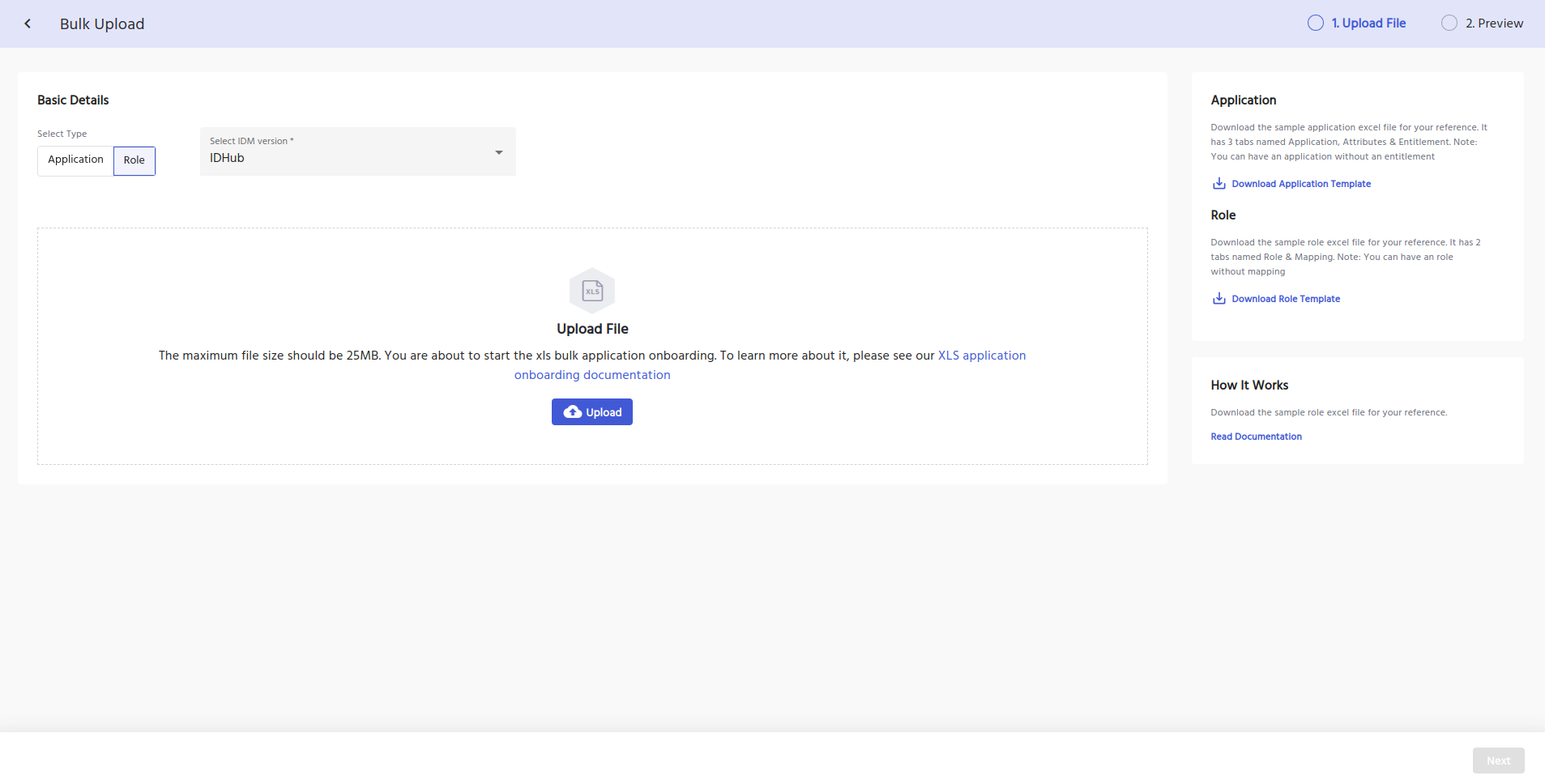
IDHub Bulk Role Upload
IDHub offers a unique Bulk Role Upload feature, that allows admin to quickly and efficiently upload multiple roles in a few simple clicks, saving valuable organizational time and resources.
The bulk upload feature provides admins with a CSV template for easy data entering.
Admins can easily follow our IDHub how to guide, to ensure accuracy while perform the upload.
Role Based Access Control Vs Attribute Based Access Control
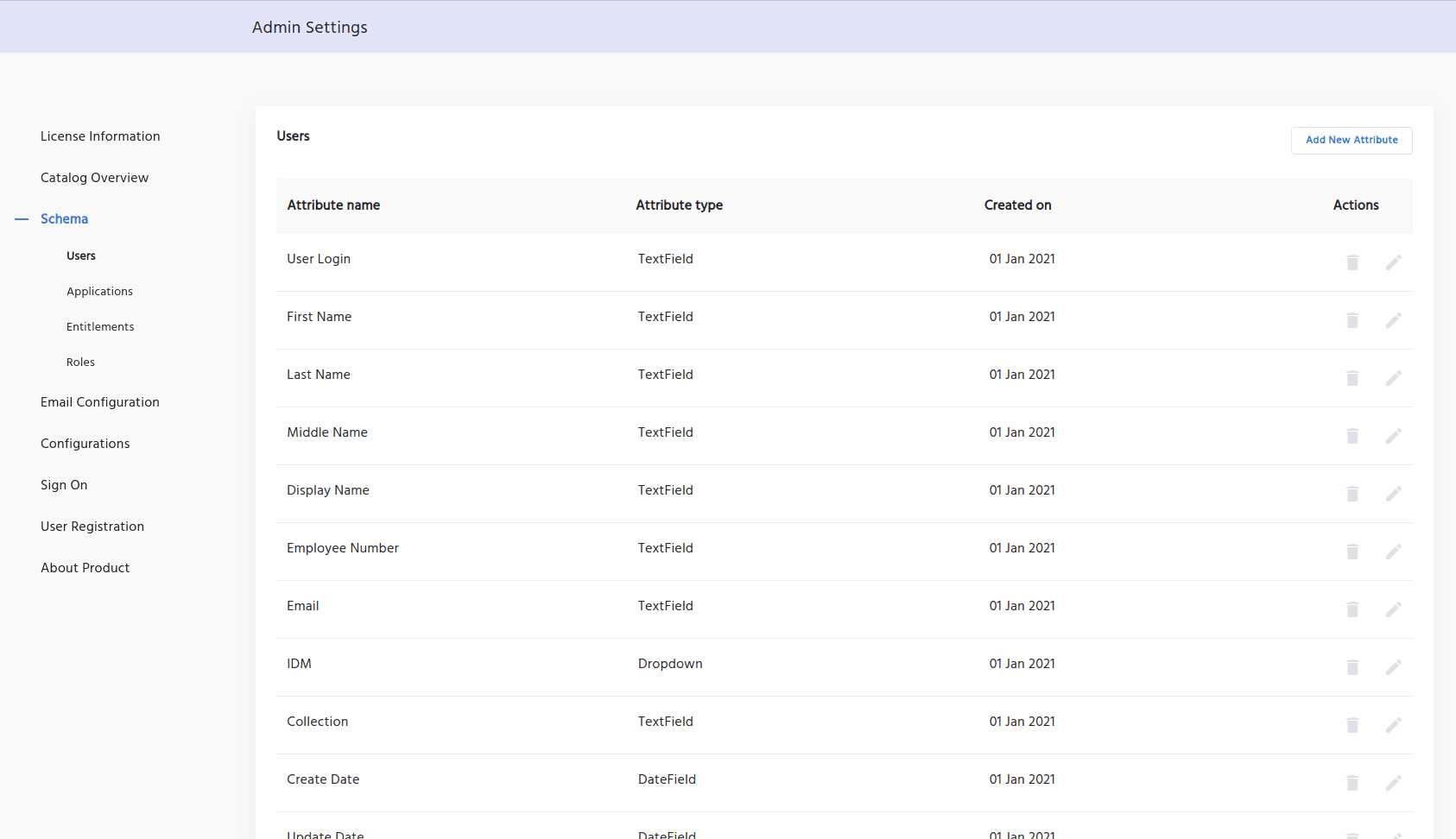
Attribute-Based Access Control (ABAC) varies slightly from Role-Based Access Control (RBAC). RBAC provides user access to resources, based on Role assignment, where ABAC provides user access to resources, based on resource attributes and user attributes.
However IDHub can accommodate both simultaneously.
This added layer of security allows systems to have more granular control over its users, and protect against outsiders using a compromised user account maliciously.
IDHub includes many out-of-the-box schema attributes. Any custom attribute can be created and added to the schema.
Location Based Access Control
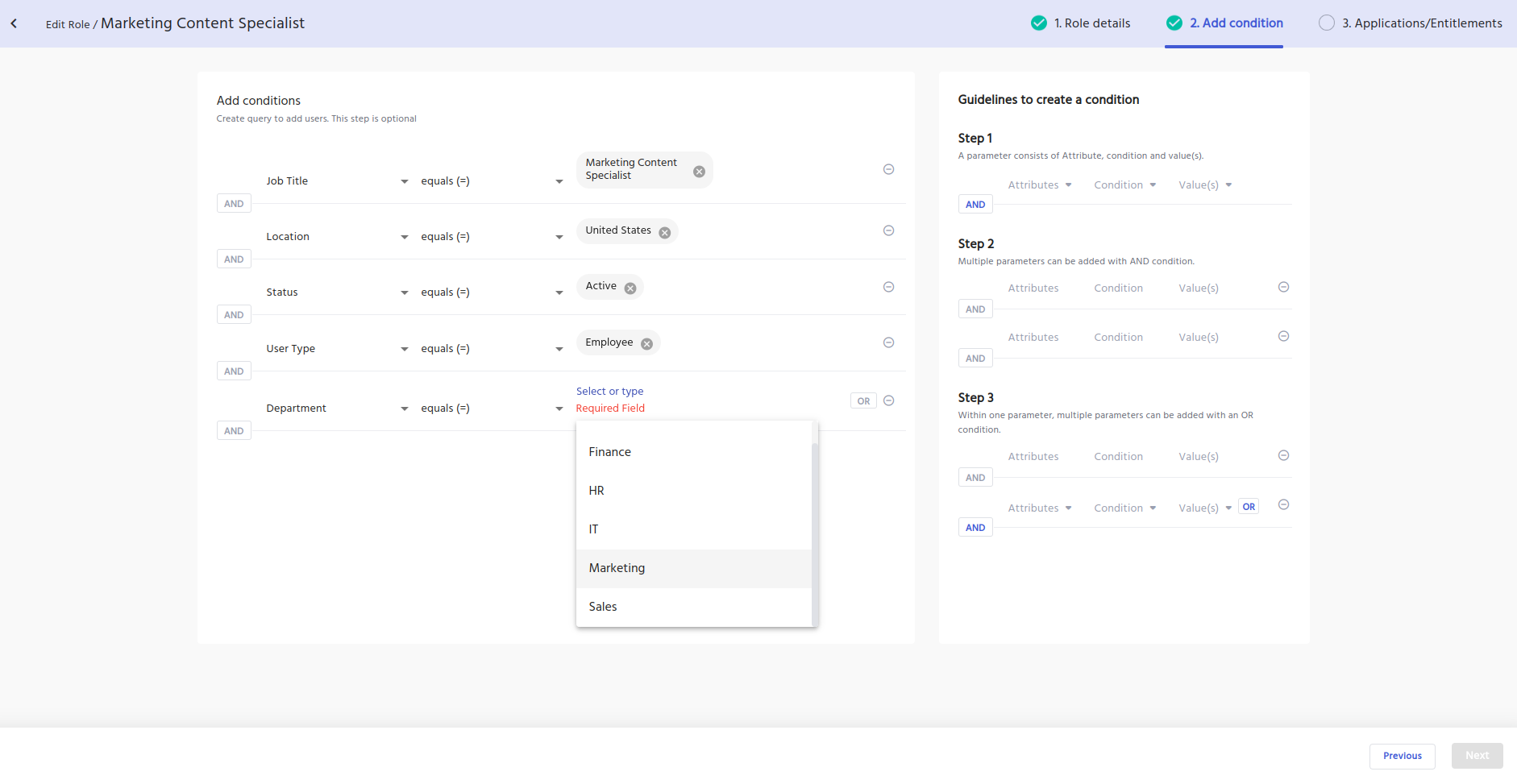
Suppose a user is newly onboarded, has a job title change, a department change, or a location change.
IDHub will recognize the user attribute change, and automatically grant or revoke Role access according to the conditions configured within the Roles.
IDHub matches the resource attributes within the Role, against the user account information, then appropriately provisions or deprovisions the resources which are assigned to the Role.
Role Based Permissions
Role-based permissions refer to the practice of assigning access rights and privileges to users based on their roles within an organization.
Instead of granting permissions to individual users, permissions are associated with specific roles, and users are then assigned to those roles.
This approach simplifies access control and administration, as users with similar responsibilities or functions share a common set of permissions tied to their roles, making it easier to manage and maintain security.
Role Based Access Control Best Practices
These key best practices help organizations establish and maintain an effective Role-Based Access Control system, enhancing security and access management.
- Clear Role Definitions: Clearly define roles based on job responsibilities and functions.
- Least Privilege Principle: Assign the minimum necessary permissions for each role to reduce the risk of unauthorized access.
- Access Reviews: Periodically conduct an access review, ensuring role assignments align with organizational changes.
- Segregation of Duties (SoD): Avoid conflicts by ensuring that no single role has conflicting or sensitive permissions.
- Single Pane Of Glass: Manage roles centrally to ensure consistency across systems and applications.
- Compliance and Reporting: Implement robust logging, auditing, and monitoring to track role changes and detect security incidents.
- User Lifecycle Management: Develop effective processes for onboarding, offboarding, and role changes to maintain accurate access control.
- Use Connectors to help automate the provisioning to user accounts with Roles.
Compliance Tools for Cyber Security
Cyber Security Tools
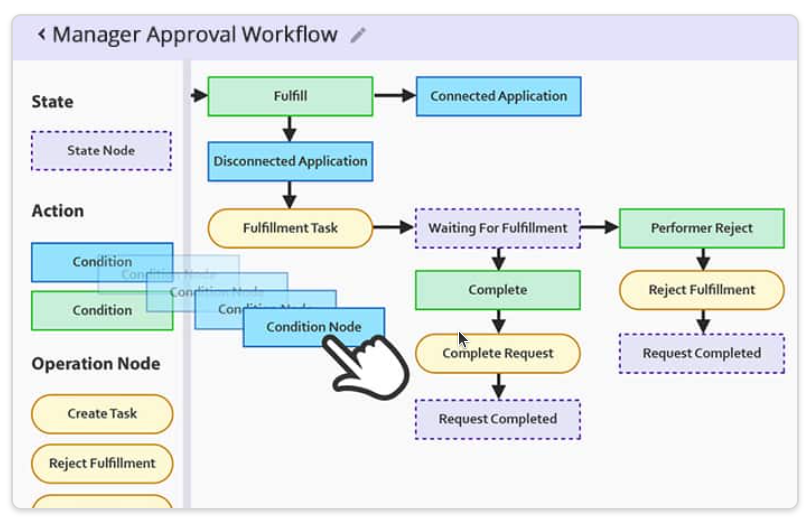
Customizable Approval Workflow Templates
Download our most common Workflow Templates, including editable versions in Visio, SVG, and PDF formats. Completely free to you.
Cybersecurity Assessment Template
Discover why cybersecurity assessments are vital for regulated industries—plus a free template to strengthen security, manage risk, and stay compliant.

Access Control Policy Template for Organizations
Utilize our free Access Control Policy Template to help establish a healthy framework for your access control. Easy to customize and share with your team.