Introduction to Healthcare IAM
Did you know healthcare data breaches are the most expensive of all industries? While the average breach in 2023 costs $4.45 million, in healthcare, it jumps to $10.93 million—a 53.3% increase in just three years!
Protecting patient data is more critical than ever, and that's where Identity and Access Management (IAM) comes in. IAM helps keep sensitive information safe, ensures compliance with regulations, and makes workflows more efficient. In this post, you’ll see how IAM can boost security and streamline operations in your healthcare organization, along with practical steps for implementation and the benefits of regular access control reviews.

Identity and Access Management in Healthcare
Identity and Access Management (IAM) is a framework of policies and technologies designed to ensure that the right individuals have appropriate access to technology resources. In simpler terms, it’s about ensuring that only authorized people can use specific systems and data and that their access is properly managed and monitored.
An IAM system typically includes several key components. These include user authentication, which verifies the identity of a person trying to access a system, and user authorization, which determines what that person can do once inside.
Other components are user and identity management, which involves adding, updating, and removing user accounts and access governance, ensuring access rights are granted and reviewed according to policy. These components and identity solutions work together to secure sensitive information and ensure that only the right people can access it.
Healthcare organizations have unique needs for IAM due to the sensitive nature of patient data and the strict regulatory requirements they must adhere to. They need robust systems to protect electronic health records (EHRs), ensuring that patient information is kept confidential and secure.
Additionally, healthcare IAM systems must support compliance with HIPAA, HITECH, and GDPR regulations, which mandate strict controls over who can access patient information and how it is protected. This means healthcare IAM systems must be highly reliable, easy to use, and capable of managing many users with varying access levels.
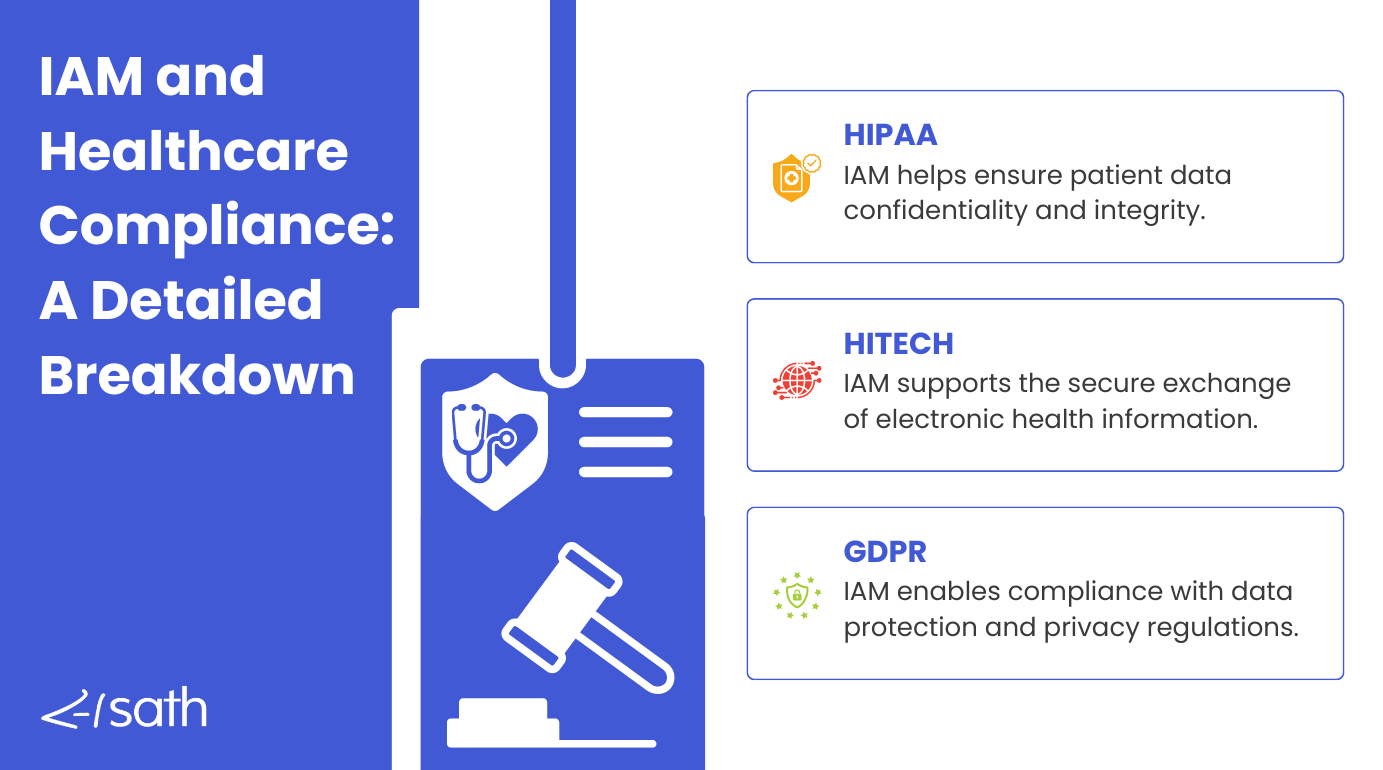
Regulatory Compliance in Healthcare
If you work in healthcare IT, you’re probably familiar with the alphabet soup of regulations: HIPAA, HITECH, GDPR, and more. These laws are all about protecting patient information.
HIPAA, for instance, sets the standard for protecting sensitive patient data in the U.S., while HITECH promotes the adoption of electronic health records with strict privacy and security rules.
GDPR is a European regulation that protects data and privacy for individuals in the EU. These regulations require healthcare organizations to safeguard patient data and ensure it’s handled properly. Compliance with these regulations is crucial in preventing healthcare data breaches.
IAM plays a huge role in helping healthcare organizations comply with these regulations. By managing who has access to what information, IAM ensures that only authorized individuals can access sensitive patient data.
It helps to keep track of access patterns and can quickly revoke access when someone leaves the organization or changes roles. This protects patient data preventing unauthorized access and helps your organization avoid hefty fines and legal trouble.
How IAM systems help ensure compliance
First, they provide user authentication, ensuring that anyone trying to access patient data is who they say they are. This typically involves passwords, biometrics, or multi-factor authentication, adding multiple layers of security.
Second, IAM systems handle user authorization, ensuring that users can only access the information they need for their role once authenticated. This minimizes the risk of data breaches by using identity governance and limiting access to sensitive information.
Moreover, IAM systems support access reviews and audits. Regular access reviews ensure that only current employees who need access have access. IAM systems can automate these reviews, making the process more efficient and less prone to human error.
They also generate detailed logs and reports of who accessed what information and when. This is incredibly useful during audits, providing clear evidence of regulation compliance.
Protecting Patient Data with IAM
As an IT professional in healthcare, you understand just how sensitive patient data is. Keeping this information secure isn’t just about following regulations—it’s about protecting the privacy and trust of the patients who rely on your organization.
Data breaches of healthcare data can have severe consequences, from financial penalties to damaged reputations and, most importantly, the potential harm to patients if their personal health information is misused.
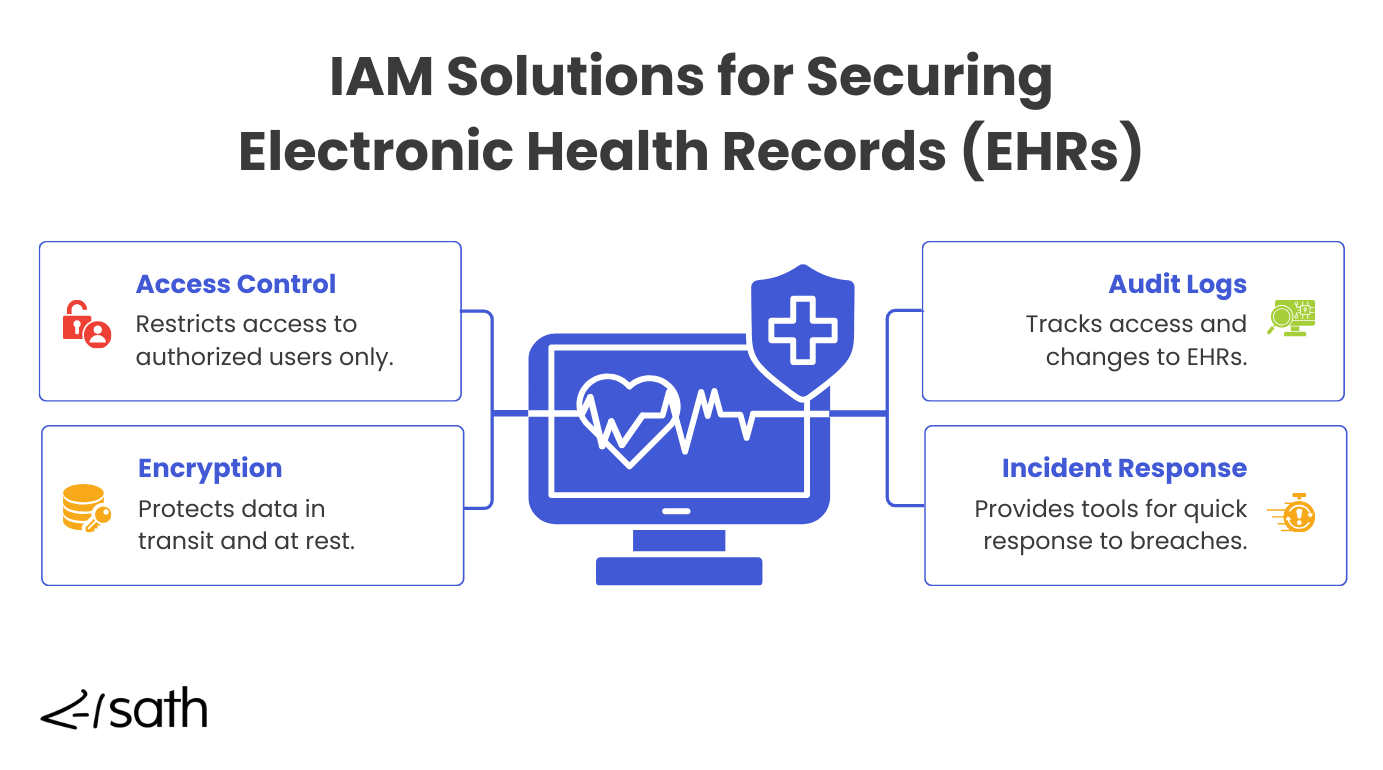
How IAM helps secure Electronic Health Records (EHRs)
IAM systems are key to securing EHRs by using access management solutions ensuring only authorized users can access sensitive patient data. They help prevent unauthorized access, monitor user activities, and provide a quick response to security incidents. Here’s how IAM solutions enhance EHR security:
- Access Control: Ensures that only authorized users can access sensitive patient data, reducing the risk of unauthorized access and data breaches.
- Encryption: Protects data both when it’s being transmitted and when it’s stored, ensuring that even if data is intercepted or accessed by unauthorized users, it remains unreadable.
- Audit Logs: Keeps detailed records of who accessed or modified EHRs and when, providing valuable insights for detecting suspicious activities and supporting compliance efforts.
- Incident Response: Provides tools and protocols to quickly identify, contain, and mitigate security breaches, minimizing the potential impact on patient data and organizational operations.
Real World Healthcare Data Breaches
Anthem Data Breach
In 2015, Anthem, a major health insurance company, experienced a data breach that exposed the personal information of nearly 80 million individuals. The breach was attributed to compromised credentials, which allowed unauthorized access to their systems.
An effective IAM system could have prevented this breach by implementing stronger authentication methods such as multi-factor authentication (MFA). Additionally, strong access controls would have restricted access to sensitive data, ensuring that only those with legitimate needs could access it.
Premera Blue Cross Data Breach
Premera Blue Cross suffered a data breach in 2014, affecting 11 million customers. Hackers gained access to their network and remained undetected for months. An IAM system could have mitigated this by providing continuous monitoring and real-time alerts for suspicious activities.
Encryption would have protected data, making it useless to unauthorized users even if accessed. Incident response tools within an IAM framework facilitated a quicker and more effective response, potentially minimizing the extent of the breach.
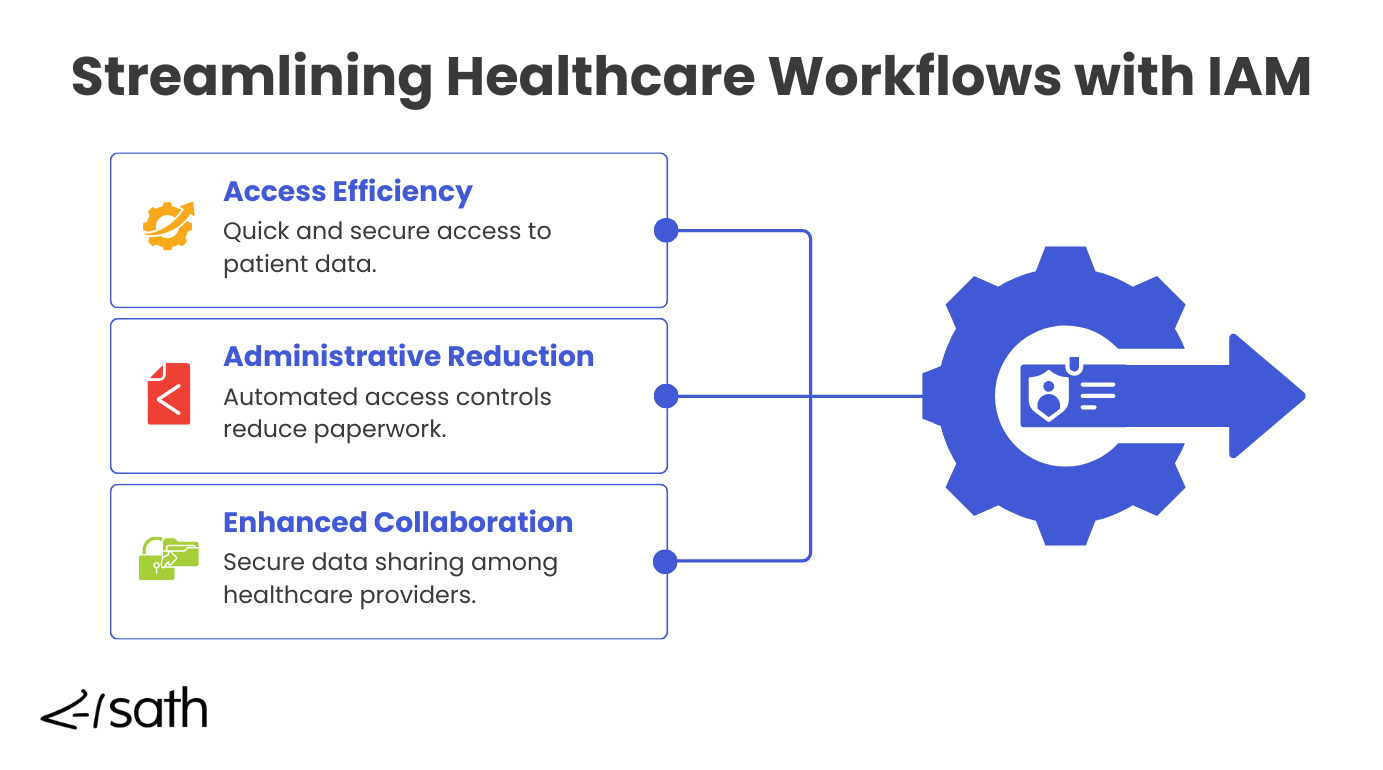
Workflow Efficiency Through IAM
In healthcare, inefficient workflows can be a major pain point, leading to delays, frustration, and potential patient care risks. Managing access to sensitive information often means juggling multiple systems and credentials, which can slow down processes and divert attention from patient care. This is where IAM can make a significant difference, streamlining operations and allowing healthcare professionals to focus more on what matters most – their patients.
Streamlining Access to Patient Data
Healthcare professionals need quick and seamless access to patient data to provide timely and effective care. IAM systems streamline this process by providing single sign-on (SSO) capabilities, reducing the need to remember multiple passwords and logins. This means less time spent on accessing records and more time dedicated to quality patient care, improving overall efficiency in healthcare delivery.
Reduce Administrative Burden with Automated Access Controls
Manual user access can be a huge administrative burden, leading to errors and delays. IAM systems automate and manage control access, ensuring permissions are granted and revoked automatically based on predefined policies. This reduces the workload on IT staff, minimizes the risk of human error, and ensures that access rights are always up-to-date, enhancing security and operational efficiency.
Enhancing Collaboration Through Secure Data Sharing
Effective collaboration among healthcare providers is essential for delivering comprehensive patient care. IAM systems enable secure access and data sharing by ensuring only authorized individuals can access shared information. This promotes better coordination and communication among healthcare teams, improving patient outcomes and more efficient use of resources. With secure and streamlined access, healthcare providers can work together more effectively, no matter where they are.
Access Reviews and Auditing
Without regular access reviews and visible auditing, healthcare organizations face significant risks. Unauthorized access to sensitive patient data can lead to data breaches, legal issues, and a loss of patient trust. It can also make detecting and responding to security incidents difficult. Regularly reviewing who has access to what information is essential to maintain security and compliance.
Regular access reviews are important in healthcare to ensure that only the right people can access sensitive patient information. These reviews help identify outdated or unnecessary access rights that could pose security risks. Healthcare organizations can better protect patient data and comply with regulatory requirements by routinely checking and updating access permissions.
How IAM Systems Facilitate Automated and Efficient Access Reviews
Identity and Access Management (IAM) systems automate the process, making access reviews much easier and more efficient. They provide tools that regularly check access permissions against current roles and responsibilities, automatically flagging discrepancies.
This automation reduces IT staff's workload, minimizes human error risk, and ensures that access rights are always accurate and up-to-date. IAM systems also generate detailed reports, making it simpler to demonstrate compliance during audits and ensuring that all other access management programs and activities are transparent and well-documented.
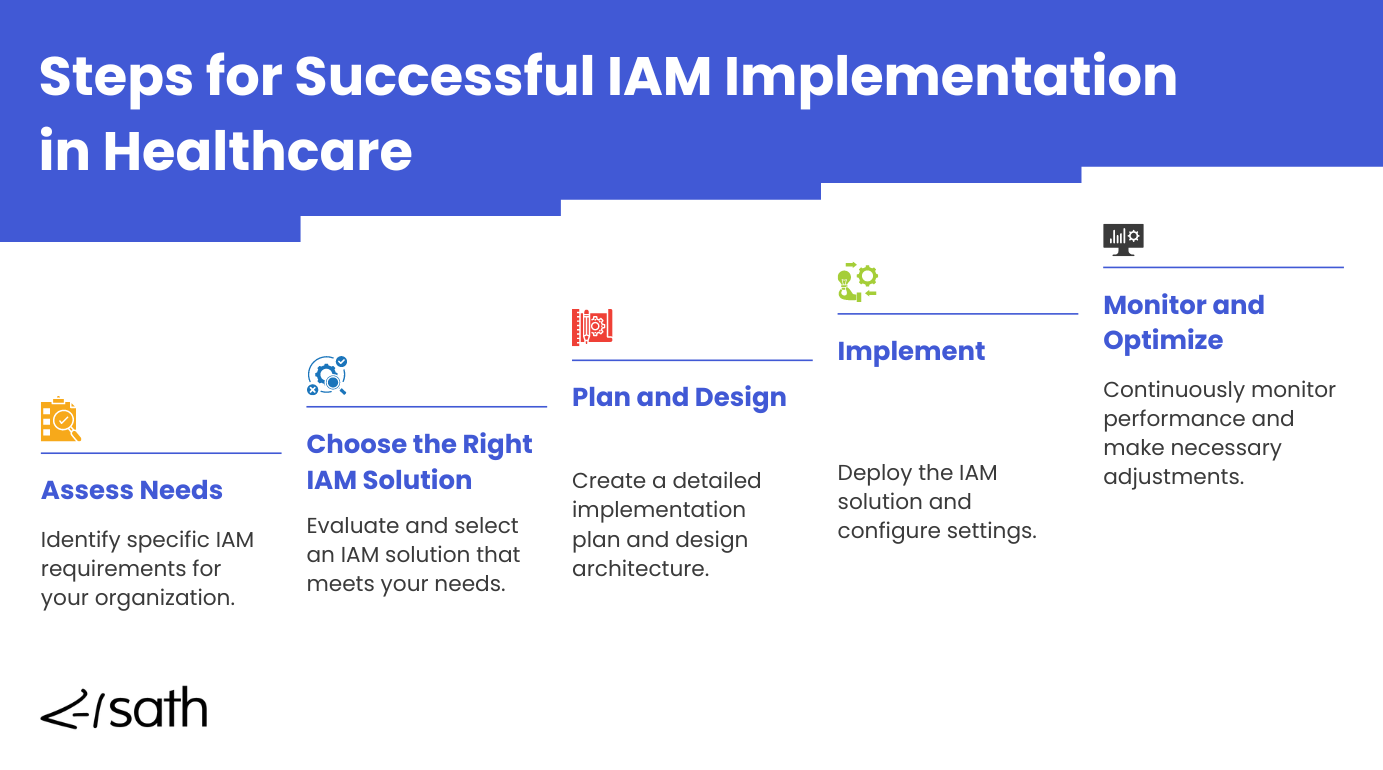
Implementing IAM in Healthcare
When implementing IAM in healthcare, it’s essential to consider your organization’s unique needs. You need a solution that secures patient data and integrates seamlessly with your existing systems and workflows.
It’s important to involve key stakeholders from the beginning to ensure that the next IAM healthcare solution meets the needs of all users, from IT staff to healthcare professionals. To ensure a seamless transition to an IAM solution, follow these steps:
- Assess Needs: Identify your organization’s specific IAM requirements. Consider the types of data you need to protect, regulatory requirements, and user groups that will need access.
- Choose the Right IAM Solution: Evaluate and select an IAM solution that meets your needs. Look for a solution that offers flexibility, scalability, and strong security features, and make sure it can integrate with your current systems.
- Plan and Design: Create a detailed implementation plan and design architecture. Define clear goals, timelines, and responsibilities, and ensure all stakeholders are on the plan. Incorporate identity solutions to manage identity risk and safeguard patient information effectively.
- Implement: Deploy the IAM solution and configure settings. This includes setting up user roles, permissions, and policies and ensuring that all systems and applications are properly integrated.
- Monitor and Optimize: Continuously monitor performance and make necessary adjustments. Review and update access controls regularly, look for unusual activity and adjust the system to ensure optimal performance and security.
Conclusion
To sum it up, IAM solutions bring a lot of benefits to healthcare companies. They help you stay compliant and accurate with reporting, make access reviews easier, simplify your workflows, boost security, and improve overall efficiency. Integrating IAM solutions into your strategy is crucial for staying ahead of security threats and keeping everything running smoothly. Ready to enhance your security and compliance? Contact Sath today to schedule a consultation and see how our IAM solutions can meet your needs and transform your operations.