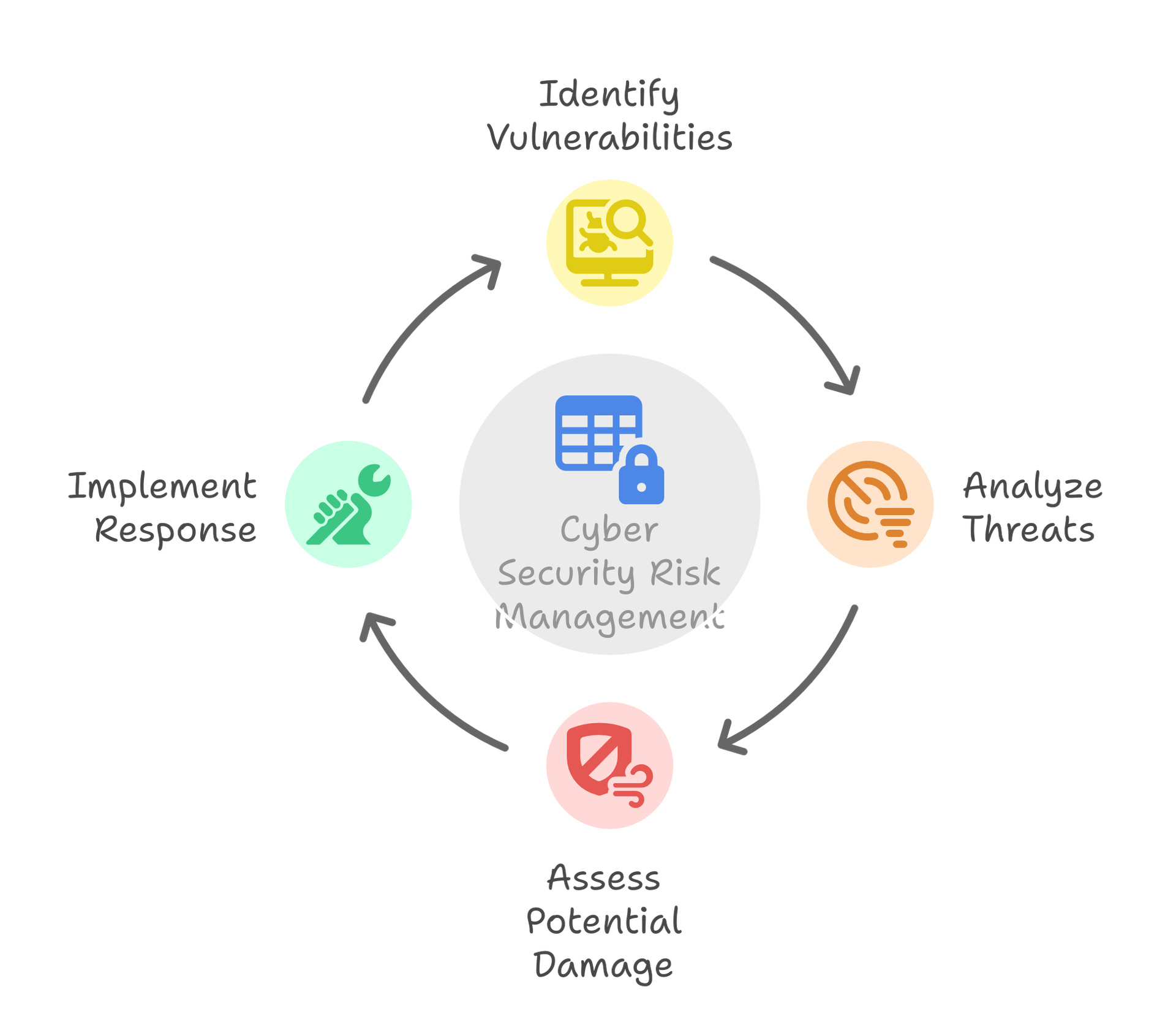
What is Cyber Security Risk Management?
Cyber security risk management is the process of protecting an organization's technology, data, and digital systems from different risks. This includes securing and attempting to protect internal business systems and digital assets from impending threats. In this field, solutions are not one-time fixes. Instead, they are ongoing processes. One must engage in ongoing development and refinement of the processes to keep up with ever-evolving threats and vulnerabilities.
What are The Key Elements Associated with Cyber Security Risk Management?
- Identification: Recognition of possible weaknesses and vulnerabilities within your systems
- Analysis: Assessing the characteristics and magnitude of the detected threats
- Assessment: Estimating and analyzing any potential damage or outcomes for your business
- Response: Carrying out the proper and actionable remediation
How is Effective Cyber Security Risk Management Achieved?
Effective cyber security risk management is best achieved through a collaborative ecosystem. Your IT team collaborates with:
- Security teams that provide continuous and real-time monitoring and response capabilities for threat perception and remedial measures
- Compliance officers who guarantee the meeting of the necessary legal and regulatory obligations
- Unit leaders of the business who offer comments and suggestions on the possible impacts of the operation(s)
- Financial experts who analyze the impacts of the operation(s) on a possible underlying loss
Is Your Cybersecurity Strategy Effectively Identifying and Mitigating Potential Threats?
Cyber security risk management serves the role of the immune system within the business. Just as our body defends against potential threats, your cyber security strategy should also guard against the following threats and preemptively mitigate them:
- Malware attacks
- Breach of sensitive information
- Phishing attempts
- Insider threats
- Vulnerabilities of the system
Therefore, it is of paramount importance to conduct periodic check-ups of the organization through the following:
- Comprehensive security audits
- Cybersecurity assessments
- Vulnerability scans
- Penetration testing
- Policy audit
Your cyber security risk management approaches must continuously upgrade and evolve to manage and mitigate continuously evolving and emerging threats. This will ensure that your organization will be able to continue to face and neutralize advanced threats and vulnerabilities while protecting and safeguarding your digital assets and infrastructure.
Digital Asset Protection
Digital assets can be defined as any files, data, or information that are stored electronically and hold value for your organization. Typically, these assets are crucial for the day-to-day operations of a business, thus necessitating the need to implement strong protective measures.
Digital Asset Examples:
Business Critical Data
This is the heartbeat of decision-making in a business. Think of balance sheets, hire rosters, and that top-secret product roadmap which sits at the center of almost every strategy meeting is your business critical data. Examples of business critical data are as follows:
- Financial records
- Strategic planning documents
- Research and development findings
- Market analysis reports
Customer Information
This is the information you save to learn who your customers are, where to reach them, and what products they might love next for your business. Examples of customer information are as follows:
- Personal identification details
- Payment information
- Purchase history
- Communication records
Intellectual Property
This covers the inventions, logos, formulas, and trade secrets that your business envisages up to stay one step ahead. Examples of Intellectual property are as follows:
- Patents and trademarks
- Product designs
- Source code
- Trade secrets
Operational Systems
Operational systems data are those without which, day-to-day service delivery would quickly falter for your organization. Think of vendor contracts, and scripted processes on which routine workflow depends constitutes your operational data. Examples of operational systems are as follows:
- Software applications
- Database systems
- Cloud services
- Network infrastructure
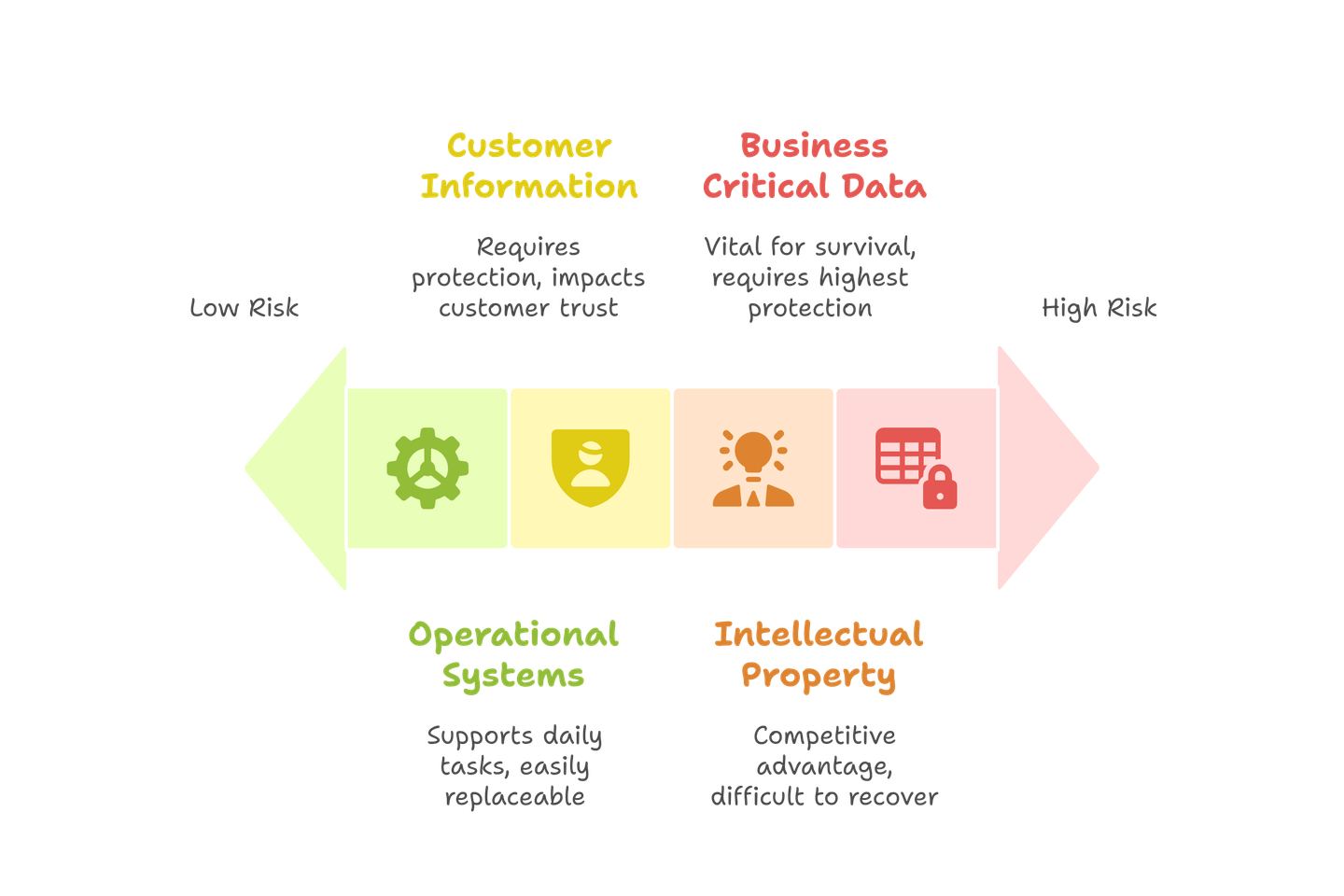
Digital assets are crucial in determining business value, competitive advantage, and operational continuity capabilities. A breach of sensitive information could result in notable financial and legal repercussions, and loss of customer trust. For example, exposed customer payment information compromises payment data security, which could invoke fraud, lawsuits, and a breach of customer trust. Therefore you need targeted cybersecurity and risk management assessments to uncover sector‑specific risks, specifically for financial service organizations.
Digital assets of your organization not only hold monetary value, but they could also be your company’s intellectual property that contains information on years of innovation and development. Therefore, to protect these digital assets, your organization needs to identify critical assets, align your security controls with your business goals, evaluate possible cyber vulnerabilities, and put in place adequate protective measures.
Best Practices For Cyber Security
The digital world is always changing. Therefore, you need to implement cyber security best practices to help protect your digital assets against new threats. By doing this, you safeguard your digital assets and maintain a strong cyber security stance. We have discussed some of the cyber security best practices for an optimal cyber security posture:
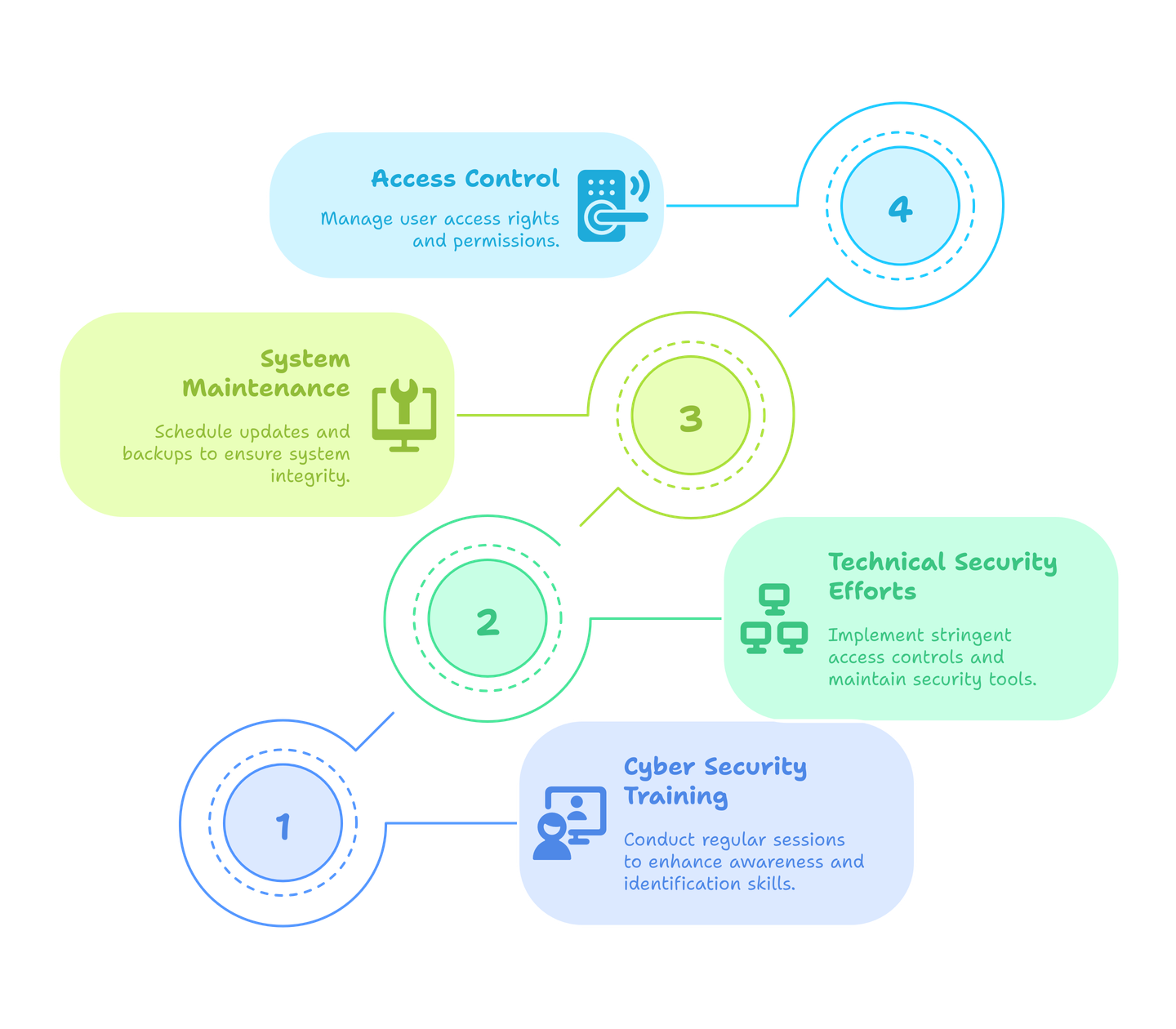
Cyber Security Training
Cyber security training teaches your employees to spot spoofed emails and unauthorized login attempts before they escalate. The mix of presentations, quirky quizzes, and twice-a-year drill attacks keep the team sharp and proves that everyone is following your company's digital asset security. Examples of cyber security training are as follows:
- Conduct regular security awareness sessions
- Phishing attempt identification training
- Enforce distinct security policies
- Incident response plan creation
- Knowledge testing through attack simulations
Technical Security Efforts
Technical security efforts consist of signature-based antivirus, disk-and-file encryption, and constant packet-sniffing on perimeter wires. These layers lock down entry points and make sure connection rules are obeyed by every logged-in user. These checks and balances will help ensure that your organization is following NIST compliance as part of your risk assessment framework. Examples of technical security efforts are as follows:
- Stringent Access Control
- Installation and maintenance of current antivirus programs
- Implementation of strong sanctions on the company’s passwords
- Encryption is used for sensitive information
- Network surveillance tool applications
System Maintenance
System maintenance demands that security updates and patches are regularly applied to applications, and logs are reviewed every night for unusual login times. Continuous diligence seals known flaws and quietly keeps networks running well, even when threat actors are hunting for open doors ensuring an optimal cyber risk management. Examples of security maintenance are as follows:
- Automated software update scheduling
- Regular security patching
- Critical data backups
- System log monitoring
- Regular assessment of system vulnerabilities
Access Control
Access control consists of implementing role-based control which confines each user to the resources necessary according to their job function. Regular access reviews, audits and a relentless commitment to the least-privilege principle, eliminates accounts who no longer require access to your organization’s resources. Examples of access control are as follows:
- Implement minimum access rights for users (least privilege)
- Control privileges and regularly audit access permissions
- Apply access control based on user profiles with defined roles and responsibilities
- Establish remote access for authenticated users only and secure it from any untrusted networks
Consider your organizational structure, industry compliance and standards, acceptable risk levels, and your specific organizational policies to tailor the aforementioned practices. You must make sure that you implement the above cyber security best practices and measures consistently and continuously upgrade and update them to properly handle and mitigate evolving threats.
Risk Management System
Your organization’s effectiveness in managing ever-evolving cyber security threats relies on using standard risk assessment frameworks. Key examples are NIST compliance (NIST Cyber Security Framework) and ISO/IEC 27001.
NIST Compliance Cybersecurity Framework (CSF)
NIST CSF has five core functions, which are as follows:
- Identify: Assess your organization’s systems, assets, and data
- Protect: Ensure critical services can be delivered with the implementation of appropriate safeguards
- Detect: Carry out predefined activities to identify cyber security events
- Respond: Remediation action regarding the cyber security incidents that were detected
- Recover: Restore impaired capabilities while maintaining resilience plans
ISO/IEC 27001
Specifically, ISO/IEC 27001 adds value to NIST by developing a standard for information security management systems (ISMS) that specifically focuses on risk management. This framework assists organizations to:
- Formulate systematic processes for controlling and protecting confidential corporate data
- Define and implement risk assessment procedures for evaluating and mitigating risks
- Create and enforce security measures
- Architect and execute appropriate information security controls
- Define processes for continual process enhancement and upgrading
The two risk assessment frameworks complement each other and provide a complete structure for a cyber security risk management system. While NIST CSF facilitates communication between technical and non-technical stakeholders, ISO 27001 helps define structures for implementing and sustaining security controls.
All organizations can modify and mold these frameworks as per their requirements. Components can be selected based on the organization’s level of risk it is willing to take and its overall business goals. These risk assessment frameworks are very flexible, which allows organizations of different sizes and across industries to easily tailor and implement them.
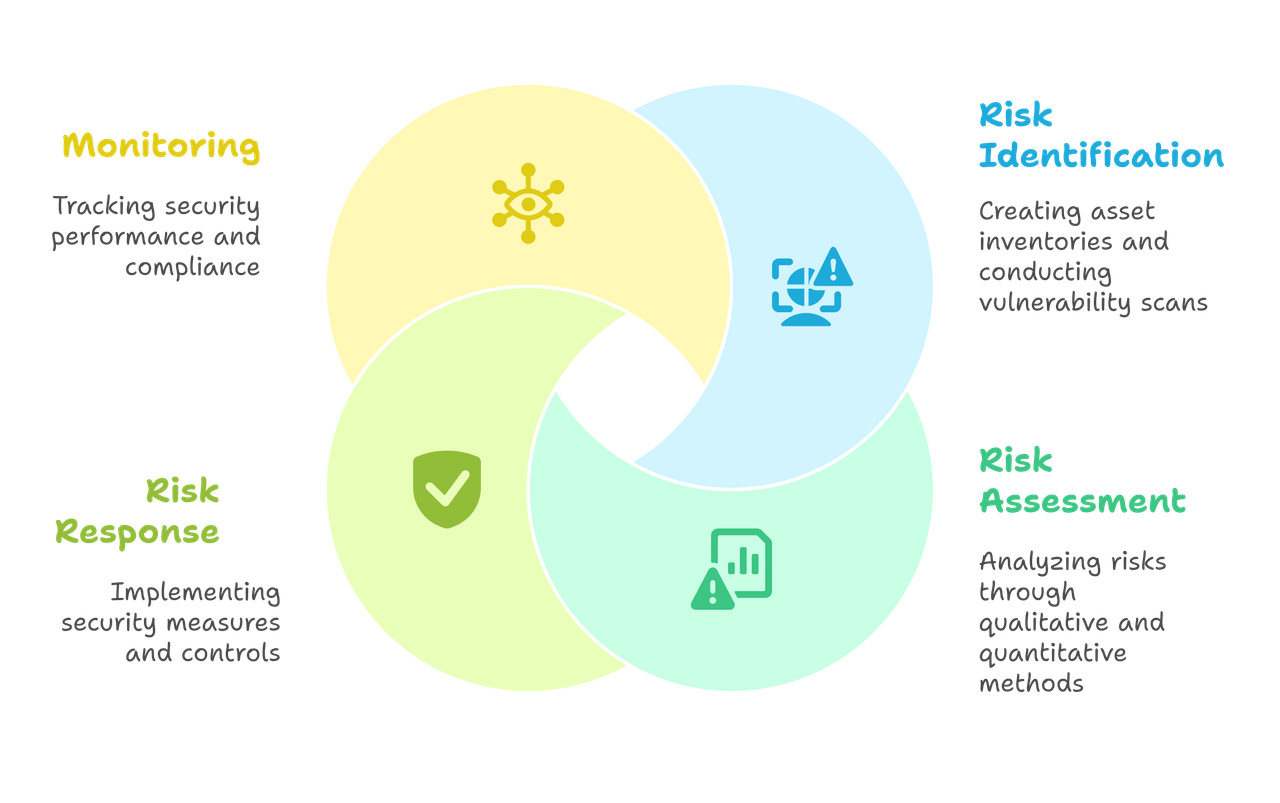
Cyber Risk Management Components
There are four core components of cyber security risk management, which work together to form a comprehensive cyber security risk assessment framework.
Risk Identification
- Creation and maintenance of an asset inventory and classification
- Conducting vulnerability scans and assessments
- Collecting threat intelligence
- Analyzing the effects on business operations
Risk Assessment
- Qualitative Analysis
- Risk rating based on severity levels (low, medium, high)
- Quantitative Analysis
- Applying numerical calculations with metrics such as
- Annual Loss Expectancy (ALE)
- Single Loss Expectancy (SLE)
- Annual Rate of Occurrence (ARO)
- Applying numerical calculations with metrics such as
Risk Response
- Access control systems - Implement access control systems, so that appropriate access to the right resources at the right time can be ensured.
- Multi-factor authentication – Every user who connects remotely must provide a second form of identification-typically a mobile token-because multi-factor authentication is now mandatory.
- Cyber insurance coverage – Organization purchased a cyber insurance policy that will cover legal fees, notification costs, and ransom payments should a breach or ransomware event materialize.
- Encryption protocols – Sensitive customer data is encrypted both at rest in storage and in transit across networks, closing the window where interception could occur.
- Next-generation firewalls - Next-generation firewalls were installed last quarter; they continuously inspect and filter inbound and outbound traffic for suspicious patterns.
- Regular software patching – System administrators apply security patches to operating systems and third-party applications on a monthly cadence, ensuring known weaknesses are addressed without delay.
- Employee training programs - Cyber security training and awareness programs are conducted by your organization, for keeping your team updates about how to handle latest threats.
- Risk acceptance for low-impact threats - Low impact threats such as weak passwords, can be accepted and ignored as they do not impact your digital asset security strategy.
Monitoring
- Real-time monitoring of security – A Security Information and Event Management platform that ingests all available traffic and log data to flag abnormal behavior the moment it appears.
- Automated detection of threats – Simulated cyber-attacks , staged every quarter by certified ethical hackers to probe the deployment for weaknesses that attackers might later target.
- Tracking performance metrics – Threat-triage dashboards display key indicators: counts of enumerated threats, clock-hours until patches land, and elapsed time between detection alert and incident wrap-up.
- Evaluate the effectiveness of controls - Regularly audit, review and update your security controls for optimal risk management.
- Verification of compliance status – Compliance staff continuously audit the shifting language of GDPR, HIPAA and other regulatory frameworks, revising training modules, access controls, and data-handling checklists to avoid regulatory missteps.
The cyber risk management strategy of your organization must be continuously updated with new technologies, threats, and shifting compliance requirements. Performing regular security evaluations arms you with the means of discovering gaps within your defense mechanisms. Therefore, your organization must set up automated systems. These systems will help with ongoing monitoring and threat detection, ensuring a strong security posture. Additionally, these systems are capable of alerting you instantly, creating comprehensive reports, and effectively tracking your security metrics.
Conclusion on Risk Assessment Framework
Cybersecurity risk management is imperative for organizations to ensure operational resiliency and business continuity. Every organization with digital assets is vulnerable to impending threats, which makes preemptive protection a necessity. Following are some of the pertinent actions that you can take to strengthen your security posture:
- Evaluate the effectiveness of your organization's cyber security risk management practices.
- Document security gaps within your security control mechanisms.
- Implement standardized frameworks such as NIST CSF or ISO 27001, tailored to your organization's needs.
- Build your organization's systems in a way that makes them periodically reassess their security measures.
- Establish employee training and awareness programs, building on foundational elements of cyber security risk management frameworks.
The threat perception in information technology is morphing rapidly. Furthermore, there is a sharp increase in the costs associated with identity fraud and hacking incidents. The saying, “An ounce of prevention is better than a pound of cure” stands resolute for any organization. What you do today in taking action will shape the future vulnerability of your organization's digital assets.
Free Cybersecurity Risk Assessment Template
Now that you've taken the first step in understanding the importance of cybersecurity risk management and digital asset protection. Take the next step and download our free Cybersecurity Assessment Template to identify potential vulnerabilities and create a tailored plan to safeguard your organization’s digital assets. Start building your effective cyber security risk management program now.