What is Identity Lifecycle Management?
Identity and Access Management (IAM) is a continuous process that requires frequent changes for all critical applications, user attributes, cloud applications, and more for the entire life of those assets in your organization.
It can also include managing privileged accounts, defining role-based access control, and access review to prevent unauthorized access.
Identity Governance is traditionally a collection of technologies and business processes, employed to create and manage the levels of access in order to mitigate security risks and increase user productivity with business resources.
With Modern IAM systems, Identity Governance And Administration of all lifecycles can be accomplished with a single software solution.
What is Provisioning?
Provisioning is a term used for constructing and providing a network, with the tools needed to produce new services for end-users, within an organization.
Provisioning is part of every IAM lifecycle and contains its own identity and access provisioning lifecycle steps.
On-boarding new employees and machine identities should be governed by the principle of least privilege, or the minimum access necessary for them to carry out their job functions.
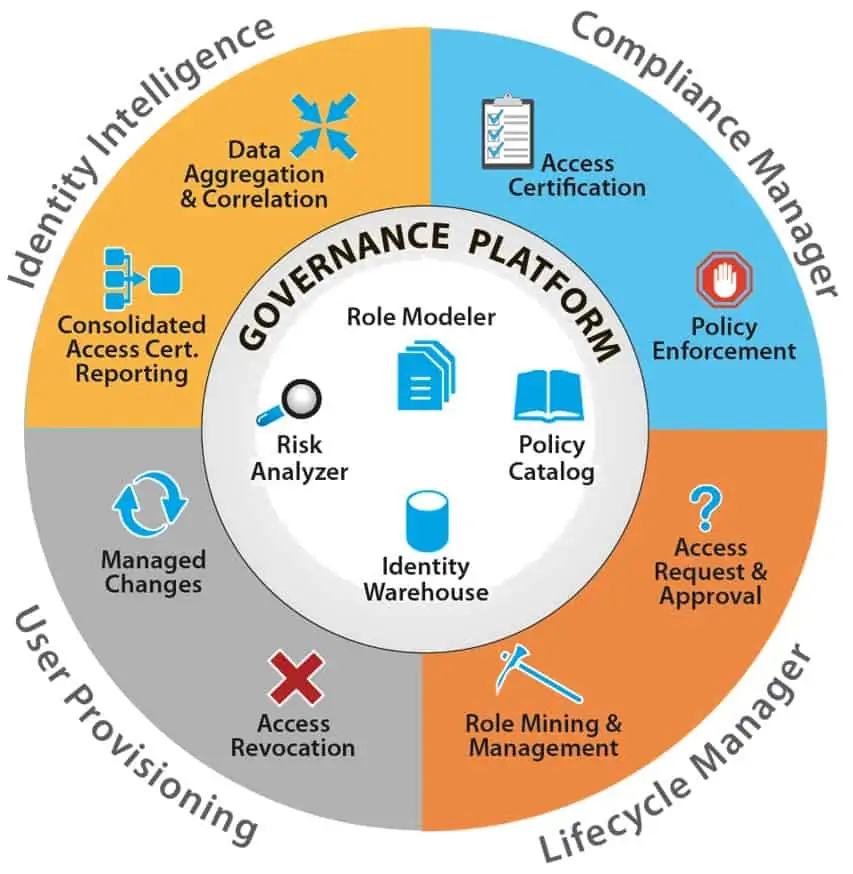
Elements
Every network consists of two key players: humans and machines. Humans take on login credentials to identify themselves. Machines identify and authenticate themselves, but they don’t take on user names and passwords. Machines instead, utilize certificates and keys.
IAM systems should reduce the time IT spends on-boarding and off-boarding users, managing job role changes, and ensuring every digital identity is accounted for, by automating routine processes, while providing end-users with a seamless experience.
An ideal solution should provision, make mid-lifecycle changes to, and deprovision accounts for users, or listen for these activities from your existing HR systems.
Asset Lifecycle Management
An IT asset is a piece of software or hardware within an IT environment. Tracking IT assets with an appropriate management system is a critical component to the financial success of an organization.
Identity and Access Management Systems not only manage the identities within an organization, but also manage access to all "assets", or in other words, they also manage all resources available within an organization.
IAM systems do this by looking at various resources within an organization, and the resource lifecycle stages.
According to Gartner lifecycle management practices are required to improve the return on investment for IT assets, avoid internal and external audit consequences, and adopt future technology.
A Modern Identity Management Solution
A well-equipped IAM system should provide appropriate resource management tools to system administrators, allowing for easy application on-boarding, off-boarding, and modification.
Ideally, each application should be able to be customized individually with connecting entitlements, which are used to grant access requests for a set of access permissions within that application, which can be added, removed, and disabled as needed within the organization.
In addition Roles can be used to group applications and entitlements, and then assign to a user, according to her access needs.
One of the limitations of traditional solutions like Active Directory is the limitation of not being able to control users' access to applications outside of your environment.
As a user's job description and title change, applications should be automatically deprovisioned, simply by revoking access to a Role, and on the flip side, assigning a new appropriate Role, will automatically provision the new set of applications and entitlements within the new Role.
Identity Management Lifecycle Example
A user has been promoted to "Marketing Manager". She will now be assigned the Role "Marketing Manager", and with that new Role assignment, she will have access to the particular set of resources, which are attached to that Role. Some resources may be applications with specific entitlements within those applications; I.E. WordPress, and the WordPress Administrator Entitlement.
When changes like this occur, a modern solution like IDHub can trigger an automated sequence of actions to fully on-board, make changes to, or off-board a user, as well as set up their permissions, settings, and memberships, within apps, fully controlling User Profile Management.
Role Identity Management
Roles are a form of digital identity, associated with permissions to specific applications, in the form of entitlements, which define what the member of that Role can or cannot do with their access.
As users within an organization change job descriptions, they may require access to new resources, and may no longer need access to old resources. When using Roles, changing departments and approving or revoking access, becomes a breeze.
Create automatic workflows, triggered by department and Role changes, provisioning and deprovisioning access to resources automatically.
Certifications can be created to identify access discrepancies, and through the Reconciliation process, revoking access to Roles and entitlements is painless.
Identity Lifecycle Management Phases
Below is a good representation of the full Identity Lifecycle process:
- New user enters the organization
- Digital identity created
- Single Sign On multi-factor Authentication process is setup.
- User is assigned a Role in the organization
- Accounts are created for the systems and Applications the user will need access to
- Access is Certified to applications periodically
- User Requests Access to resources when needed
- User's Role changes in the organization
- New application accounts are created and Provisioned
- Discontinued applications are deprovisioned, through Reconciliation
- User leaves organization
- User access is removed to all accounts
Application Lifecycle Management
Below is a good representation of the full Application Lifecycle process:
- Application Adoption
- Application Onboarding
- Entitlement Management
- Linking to Roles
- Assigning Approvers
- Provisioning Users
- Certification
- Reconciliation
- Deprovisioning Users
- Deprovisioning Applications
- Removing Applications from Account
Conclusion
Identity Lifecycle Management isn’t just about handling accounts—it’s about maintaining control. When users change roles, leave the company, or shift between systems, their access needs to follow. ILM keeps that in check.
It reduces risk by cutting off unnecessary access, supports compliance by keeping a record of who had access to what and when, and saves time through automation.
In short: ILM helps you stay organized, secure, and accountable—without wasting resources or leaving gaps.